| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
I Am Not Amused! (Or How To Spot Phishing Attempts In 2019) |
|
by phorneker  Photograph by Alexander Bassano, 1886, now in public domain and courtesy of Wikipedia Since I wrote my last article on the state of cyber security, I have had numerous attempts from cyber criminals to steal my personal information by way of phishing. On my Gmail account (which was the apparent target of some data breaches), I was able to detect the attempts by simply looking at the Spam folder. 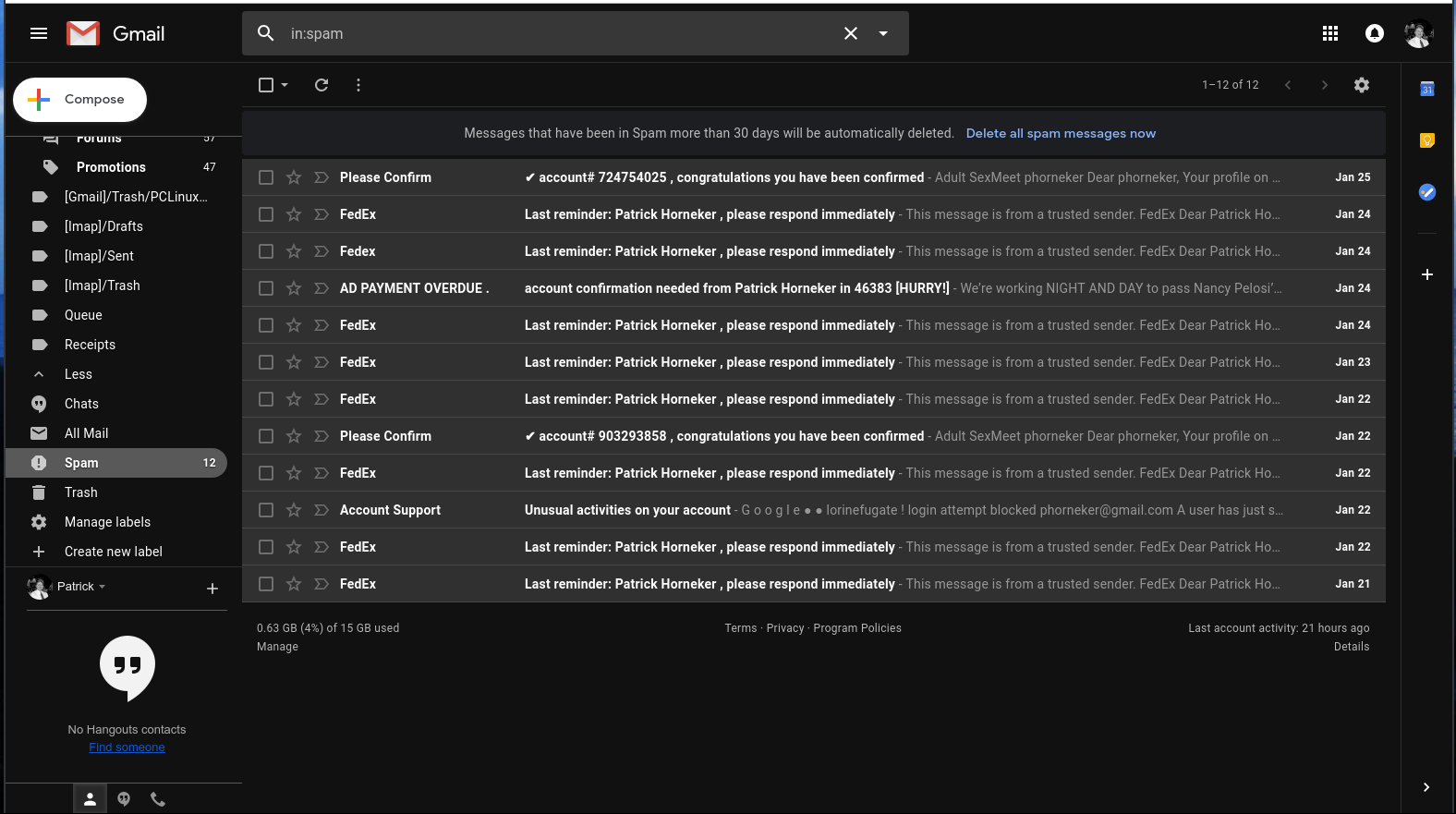 Here, we see several clues as to why these messages were placed in the Spam folder. Here is a clue that these cyber criminals are not the brightest tools in the shed. 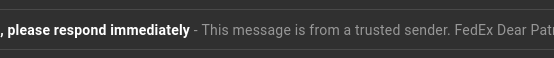 This appeared to have come from FedEx. The fact that these messages were found in the Spam folder and the number of times this was sent is evidence that this was not sent from FedEx. Furthermore, the fact that the first line of the message says "This message is from a trusted sender" to me says that it is not from a trusted sender. Legitimate e-mails from FedEx would never place "This message is from a trusted sender" at the beginning of the e-mail, nor would they ever have a reason to do so. Also, legitimate e-mails from FedEx would not be found in the Spam folder in the first place. ...and I