| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Snowflake Makes It Easy For Anyone to Fight Censorship |
|
by Cooper Quintin  Tor, the onion router, remains one of the most effective censorship circumvention technologies. Millions of people use the Tor network every day to access the internet without fear of surveillance and censorship. Most people get on the Tor network by downloading the Tor Browser and connecting to a relay. But some countries, such as Iran and Russia, block direct access to the Tor network. In those countries people have to use what are known as "Tor Bridges" to circumvent national firewalls. Tens of thousands of people use bridges regularly to circumvent censorship and national or regional restrictions. 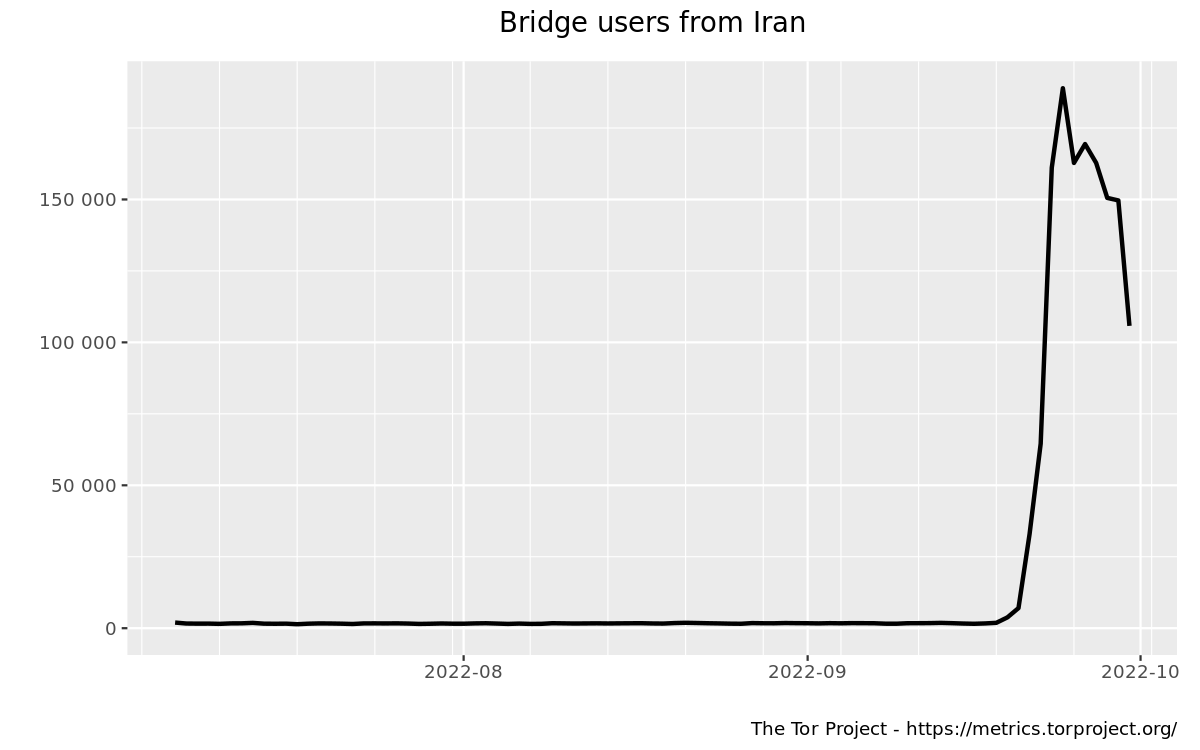 The number of bridge users in Iran grew exponentially in the last week of September 2022. Of course, ISPs in countries where Tor is banned are constantly trying to find the IP addresses of bridges and block them to prevent people from accessing Tor. Bridge connections can also be identified (or "fingerprinted") as connections to the Tor network by an ISP using deep packet inspection. To deal with this, Tor has a clever solution called "pluggable transports." Pluggable transports disguise your Tor connection as ordinary traffic to a well-known web service such as Google or Skype, and smuggles your Tor connection inside of the seemingly innocuous traffic. In the past, running a pluggable transport was difficult to set up, requiring a server and a good deal of time and technical knowledge. Now, thanks to a new pluggable transport called "Snowflake," anyone can run a pluggable transport in their browser with just a couple of clicks and help people all over the world access the unrestricted internet. If you are ready to get started you can install the Snowflake browser add on, or if you run a server you can run the standalone version written in Go.  The user interface for the Snowflake browser extension  Logs from a standalone snowflake instance running on a server How Snowflake Works Snowflake is composed of three components: volunteers running Snowflake proxies, Tor users (or clients) that want to connect to the internet, and a broker that delivers Snowflake proxies to clients. Volunteers willing to help users on censored networks can help by spinning up short-lived proxies on their regular browsers. When you enable Snowflake, your browser will contact the broker and let it