| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Root Out Root Kits With rkhunter
|
|
by Paul Arnote (parnote) Recent headlines in the news spell out the promotion of computer security and computer spying to the forefront of global consciousness. Edward Snowden. NSA. GCHQ. Google aligning with ALEC. Microsoft intercepting Skype conversations. Microsoft having an "open door" backdoor for the NSA. Canadian spies targeting agricultural interests in Brazil. Chinese hackers stealing defense secrets. There seems to be no end to the spying allegations and revelations in sight. It became quickly apparent with Avast Antivirus announcing a false positive over the September magazine cover graphic on the magazine's October website (hereafter referred to as the Avast Fiasco), that many users are still concerned about malicious software under Linux. But let's set one thing straight, right up front: there are no viruses "in the wild" for Linux. However, this doesn't mean that Linux is immune from malicious software. Linux, as well as every other OS, is still vulnerable to a variety of malicious software known as rootkits. It also illustrates -- perfectly -- why you should never install software from outside the official PCLinuxOS repository. What is a rootkit? Well, basically, it's a form of malicious software that hides out on your computer that is designed to obtain root level access to a computer. It does this while attempting to hide and prevent detection by antivirus software. Rootkits can be installed on your computer via a "trojan horse" method, where the software is surreptitiously installed in a "drive-by" fashion. These rootkits can infest your system while browsing nefarious websites, opening suspicious email attachments, or by engaging in password cracking activities. Once installed, they can wreak havoc on a computer. They may stealthily "phone home" with sensitive and private data. Or, they may simply pave the way for other bundled software payloads to steal email contacts, passwords, PIN numbers, credit card information, or conduct activities on your computer that you did not authorize. Today's rootkits don't work so much to elevate privileges to root level access, but instead work mostly to help make the bundled payload software undetectable. So how do you protect yourself, your computer and your data? The obvious answer is to not surf/browse nefarious websites, open suspicious email attachments, or attempt to crack passwords. Fortunately, the PCLinuxOS repository also includes one of the most popular rootkit detection programs: Root Kit Hunter, also more commonly referred to as rkhunter. It is a command line utility that is fairly easy for anyone to run, provided they have root access. It can detect, but not remove, rootkits. More on that later.To get started with rkhunter, you will need to install it from the PCLinuxOS repository, via Synaptic. Be sure to fully update your system while you've got Synaptic open (it's a very, very bad practice to do selective updates, which will lead to you eventually borking your system). Running rkhunter 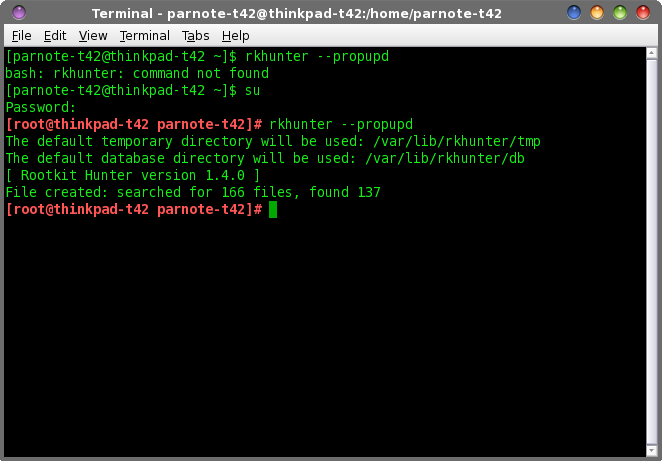 Before you get started with rkhunter, you will first need to update