saw all of this without ever having to open a message in the Spam folder. Here is another laughable attempt to get information from me.  which came from this apparent sender 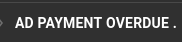 First of all, why would "AD PAYMENT OVERDUE" be a name of a sender for a e-mail message? Second, had I opened this message (and apparently clicked in the embedded link in the message), it would have confirmed that my email address is valid, making this email address a gold mine for cyber thieves. My response in the words of Anne Robinson, "You are the Weakest Link, Goodbye!" ...and we would have to be complete imbeciles to not notice this to be a phishing attempt: 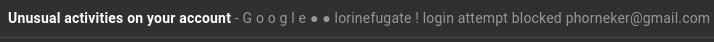 Notice that the word "G o o g l e" contains spaces between every letter in the word...and who the **** is lorinefugate? The only unusual activity here is the fact that this was sent in the first place. I have one simple policy on what to do with these messages:  That's right! Shred them. Lastly, let us look at these two headers: 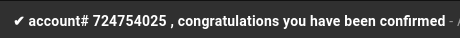 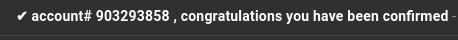 The formatting of the headers alone tells me these are from the same scammer! E-mail is not the only venue where phishing happens. The number of robocalls is expected to spike this year. In October and November of last year, a number of such calls came to my phone with the following numbers (no doubt spoofed as you will see when you read the list):