know that you are ready to accept peer-to-peer connections from people seeking to access Tor. Then clients who are on a restricted network can contact the broker and ask for a proxy, the broker will eventually hand them your IP address, and then the client will make a direct connection to your computer using WebRTC (the same technology which is used by Zoom, Skype, and any other peer-to-peer web connection.) Your computer will then forward traffic from the client to the Tor network. 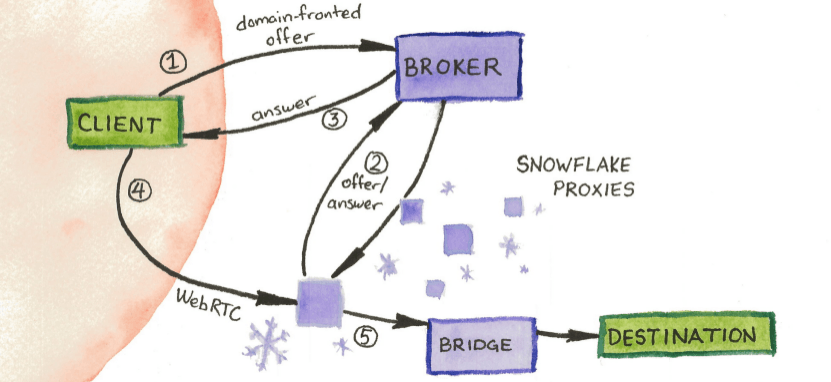 A visual diagram of Snowflake The obvious weak point here is the broker server. Why couldn't a country just block the broker IP since it is well-known? The answer is a technique called "domain fronting." The details of domain fronting can be found elsewhere, but in brief, domain fronting lets the client make a request that looks like an ordinary web request for google.com, and thanks to HTTPS the request is able to hide its "Host" header which is actually for an arbitrary web service hosted on Google's cloud. In this case, that service is the Snowflake broker. To block Snowflake, a network or country would have to block all of Google or every IP address outside of the network, essentially a complete internet shutdown. Of course, countries have repeatedly shown their willingness to do exactly that, but it's a much higher price to pay than simply blocking Tor. The security concerns for the Snowflake proxy operator are minimal. The Snowflake client will not be able to interact with your computer in any way or observe your network traffic, and you will not be able to see their traffic. From the perspective of your ISP it will look like you are connecting to a Tor bridge, which if you are running a Snowflake proxy should be legal and unrestricted in your country. There is no more risk running a Snowflake proxy than running Tor browser. Snowflake means that everyone can help people exercise their freedom of expression anywhere in the world, and it takes no technical knowledge to run, so if you are in an unrestricted country (such as in North America or most of Europe) go run one now! And if you are in a restricted network consider using Snowflake to circumvent censorship and access the internet. More technical readers are encouraged to read the Snowflake Technical Overview and the project page for more technical details. For other discussions about Snowflake, please visit the Tor Forum and follow up the Snowflake tag. |



