| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Shellshocked? Maybe, Maybe Not |
|
by Paul Arnote (parnote) On September 24, 2014, a security vulnerability was discovered in bash, the Bourne Again Shell. Bash, the default in PCLinuxOS, is the basic, text based command interpreter that allows a user to interact with their computer from the command line. It is commonly referred to as a shell. Bash is the default shell in many Linux distros, and is the default shell in Mac OS X. Well, OK. You might be. Shellshocked, that is. You are, if you haven't kept your system up to date. But if you have maintained your updates regularly (as you should), your system should be patched and immune from the most common vulnerability. Users of Windows, Android and iOS are not typically affected, at least directly. On the latter two OS's, there is a risk only if the user has installed a version of bash. For example, there are several versions available in the Google Play store on my LG2 Android phone. While it isn't clear by reading the descriptions if those versions of bash are affected, it would be a safe bet to assume that they are. The release dates for most of the versions are from August, 2014, which was before the discovery of the Shellshock vulnerability. Bash came about in 1989, originally written by Brian Fox for the GNU Project as a free replacement for the Unix Bourne Shell. It's POSIX compliant, and also incorporated features from csh, ksh and sh. It is suspected that the newly discovered vulnerability has been there since the beginning. Other accounts place the vulnerability going back to version 1.13. Nonetheless, bash is now up to version 4.3.2, so the vulnerability has been around for some time now.  Basically, the vulnerability allows a function to be exported as an environment variable to another instance of bash. That function can easily include malicious code. In fact, by the end of September, more than 1.5 million exploits of the vulnerability were being tracked. Those exploits ranged from DDoS attacks to "command and control deployment" attacks. It's not difficult to find a very wide assortment of topics discussing the Shellshock vulnerability, more formally known as CVE-2014-6271. The best -- and most understandable -- discussion of Shellshock I found was at Wikipedia. Another excellent discussion was found at troyhunt.com. ZDNet has also published an excellent FAQ about Shellshock. So, I'm not going to go into an in-depth discussion about how it works. I cannot even come close to doing justice to the topic that the excellent resources I've mentioned here have done, as well as all of the other thousands of similar sites doing the same thing.How Serious Is Shellshock? If you were to rate vulnerabilities on a scale from one to ten, with one being the lowest level of vulnerability and ten being the highest, most severe vulnerability, Shellshock rates a 10. In fact, the National Vulnerability Database, sponsored by the DHS (Dept. of Homeland Security) National Cyber Security Division and National Institute of Standards and Technology, rates the Shellshock vulnerability a 10. Shellshock Timeline The timeline is interesting because it shows how quickly the open source community rallied to fix the Shellshock vulnerabilities. Here is a condensed timeline that hits the highlights. You can read the entire timeline here. September 12, 2014: First report of discovery of the initial vulnerability.September 24, 2014: News of the bash vulnerability released to the public. September 24, 2014: First patch of bash is deemed incomplete. September 26, 2014: Second patch of bash is also deemed incomplete. September 27, 2014: Official patch (4.3-027) is released that eliminates Shellshock vulnerability. Three additional patches were released between September 27, 2014 and October 5, 2014. For most users, the 4.3-027 patch fixed the issue. The additional patches fix additional possible vectors for exploitation. These vectors typically represent special cases that are not common to the average user, and that are effectively eliminated with the 027 patch. Who Is At Risk? Well, just about anyone who's still running a vulnerable (unpatched) version of bash carries a certain level of risk. As a "regular" user, your risk is minimal. But why chance it, especially when the "fix" is easily obtainable and available? As an individual, your risk is heightened by the use of untrusted networks, e.g. public wifi hotspots.  Those most at risk are those running servers. The bash vulnerability is most easily exploited from those using CGI scripts to launch another instance of bash, complete with malicious functions exported to the environment variables stack. If you use ssh, you are also at risk. All it takes is some hacker looking for an open ssh port, and when it finds one on your system, it's pretty easy for the hacker to execute malicious commands that will wreck havoc on your system after executing an elevation of privileges. Besides elevating privileges on the affected systems, Shellshock can and has been used in DDoS attacks. There are other potential threat vectors associated with Shellshock, and reading the aforementioned resources will fill you in on those. How To Tell If You're Vulnerable Thankfully, the test to see if your version of bash is vulnerable to the two most common exploits is pretty simple. First, open a terminal session. At the command line, type the following: env x='() { :;}; echo vulnerable' bash -c "echo this is a test" If your system is vulnerable, you will see the following output: vulnerable this is a test 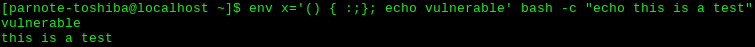 If you system has been patched (e.g., you've kept your system updated), you will see the following output: this is a test 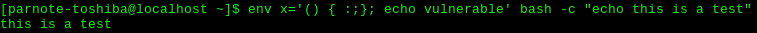 Summary It's amazing that this vulnerability has been around in bash for over 20 years, and security experts have never noticed or realized the problem. It's not entirely clear how long hackers have been exploiting it, either. All that computer security folks can do at this point is speculate and wonder. One thing is for certain: once word about the vulnerability came out, the hackers were quick to exploit it. Fortunately, the two most prevalent vulnerabilities were fixed in a very short time. However, systems remain(ed) vulnerable until the updated/patched version of bash was installed. The fix (an updated bash) was posted to the PCLinuxOS repository within a few days. This illustrates why it's so important to regularly apply updates on your system. Although Windows users weren't directly affected (bash does not run natively on Windows), any user who connects to the internet is/was at risk. Seeing how the vast majority of network servers run Linux, all of their private information was just as at risk as a user who uses one of the OS's where bash runs natively. And these days, it's rare to find a computer that isn't attached to the internet. |