| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Microsoft? Has Its Own Linux?? |
|
by Paul Arnote (parnote) As frequently as assaults on your privacy happen, I figured I probably needed to make something about them a regular part of the Short Topix column. I seem to be reporting on privacy intrusions on a monthly basis here, so we might as well have a regular place to put them. So, below is the inaugural appearance of "The War On Your Privacy" portion of this monthly column. To better define the scope of what I'll be covering in this section of my monthly Short Topix column, it'll be pretty much restricted to data breaches and other intrusions on your privacy. Other news items announcing ways to protect your privacy will, when reported on, be given their own section of Short Topix as I've always done. The War On Your Privacy Monthly Update  AN ARTICLE ON TECHRADAR PRO reports that 700 million LinkedIn records have been scraped from the career networking site, and are being offered for sale on an underground hacking forum. This follows two months after 500 million records from the career networking site were sold off in a similar manner. The latest LinkedIn breach was initially reported by the VPN review site, PrivacySharks. LinkedIn is still investigating the issue, but their initial analysis points to only information from public-facing pages being included, and that no private information of users was compromised.
Tom Burt, Microsoft Corporate Vice President of Customer Security & Trust, reported in Excerpted from Burt's written testimony: Traditionally, secrecy was the exception. In recent years, law enforcement has turned that exception on its head, developing a practice of reflexively asking to keep even routine investigations secret. Providers, like Microsoft, regularly receive boilerplate secrecy orders unsupported by any meaningful legal or factual analysis. Microsoft does not simply comply with such demands without question. We review them closely to protect our customers' interests. Some of the demands Microsoft received were legally deficient and we did not comply. In other cases, we have challenged -- through negotiation or litigation -- the orders. This includes secrecy orders approved by courts where the account holder was not a target of the investigation but a victim; where the investigation related to just one email account belonging to a large, reputable organization -- a company, government, or school -- and there was no allegation that the organization itself or its leadership was suspected of wrongdoing; where the government was engaged in discovery negotiations with an organization under investigation, and then secretly demanded the very same records from us to evade a dispute over privilege and the extent of discovery; and even where the owner of the target account consented to the search. You can read Burt's full written testimony before the committee hearing here (PDF). It is QUITE eye-popping. And you wonder why people don't trust their own governments to do the right thing. A JANUARY ATTACK ON MICROSOFT EXCHANGE SERVERS that spanned into February and early March of this year, has been tracked to a Chinese government-sponsored hacking group by U.S. officials and several U.S. allies, according to a report from the Associated Press. According to a previous article in March from the AP, "the hackers grabbed data, stole credentials or explored inside networks and left backdoors at universities, defense contractors, law firms and infectious-disease research centers." Concerns are especially high among those worried about intellectual property theft, hospitals, financial institutions and managed service providers who host multiple company networks. WWII Gaihōzu (Japanese Imperial Maps) Rediscovered 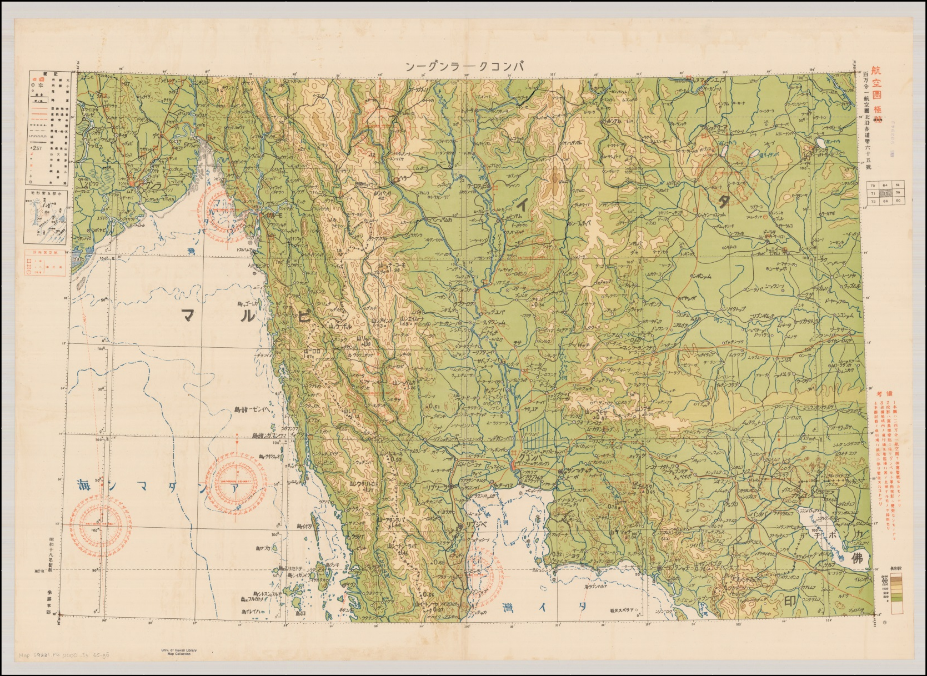 After the end of World War II, American (and other Allied forces) captured thousands of military maps from the Imperial Japanese armed forces. These maps weren't just of Japan, either. These maps were from all over Asia, including Korea, China, USSR, Burma, Thailand, and many of the Pacific Islands. Realizing their value, the U.S. Army sent these maps ... called gaihōzu ... back to the U.S. for safe keeping. But, because of their intelligence and tactical value, it was decided that all of these maps shouldn't be stored all in one place. So, they sent them to libraries scattered all around the