There is a pattern here that suggests that not only were these numbers spoofed, but they were spoofed by the same scammer. The prefixes 985 and 986 in area code 765 are for phone numbers in and near Peru, IN (Miami County). The 985 prefix in area code 574 is for phone numbers in Elkhart, IN. The last four digits are simply arbitrarily assigned to the spoof. How does 574-985-9799 fit into this pattern? Because, 765-985-9799 is a legitimate phone number for a Peru, IN resident. In order to use this in a caller ID spoof, the 765 had to be changed to 574 for the call to appear to be from the same state. What tipped me off that this is a scam is not the 574 or 765, but the consistent pattern of 985 and 986 prefixes appearing in the list. So, what do I do when I get these calls? What else, send the call directly to voicemail. If the call is important, the caller would leave a message. While the Do Not Call registry eliminates telemarketing calls, it only eliminates legitimate telemarketer calls. (Note that collection agencies are exempt from the Do Not Call list.) What will ultimately solve the robocall problem will be to simply not answer the phone when one of these calls is received. Phishing Quiz There is a quiz you can take to test your knowledge on phishing and how to spot it. ( The quiz can be taken at this legitimate URL: https://phishingquiz.withgoogle.com/ )  Click on "Take The Quiz" to begin. You will need to create a name and email that is used in some of the questions.  The name and e-mail address does not have to be real. In fact, It is best to use fake names and e-mail addresses here for purposes of this quiz. For this quiz, I used "Bob McKenzie" for the name and bobanddoug@noemail.com for the email address.
Click on Get Started to begin the quiz. 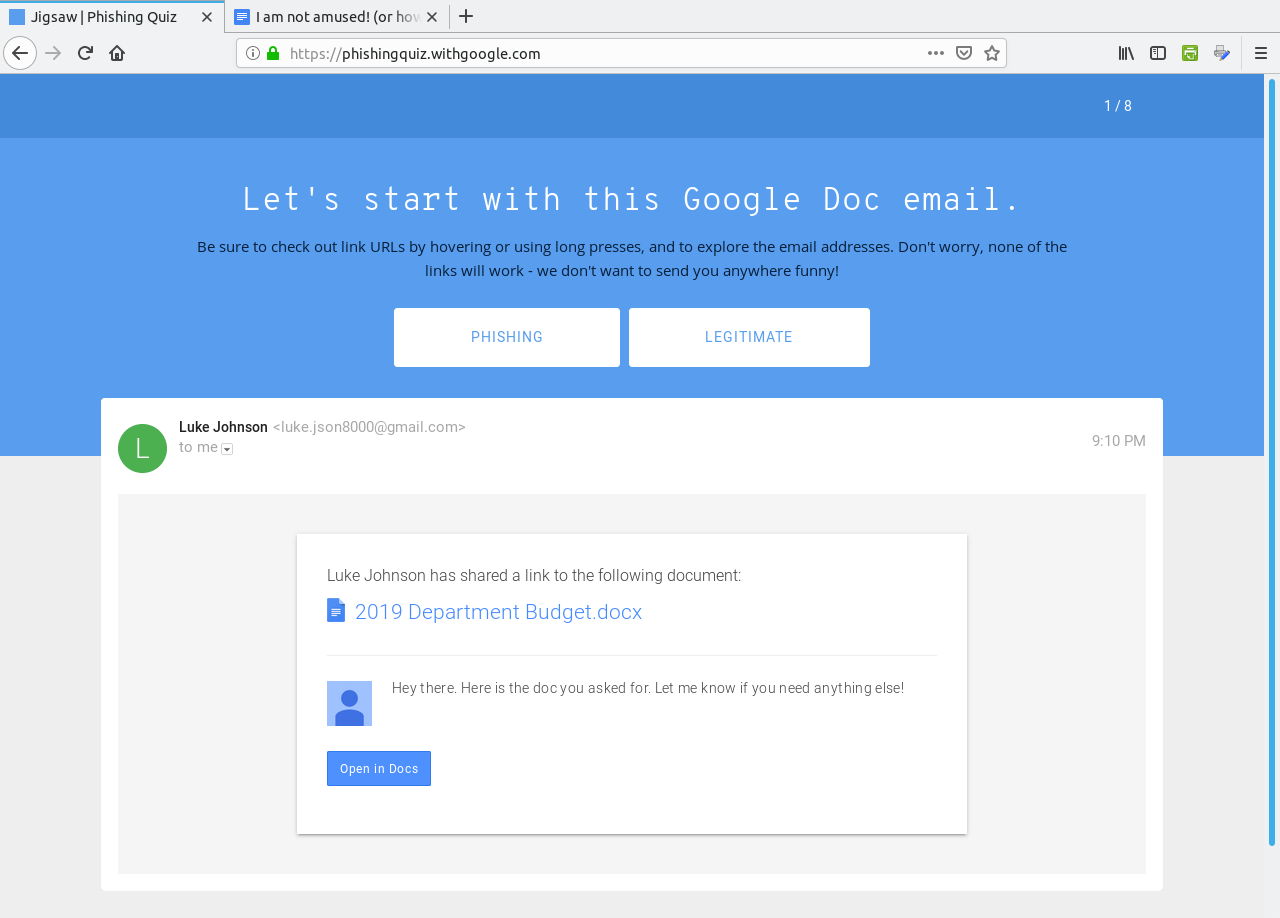 The correct answer here is "Phishing" as the link to the document points to a fake domain "drive-google.com", instead of docs.google.com as one would expect from the Open in Docs link. 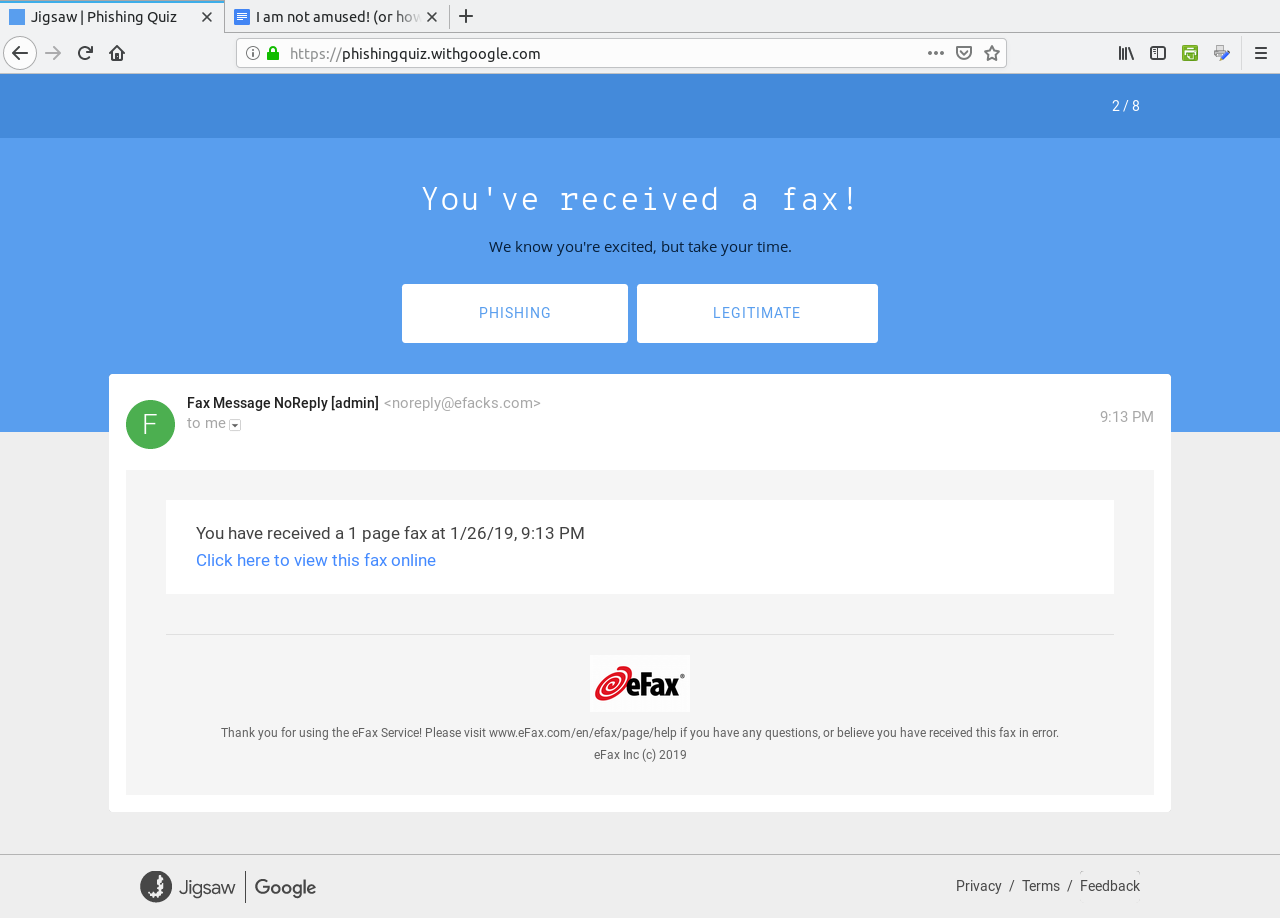 This is a Phishing email as well. The sender address reads "noreply@efacks.com" instead of noreply@efax.com as the logo on the email would suggest. Also, the link contains a URL with a domain of mailru382.co, instead of the proper efax.com domain in the URL. The next question is similar with the link to an improper domain for Google Drive. The fourth question is a legitimate e-mail. 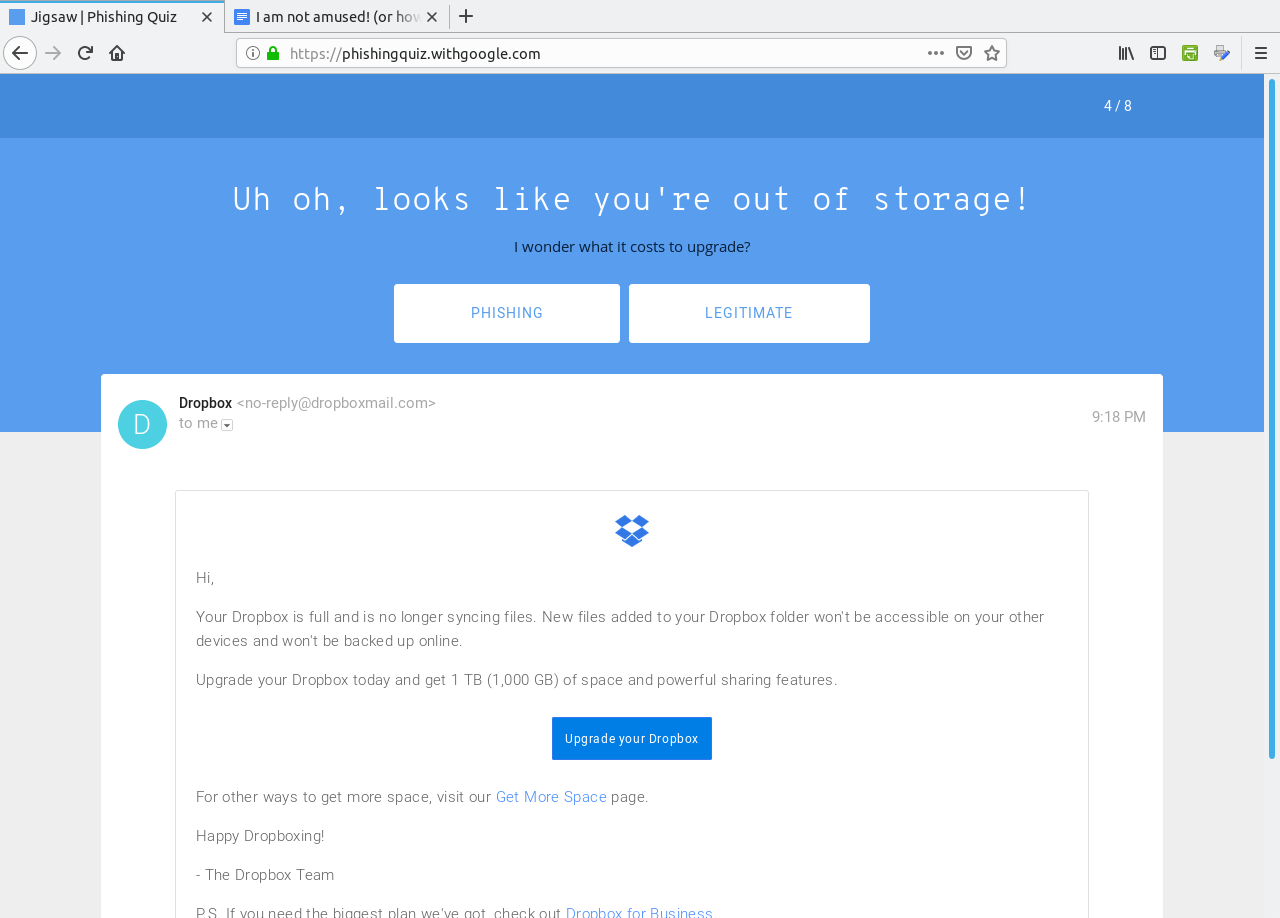 ...from Dropbox nevertheless (which in 2012 experienced a data breach). The correct answer here is Legitimate. The next question contains a PDF of 186KB in length. This one is a Phishing email. 