its database. First, open a terminal window (any terminal window will work, so choose your favorite). In the above graphic, notice how I first attempted to run rkhunter as a normal user. I was met with a "bash: rkhunter: command not found" error message. Since you can only run rkhunter as the root user, you will need to su to the root user, supplying your root user password when prompted. Once you have root access, enter the following: rkhunter --propupd Now, sit back and wait while rkhunter downloads and updates its database. There are quite a few options you can choose when running rkhunter. Here is a list of them all, with a brief description of what each do:
Usage: rkhunter {--check | --unlock | --update | --versioncheck |
--propupd [{filename | directory | package name},...] |
--list [{tests | {lang | languages} | rootkits | perl | propfiles}] |
--config-check | --version | --help} [options]
Current options are:
--append-log Append to the logfile, do not overwrite
--bindir <directory>... Use the specified command directories
-c, --check Check the local system
-C, --config-check Check the configuration file(s), then exit
--cs2, --color-set2 Use the second color set for output
--configfile <file> Use the specified configuration file
--cronjob Run as a cron job
(implies -c, --sk and --nocolors options)
--dbdir <directory> Use the specified database directory
--debug Debug mode
(Do not use unless asked to do so)
--disable <test>[,<test>...] Disable specific tests
(Default is to disable no tests)
--display-logfile Display the logfile at the end
--enable <test>[,<test>...] Enable specific tests
(Default is to enable all tests)
--hash {MD5 | SHA1 | SHA224 | SHA256 | SHA384 | SHA512 |
NONE | <command>} Use the specified file hash function
(Default is SHA1, then MD5)
-h, --help Display this help menu, then exit
--lang, --language <language> Specify the language to use
(Default is English)
--list [tests | languages | List the available test names, languages,
rootkits | perl | rootkit names, perl module status
propfiles] or file properties database, then exit
-l, --logfile [file] Write to a logfile
(Default is /var/log/rkhunter.log)
--noappend-log Do not append to the logfile, overwrite it
--nocf Do not use the configuration file entries
for disabled tests (only valid with --disable)
--nocolors Use black and white output
--nolog Do not write to a logfile
--nomow, --no-mail-on-warning Do not send a message if warnings occur
--ns, --nosummary Do not show the summary of check results
--novl, --no-verbose-logging No verbose logging
--pkgmgr {RPM | DPKG | BSD | Use the specified package manager to obtain or
SOLARIS | NONE} verify file property values. (Default is NONE)
--propupd [file | directory | Update the entire file properties database,
package]... or just for the specified entries
-q, --quiet Quiet mode (no output at all)
--rwo, --report-warnings-only Show only warning messages
--sk, --skip-keypress Don't wait for a keypress after each test
--summary Show the summary of system check results
(This is the default)
--syslog [facility.priority] Log the check start and finish times to syslog
(Default level is authpriv.notice)
--tmpdir <directory> Use the specified temporary directory