U.S., and there they sat, gathering dust and forgotten. That is, until a former Stanford graduate student working on a Master's dissertation about the ancient Chinese Han dynasty started asking around about some rumored maps of old Asia, according to an article on National Geographic. Her search led to their rediscovery. Sometimes, especially early on, Japanese cartographers would use and appropriate maps made by the local indiginous people. But, as time went on, they discovered the maps weren't detailed enough to suit their needs. So, Japan sent out teams of surveyors to create more detailed maps. The other countries and regions these surveyors were mapping weren't always that "thrilled" about the presence of the Japanese surveyors. In fact, at one point, an entire Japanese surveyor team simply "disappeared." These detailed maps now hold a lot of historical significance. It offers a fascinating window on the history of Asia, as well as World War II. You can view collections of these historical maps by visiting the Gaihozu Digital Archive, and the Gaihozu: Japanese Imperial maps collection at the Stanford library. Microsoft? Has Its Own Linux??  Are you sitting down? If not, take a moment, find a chair, and plant your backside in it. I wouldn't want anyone falling out and injuring themselves. Microsoft has its own version of Linux, called CBL-Mariner. The "CBL" stands for Common Base Linux. There. I said it. It has actually happened. Are you still vertical? Do you need to catch your breath? After years of declaring Linux a cancer and doing everything in its power to eliminate Linux from the computing landscape, Microsoft has its own version of Linux. [ GASP!!!! ] Don't expect to find it too useful, though. CBL-Mariner is a lightweight Linux server. In fact, no ISO currently exists of CBL-Mariner, but you can download the source files from GitHub and build it yourself. To build it, you have to be running Ubuntu 18.04, though (although there are reports of it being successfully built on even more recent versions of Ubuntu). Plan on the build process taking you just under an hour to complete. There is no desktop environment. Just a plain old command line. It's geared towards powering "the cloud." Microsoft released it without any fanfare. It just took people quite a while to notice it. Built for its own internal use, CBL-Mariner's first commit on GitHub was in July 2020. It literally took a full year for most people to sit up and take notice. Don't get your hopes up, though, as TechRepublic's Jack Wallen did. No, Microsoft isn't rebasing Windows on Linux (although that should have happened YEARS ago). ZDNet's Steven J. Vaughan-Nichols also seems quite giddy about CBL-Mariner. Vaughan-Nichols gives a good summary of just what CBL-Mariner's role is. Still, for those of us who have been around computing for a significant amount of time, this revelation is shocking and unexpected. Miracles will never cease! Get The FLoC Outta Here!  If you haven't heard by now, Google is supposed to be moving away from the dreaded cookies that identify individual users as they move about the internet. Google plans to replace cookies with FLoC, which stands for "Federated Learning of Cohorts." Here's what EFF (Electronic Frontier Foundation) says to explain FLoC: FLoC runs in your browser. It uses your browsing history from the past week to assign you to a group with other "similar" people around the world. Each group receives a label, called a FLoC ID, which is supposed to capture meaningful information about your habits and interests. FLoC then displays this label to everyone you interact with on the web. This makes it easier to identify you with browser fingerprinting, and it gives trackers a head start on profiling you.  Google is now trialing FLoC on about 0.5% of random Google Chrome users. To see if you are one of the "lucky" Google guinea pigs, under the hamburger menu, go to Settings > Privacy and security > Privacy sandbox. If you don't see this item, you are not a part of Google's Frankenlab experiments. Simply turn the slider in the upper right corner to the OFF position to opt out of being one of Google's test subjects. Don't think, however, that you cannot or will not be added to further rounds of testing later, so check back often. Once Google goes "live" with FLoCs and lets its monster out of its cage, don't hold your breath about being able to opt out of using the new tracking technology. While Google claims that FLoC will protect user privacy far better than cookies, there are many critics of the use of FLoCs. They say that in many ways, they are worse than cookies. Leave it to Google to come up with something worse than cookies that serves their [greedy] pursuit of advertising dollars. Thankfully, you are not alone in your concerns. The EFF is leading the charge against FLoCs, along with most other "technologies" that track users and compromise their privacy. They even have a special website, named Am I FLoCed?, that will check to see if you are being tracked by the Google FLoC of geese.  