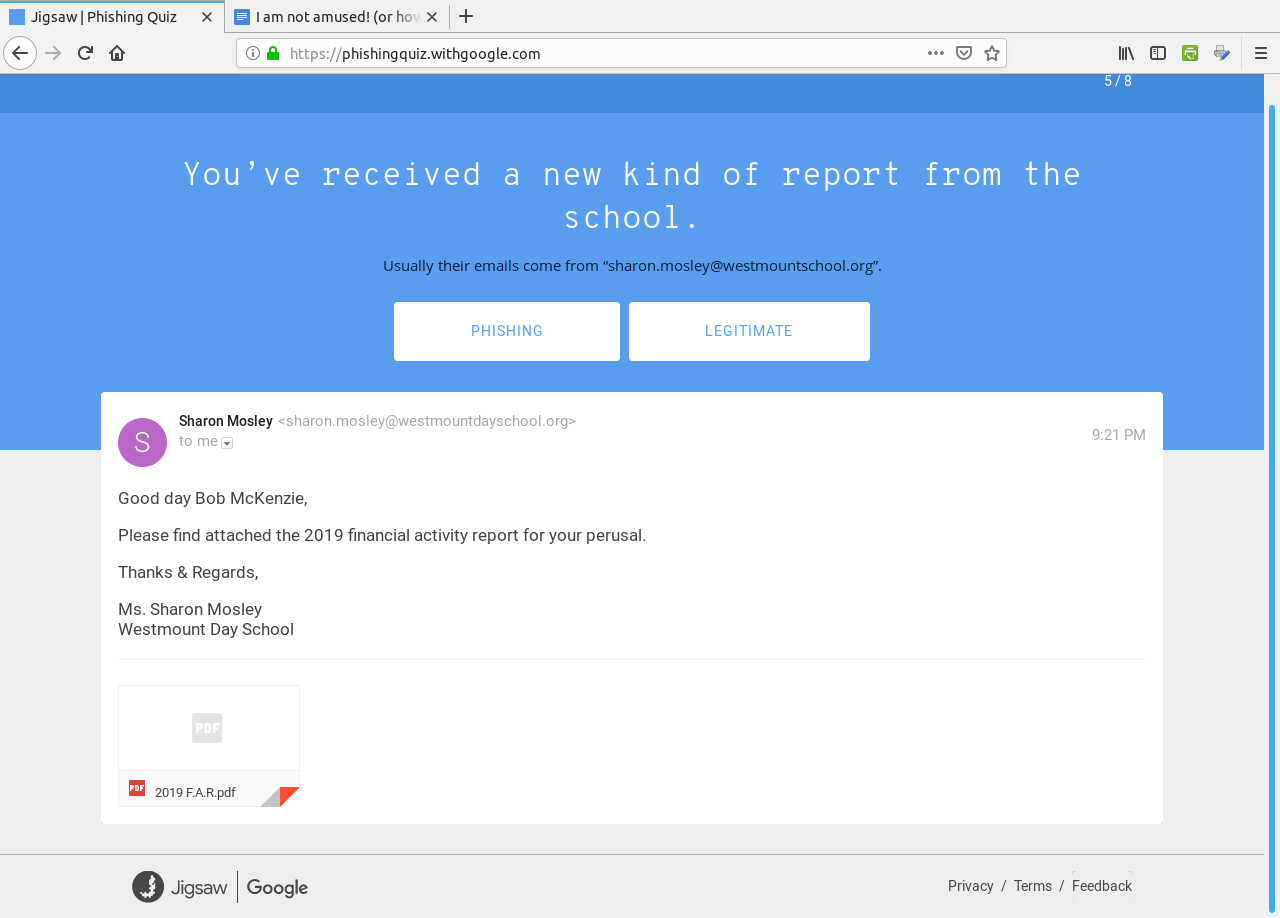 Any attachment that large should be treated as suspicious. This file has either got to be a PDF containing a ton of graphics, which is very unlikely for a financial report, or the file contains malicious code which will compromise (most likely) Windows or Mac OS-X systems. In any case, it is best to not open attachments, especially if you are not expecting anything of the kind in the e-mail. (I liked the "Good day Bob McKenzie" in this message as that was the greeting used on the Great White North sketch.) This next one should be self explanatory. 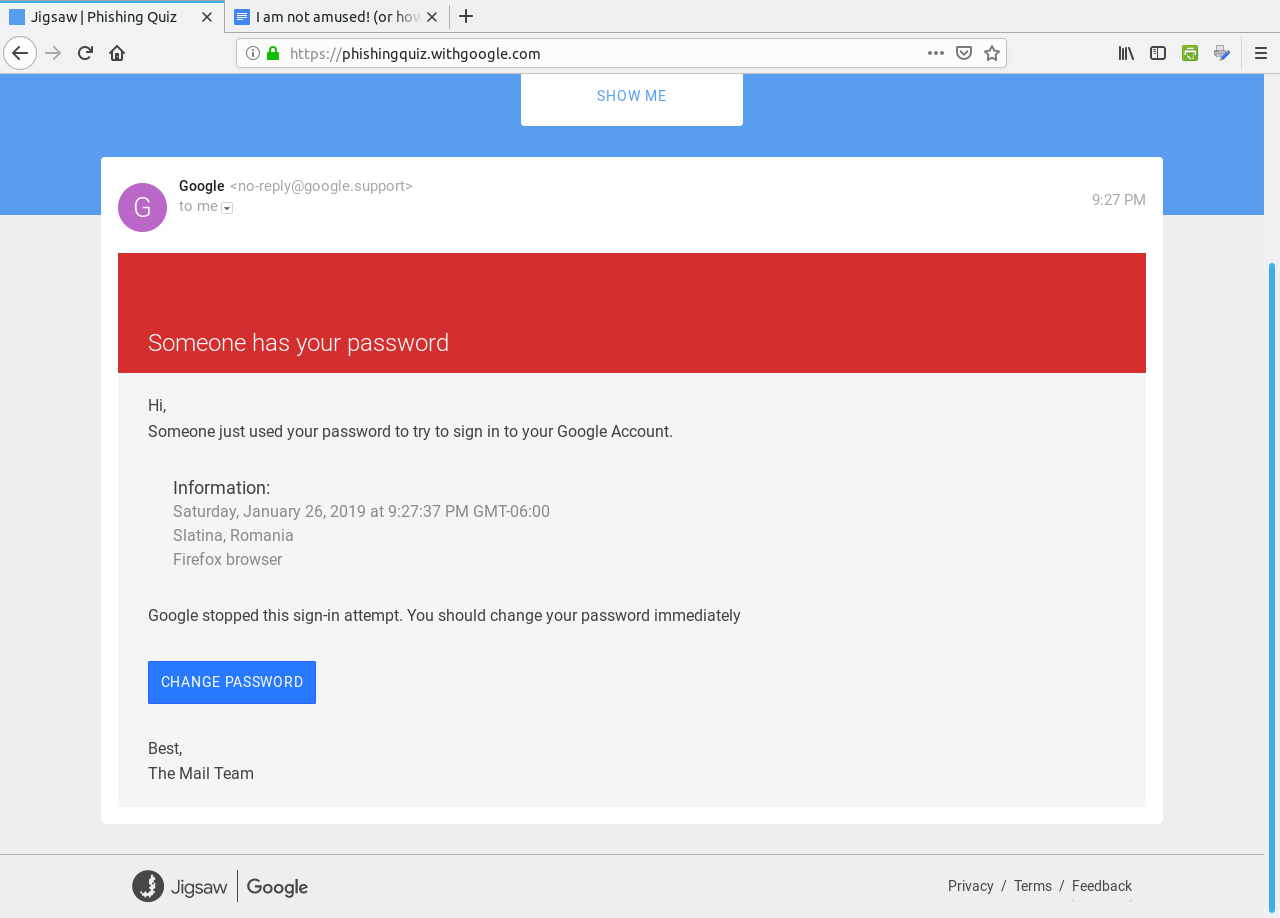 The domain of google.support (up to now) does not exist. The link to change the password links to the domain of ml-security.org, which to my knowledge is unknown or nonexistent. Whoever composed this garbage obviously knew nothing about writing business correspondence. This reads like something a third grader would write. The following question is worse, and is also a Phishing email. 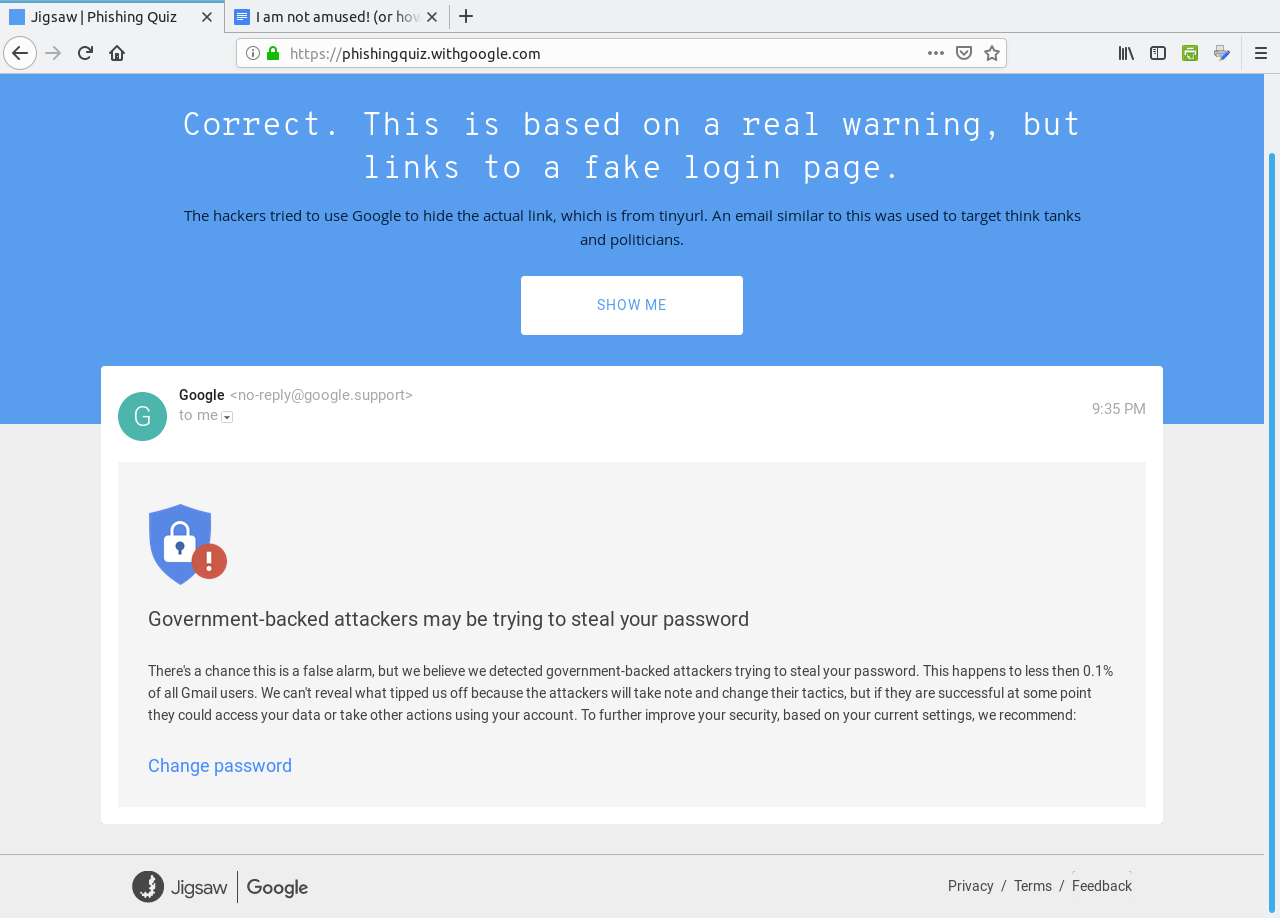 The next question most likely would happen on a Android tablet or smartphone. 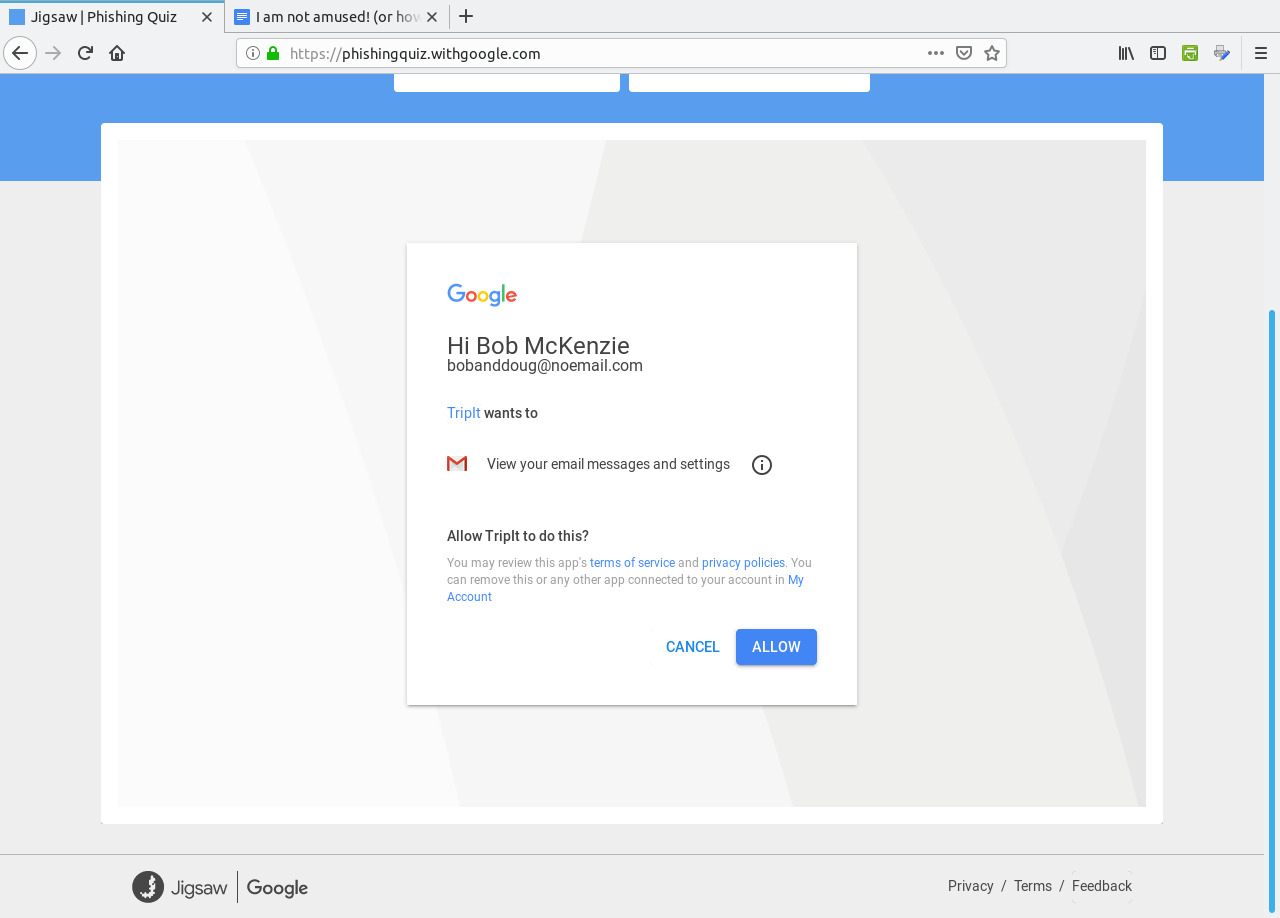 Notice that the dialog asks us to allow "Tripit" to View email messages and settings. Why would we even want that to happen. "View email messages and settings" suggests that we allow