--unlock Unlock (remove) the lock file
--update Check for updates to database files
--vl, --verbose-logging Use verbose logging (on by default)
-V, --version Display the version number, then exit
--versioncheck Check for latest version of program
-x, --autox Automatically detect if X is in use
-X, --no-autox Do not automatically detect if X is in use
While the number of options may be overwhelming for some users, we can reduce them down to just those that are more commonly used. 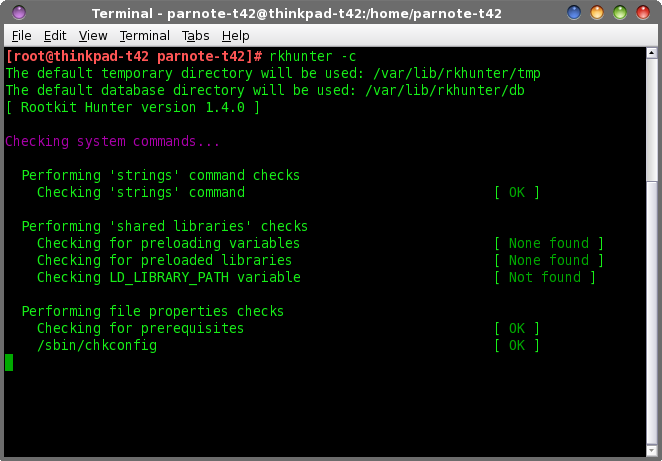 To begin, you will want to simply run rkhunter. Enter rkhunter -c on the root command line. Similar to when we performed the initial update to rkhunter, sit back and watch as rkhunter performs its chores. Don't worry ... you won't be sitting there long enough for cobwebs to form. The first time I ran rkhunter on my computer, it took just a little over three minutes to complete. But, using the default command line above, it will ask for you to press the Enter key periodically as it performs its various tests. If you prefer it to not wait on your user input, change the command to rkhunter --sk -c. The --sk command line switch skips the user input (pressing the Enter key), and will allow rkhunter to move straight from one task to the next. However, both commands will still produce the same output in the terminal window. Below are some random screenshots as rkhunter goes through the process: 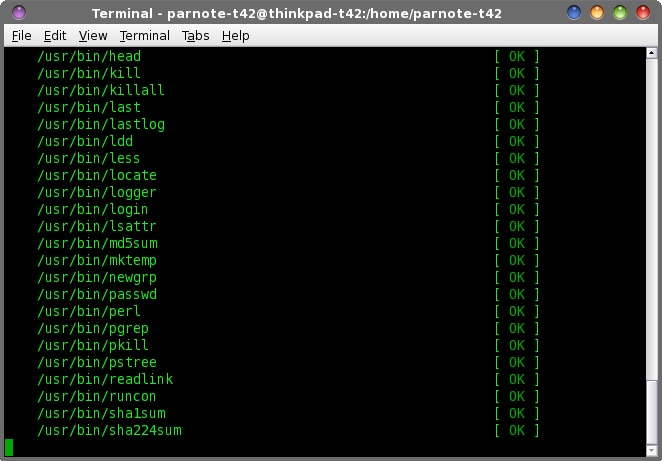    At the end, once rkhunter has run all if its tests, it displays a summary screen: 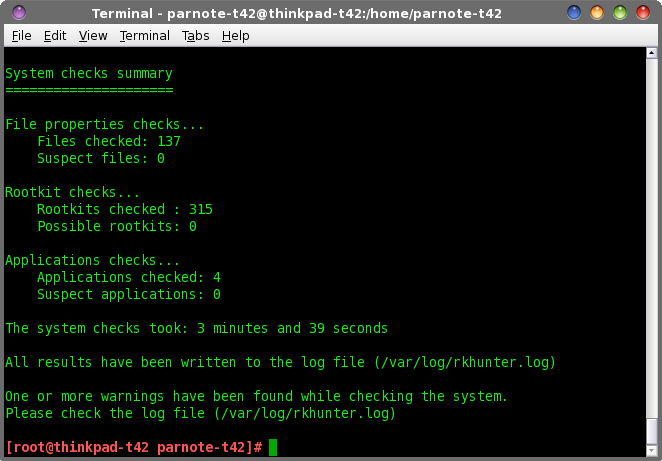 Here are the things that rkhunter checks when you run it:
-- compare SHA-1 hashes of system binaries against known values in its database 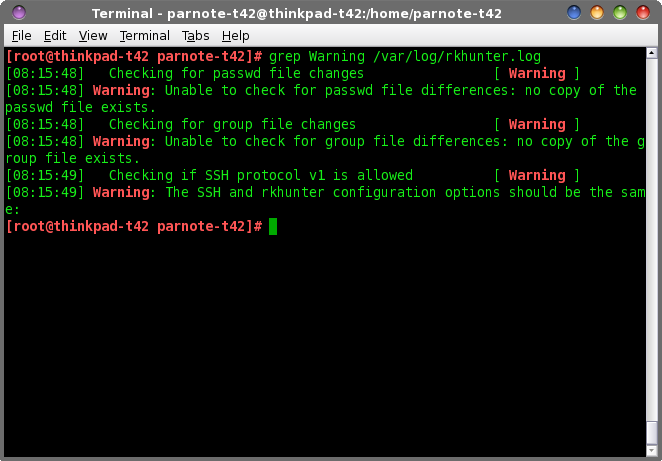 While rkhunter is running, it writes out all of the warnings it finds to the /var/logs/rkhunter.log file. You can easily view those logs from the command line. Still as the root user, enter the following: grep Warning /var/logs/rkhunter.log Every time you run rkhunter, the log file will be overwritten. If you want to keep all of your warnings from every time you run rkhunter, change your command to rkhunter --append-logs --sk -c and the new warnings will be appended to the end of the rkhunter.log file. You should update the rkhunter database periodically. Monthly (or more often) would probably be best. Enter the following command (as the root user) to update the database: rkhunter --update You can also set up rkhunter to run on a regular basis, via crontab. Enter the command in crontab (or your favorite crontab GUI program, such as Gnome Schedule or VisualCron) as follows: rkhunter --cronjob --append-logs The command above will run as scheduled with crontab, and append any warning information it discovers to the end of the log, stored in /var/logs/rkhunter.log. While you can decide how often to run rkhunter, it would be prudent to run rkhunter at least weekly.What Are These Warnings? Keep in mind that rkhunter is merely a rootkit detector. It cannot remove rootkits. Some warnings may occur because you have open ports on your network adapters. On my computers, it usually throws up a warning because of an open SSH port (I use SSH to access files on the various computers around my house). Below is a sample of the warning information from a recent rkhunter session:
[12:12:21] Checking if SSH protocol v1 is allowed [ Warning ]
Other warning messages may occur because of software upgrades, custom system configurations, or other legitimate system changes. If rkhunter reports a rootkit, you will need to check if it is a false positive. The best thing to do if you get a positive report of a rootkit, or if you get other warning messages, is to re-run rkhunter. Enter the following, as the root user:
rkhunter --propupd (updates database and clears logs) If you still get the warning message, try Googling the specific warning message to see if other folks have received the same warning message. Often times, you'll get your answer. If you still need further assistance, you can sign up for the rkhunter mailing list, and post a question there. What to do if you have a bonafide rootkit Fortunately, rootkits under Linux are not a common occurrence, so the chances that you'll need to follow these directions are slim. But if you do, your first step is to immediately take the affected computer offline. Then, backup all of your personal data. Do not copy any binary file that you cannot confirm is clean. Remember that rootkits are sneaky little devils, and may masquerade as another file -- and often a very innocent looking file. Unless you are a security expert, attempting to remove a rootkit yourself may not be the best solution. A security expert should be able to diagnose the full mechanism, attack vector, and penetration path of a particular rootkit. Most users do not have this ability.
In this case, your best choice is to reinstall, then move all of your data back onto the computer. Be wary of personal remasters, since the rootkit may have been copied to the personal remaster, as well. It would be best to reinstall from the latest LiveCD version of PCLinuxOS that you prefer. PCLinuxOS users are spoiled, in a good way, since it only takes 30 minutes (often less) to reinstall the OS. When reinstalling, be sure to format both the / and /home partitions of the drive. This way, you can be more certain that the rootkit isn't hiding out on your hard drive. Sure, it may take some additional time to set everything up the way you like it, as well as reinstalling all of your favorite programs. But in the end, this will be the only way to be certain that you have killed and eliminated the rootkit. Summary It's unfortunate that in today's world, we have to be ever vigilant when it comes to computer security. Unlike 15 years ago when the primary concern was malicious hackers releasing a new virus, we must now fear our governments, government agencies, large corporations, in addition to the malicious hackers. The threat level has spread to include groups that we originally -- and mistakenly -- thought had our security at heart and in mind. Sad as it is, it seems that we can only trust ourselves. Any user who spends any amount of time online (and who doesn't these days?), we owe it to ourselves to remain vigilant in the protection of our data, identity and reputation. |