Google Chrome  Firefox If you connect to the Am I FLoCed? website in Chrome, you will see the top message above displayed in Chrome. Out of curiosity, I tried the website in Firefox, and I got the message in the bottom image above displayed. The website goes on to give a good, easy-to-understand explanation of the new FLoCs, and how they might compromise your privacy. Google is trialing FLoC **ONLY** in Google Chrome, and it has not spilled over to any other browser, including any of the Chromium variants (Brave, Edge, Chromium, etc.). No other browser maker (like Mozilla) has come out in support of Google's new FLoC tracking. If you ever needed a/another reason to hate Google and/or ditch Google Chrome, you might want to pay attention. FLoC represents a direct assault on your privacy, spearheaded by Google. If this isn't enough to persuade you of Google's evil intent, then nothing ever will and you deserve what you get. Dropbox Adds New Features, Capabilities  Citing the explosion in WFH (working from home) over the past 15 months brought on by the COVID pandemic, the Dropbox team has added some new features. Most of these new features are available to both paid and free Dropbox users, albeit only on the Dropbox web page, and (sadly) not from your Dropbox directory on your computer.  Still, here are some of the new features you are apt to see in Dropbox. First, Dropbox will allow you to convert between JPG, PNG and PDF file formats without having to leave the Dropbox site, and without having to first download the file and then manually convert them on your computer, before re-uploading them to Dropbox. There are plans to add video file conversion, as well, according to the Dropbox folks. They have also dramatically improved camera uploads to Dropbox, making it easier to use Dropbox to share images and files with family and friends. The new Dropbox Passwords feature allows you to store, sync and share your passwords between devices. It also contains support for debit and credit card numbers. The "Suggested Folders" feature helps users add and share the right content with the right people, but is available only to those Dropbox users with a paid subscription. Personally, some of these new features sound pretty enticing and will be welcomed by many Dropbox users. However, some of these new features sound like a security nightmare in the making. I, for one, would be hesitant to store my passwords and debit/credit card numbers in my Dropbox account. The risk, in the event of a data breach, is just too great. Now ... if only Dropbox would increase the storage space allotted to Basic (free) users beyond the 2GiB of space that they've offered since Day One. Google Maps Leads Users To Potentially Fatal Hiking Trail  Ben Nevis is the highest mountain in Scotland, standing 4,412 feet (1,345 meters) tall. As mountains go, it's no Mt. Everest, but it's still fairly tall. And, as with many mountains, it can be deadly to hikers and mountaineers. The United Kingdom conservation charity John Muir Trust and Mountaineering Scotland, the national representative body for mountaineering, hillwalking, climbing, and snow sports touring, has specifically warned that a route provided on Google Maps, which leads hikers to a parking lot at the head of Glen Nevis, could be putting people at risk. Google Maps can proceed to display a dotted line to show a path to the top of the mountain, one which would be difficult for even the most experienced mountaineer to follow. Heather Morning, Mountaineering Scotland's Mountain Safety Adviser, said in a statement released by the conservation charity, "For those new to hill walking, it would seem perfectly logical to check out Google Maps for information on how to get to your chosen mountain. But when you input