whatever process to login to G-Mail as if it was a normal user and physically view the entire inbox of email messages. Allow this to happen? H***, No!!!! However, this turned out to actually be legitimate. Though the links did not show on the quiz, the links were indeed legitimate. In any case, the lesson here is to err on the side of caution, and not allow anything that could be perceived as suspicious from accessing our digital assets. After all, digital assets are just as important as our real world assets (that we pay hard earned money for). WHOIS Lookup Earlier in the quiz, there was a domain of ml-security.org. How do we find out if this is legitimate? Simply install whois from the repository and type in whois ml-security.org from a command line. The following are the results from the command:
Domain Name: ML-SECURITY.ORG What do we learn from this? The domain is registered in the state of California at a company called MarkMonitor, which is a part of Clarivate Analytics. With the tools like whois available at our disposal, we can at least attempt to track the source of these problems. ...and now the fun part begins. E-Mail Collection of Failed Phishing Attempts January 2019 As there seems to be some kind of scam, scandal or data breach every week, it would only be appropriate that I start a new series with the title of this article "I am not amused!" The phrase "We are Not Amused!" (of which I derived the title of this article) was first attributed to Queen Victoria. Whether that is true or not is still under debate (more than 100 years after Queen Victoria's death). Legend has it this phrase was a response to an equerry who told a story that had some impropriety and lack of decorum at the dinner table in Windsor Castle. (This was in the late nineteenth century.)
January 27, 2019 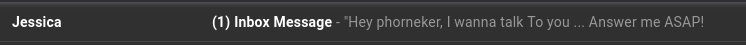 First of all, who is this Jessica? When accessing G-Mail with Chrome or Firefox, you can hover over the sender's name to get the email address from which the message originated. For this message, the email address was enough to tell me this is not a legitimate email: ImOR8hhAqrupUDW3B2p@kpgv5i391rl0pscmi.edu.se A WHOIS search on kpgv5i391rl0pscmi.edu.se gave me corroborating evidence I needed to prove this fact. Just looking at the domain name suggests that this cannot possibly be a legitimate domain, but rather looks like either a cheap imitation of a strong password, or an encrypted form of the actual domain name and/or sender name. The .edu.se would suggest that this came from a Swedish college or university. When I researched colleges and universities in Sweden, it turns out that domains for these campuses end in .se and not .edu.se hence providing another reason this email is not legitimate.
