| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Firejail, Easy Sandbox On PCLinuxOS |
|
by Alessandro Ebersol (Agent Smith)  Protecting environments on Linux is one of the most notable features of the operating system. One of the best known techniques is the Chroot, a virtual environment created to run applications safely. But Chroot is quite complicated to set up, and its use is not that easy. But let's say you need features like the ones Chroot can offer, as a security solution for your desktop. How to achieve it? Have all the trouble setting up Chroot for everyday situations? In fact, there is already an easy solution to security problems in Linux, which is called Firejail. What does Firejail do? Firejail uses the implementation of namespaces and sec-comp-bpf on Linux to create isolation between applications, the file system, and the operating system's resources, creating a sandbox that effectively isolates applications from the operating system. It allows a process and all its spawns to have their own particular view of the kernel resources, shared globally, such as the network stack, the process table, and the assembly table. Written in C with virtually no dependencies, the software runs on any Linux computer with a version of the 3.x kernel or later. The sandbox is lightweight, the overhead is low. There are no complicated configuration files to edit, no open socket connection, no daemon running in the background. All security features are implemented directly in the Linux kernel and are available on any Linux computer. The program is released under GPL v2 license. To understand how it works we have to analyze what are the namespaces and what is sec-comp-bpf. Namespaces Much is said about containers. In fact, it is one of today's hot technologies, since it allows the creation of extremely simple virtual machines. The abstract purpose of containers is actually to provide a group of processes with the illusion that they are the only processes in the system. When deployed, this feature has the potential to deliver many practical benefits, such as light virtualization and checkpoint/restore. To give processes in a container the illusion that there are no other processes in the system, several global system resources must be involved in abstractions that make it appear that each container has its own resource instance. This has been achieved with the addition of "namespaces" to various global resources. Each namespace provides an isolated view of a specific global resource for the set of processes that are members of this namespace. The namespaces began to be implemented in the kernel 2.6.23 and have reached maturity in the 3.8 kernel. Currently, Linux implements six different types of namespaces: pid, user, uts, ipc, mnt, and net. Thus, each of these namespaces acts in a way to create a capsule, where an application can be encapsulated and have the illusion that only it has all the resources of the system.I will not dwell too much on each one of the namespaces components, since it is not the scope of this text, but, to speak about Firejail. If you are interested in delving into the namespaces, I suggest reading this article. Seccomp-bpf Seccomp-bpf stands for secure computing mode. It is a simple but effective sandbox simulation tool introduced in the Linux 3.5 kernel. It allows the user to connect a system call filter (syscall) to a process and all its descendants, thus reducing the attack surface of the kernel. Seccomp filters are expressed in the Berkeley Packet Filter (BPF) format. Resources
Installation To install it in PCLinuxOS, in a terminal, as root, type apt-get install firejail firetools, or use Synaptic. Usage To run an application using the default firejail protections for this application (the default profile), run the following:
$ firejail To use Firejail with a specific profile (Firejail has profiles for more than 400 applications on Linux ): firejail -profile = filename.profile Other than the profiles that already come with the program, you can create your own profiles and save them in ~/.config/firejail The profiles saved in this folder take precedence to the profiles that come with the program. If you want to use all your programs with Firejail, just type as root, # firecfg This creates symbolic links in /usr/local/bin pointing to /usr/bin/firejail, for all programs firejail has profiles. Below is the generic Firejail profile:
################################ Let's say, for example, that you want to prevent the application from accessing the user's document directory. To do this, you would add the following line to the newly created profile: blacklist $ {HOME} / Documents Thus, the program that runs with this profile will not be able to access the /Documents folder in your /home. You can make specific folders read only, like this: read-only ${HOME}/Documents The configuration possibilities with the profiles are very wide, having great granularity. In order to delve into the profile configuration commands, you can access this Wiki here: https://wiki.archlinux.org/index.php/Firejail, which is quite complete. Using Firetools Let's take a look at how the FireJail GUI works, Firetools. From a terminal window, issue the firetools command and start the tool. You should see two things: The Firetools window and a prompt for the application running in the system tray.  Pre-configured applications in Firetools You'll find some applications already included in Firetools. To start one, you can either double-click the application launcher or right-click the launcher and select Run. Firetools includes a monitor that you can run to see which applications are running on a firejail. To open this, untar the Firetool, right-click anywhere in the GUI and select Tools. When the monitor opens, you will see all sandboxed applications listed. 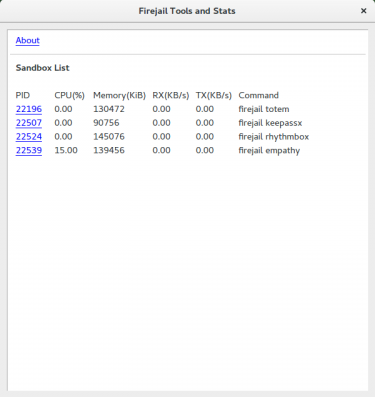 Apps Running in the Firejail Sandbox Final Thoughts Now, why would we use Firejail in PCLinuxOS? Well, some usage scenarios come to mind. Firejail can strengthen the security of a variety of applications, whether desktop or small server applications, perhaps small businesses or schools, offices and administration. Create kiosk machines, and limit user access. Do not allow it to exit the /home folder and shut down the system. And, most importantly, create a security layer with applications packed in appimage format, which are becoming very popular, and which can become vectors for infection and propagation of malware. I hope you can enjoy Firejail, one more security resource for PCLinuxOS. (Appimages were begging for a tool like that). |