Ben Nevis and click on the ‘car' icon, up pops a map of your route, taking you to the car park at the head of Glen Nevis, followed by a dotted line appearing to show a route to the summit." Morning added, "Even the most experienced mountaineer would have difficulty following this route. The line goes through very steep, rocky, and pathless terrain where even in good visibility it would be challenging to find a safe line. Add in low cloud and rain and the suggested Google line is potentially fatal." Since the criticism, Google has changed the driving instructions to get to Ben Nevis to take visitors to the mountain's visitor center, where they can discuss with park personnel the best route to take to climb or hike Scotland's highest mountain. PCLinuxOS Short Topix Roundup  WHO BETTER TO DESIGN NEW AI COMPUTER CHIPS THAN AI? An article at WIRED highlights just that approach. Computer chips, often smaller than a fingernail, contain billions of components. Each and every decision made on the arrangement of those components has the potential to affect the speed and efficiency of the resulting chip. So, to place a billion transistors on a small computer chip, who better to do it than AI? While attempts to have computers help design computer chips in the past have fallen short, new advances in AI have made such matters within reach. Remember when you were told that the data being collected from your cell phone was being anonymized? Well, you were being lied to, even if it's a lie by omission. According to an article on Vice, they are FAILING TO TELL YOU ABOUT AN ENTIRE INDUSTRY THAT OPERATES IN THE SHADOWS, and who's sole business model is to collect the unique cell phone ID and mobile advertising IDs produced by various apps (called MAIDs), and linking them to personally identifiable information. The article, to say the least, is eye opening and quite disturbing. According to an article that appeared on Reuters, THE GERMAN DATA PROTECTION OFFICER GAVE MINISTRIES UNTIL THE END OF THE YEAR TO CLOSE THEIR FACEBOOK PAGES, after discovering that Facebook had failed to comply with German and European Union privacy regulations. Commissioner Ulrich Kelber said it was impossible to run a fan page in such a way that followers' personal data was not transmitted to the United States. Under EU law, personal data can only leave the EU for a jurisdiction with equivalently strict data protection rules, something that is not the case for the United States. An article on Lifehacker LISTS SOME OF THE MORE NOTABLE CHANGES IN FIREFOX 90. Those include the ability to store credit card numbers, SmartBlock 2.0 working with Facebook to block the tracking Firefox users across the web, and the removal of the ability to download from FTP servers via a FTP. JustTheNews published an article describing how Erik Finman, the youngest Bitcoin millionaire, has CREATED THE FREEDOM PHONE, WHICH PROTECTS USERS' PRIVACY WHILE PROMOTING FREE SPEECH AND PREVENTING CENSORSHIP. Built on top of a version of Android that has been "de-Googled," it even has its own app store. Privacy activist Edward Snowden, in an interview with The Guardian, warned that no mobile phone is safe, considering the revelations about the clients of NSO. He has CALLED FOR A SPYWARE TRADE BAN in the wake of the NSO revelations. NSO Group manufactures and sells to governments advanced spyware, branded as Pegasus, that can secretly infect a mobile phone and harvest its information. Emails, texts, contact books, location data, photos and videos can all be extracted, and a phone's microphone and camera can be activated to covertly record the user. Now this one is a bit funny. A lot of attention was being paid to Amazon founder and former CEO Jeff Bezos as he made his 10 minute flight into space aboard Blue Origin's inaugural crewed flight. But the best part of the story (it was widely reported, and I saw it on Gizmodo and Reuters) may have been from Oliver Daemen, the 18 year old from the Netherlands. He not only MADE HISTORY AS THE YOUNGEST PERSON TO GO INTO SPACE, BUT HE ALSO MADE HEADLINES FOR SOME "SMALL TALK" HE MADE WITH BEZOS. He told Bezos that he had never bought anything off of Amazon. Bezos' response was as priceless as it was true: "Oh, wow, it's a long time ago I heard someone say that." Additional history was made on the flight, with 82 year old female pilot Wally Funk becoming the oldest person to fly into space. |