After several previous attempts these guys are at it again. This time only once. This time, I hovered the mouse over FedEx and discovered it came from Fedex@returned.your-server.de Not exactly fedex.com is it? I found out from FedEx that the link supplied in the fraudulent email points to a site containing malware. Even if this malware were targeted at Linux, the worst case scenario here would be to have the malware terminate with a Segmentation Fault message. (Thank God we do not run systemd, and that I delete these messages immediately.)  January 28, 2019 Then, the very next day, these three consecutive messages appeared in my Spam folder. 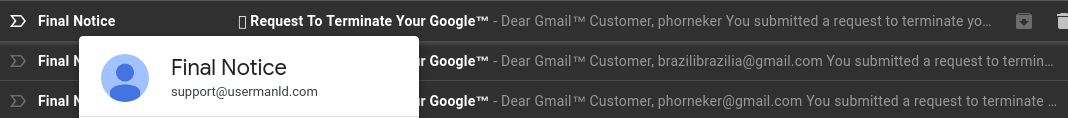 I had the mouse pointer on the top Final Notice, and found the address to read as support@usermanld.com ...of which usermanld.com is not a valid domain. 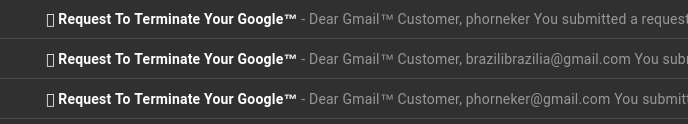 The headers in these three messages start with a unknown character as represented by the box before the word Request, and end with the trademark symbol. While the name Google is trademarked, Google does not place that trademark in legitimate emails. The first message has only the username, the third message contains the full email address, and the second message has a different email address. (Who is brazilbrazilia on Google Plus or YouTube?)  ...and then there is this gem:  The date on this email is January 28, 2019. The previous message in the header shows the original message sent March 29, 2018, which would have been nine months ago. So, I checked the Sent folder, and found messages that were sent around that date (March 29, 2018). 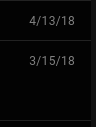 Notice that there is no message in the Sent folder between March 15 and April 13 of last year. Also, who is this Jazmin Adams, and why would it take nine months to respond to this so-called message? For starters, the email address is at teckvar.com which is located in Panama, according to the whois client. I researched the name and found there are several Jazmin Adams in Florida, one that is a RPN in Hannibal, MO, one that is an artist in Fort Worth, TX. The name Jazmin itself lead to a floral shop in the Pilsen neighborhood in Chicago. So, whoever wrote this fake email took a respectable name in vain. ...and our old friend FedEx is at it again...twice!  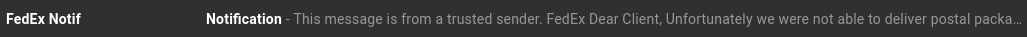 Remember, these messages stated "Last Reminder". Imagine FedEx sending out that many "Last Reminders" to one customer in a six day period. Last time I checked, Last Reminders for any given package should only be sent out once! This "Last Reminder" supposedly came from cv0vc@ec2-13-54-123-19.ap-southeast-2.compute.amazonaws.com ...which as we could figure out is incorrect, and definitely not fedex.com. In fact, this is not a valid domain for email generated from applications that run on Amazon Web Services. (It does not specify the country where the application is running. There is a southeast showing in the domain, but the southeast part of where?) The second one is more lame as the first as Notification has been abbreviated to Notif. Interestingly enough, the word Notification appears in the same email, unabbreviated!  I also love it that it says: Dear client, Unfortunately we were not able to deliver postal package... There are enough evident clues to tell this is a phishing attempt, and the email address is just as obvious: FedEX.Notification@fcvtaifb.mdb.com I'm sure that the people at FedEx are getting FedUp with this nonsense. Online dating sites are targets to this type of phishing. Even the dating site eHarmony falls victim to this:  First of all, eHarmony would never solicit business in this manner, let alone allow a third party vendor to do likewise. But whoever owns info.q8ffitul471@fgz.newgiftshere.com seems to disagree. The message should read "Sign up today...and get your identity stolen!" (These people didn't sign up for eHarmony.)  De Staalmeesters - The Syndics of the Drapers Guild, Rembrandt van Rijn, 1669 Public domain, courtesy of Wikimedia This next one should be self explanatory:  Sounds like those late night ads that appeared on analog television back in the 1990s and early 2000s. The email address should tell the whole story. 5g98dantrwy4jfzac@qb3bbncuz5ivm5zzn.luu.ignorantinterest.com ignorantinterest.com? You said it! January 29, 2019 What an appropriate way to nearly end this collection than with Victoria herself (or should I say Viktoria)  This one came from sexy_victoria@vatulop.com.  By John Tenniel - Transferred from en.wikipedia to Commons., Public Domain, https://commons.wikimedia.org/w/index.php?curid=5827242 January 30, 2019 Just when I thought this was over for the month, another such phishing attempt was made, this time as a fake offer for a personal loan. This phishing attempt comes with an email address of: info.05chtnxfu0e@mx4.medicalinnovationz.com I don't know about you, but any name that has a "z" at the end of it should never be trusted to be legitimate. This is one of the oldest tricks in the book when it comes to scamming. Even if it were legitimate, why would a company that is in the health care business be offering personal loans (other than to cover the high cost of healthcare)? ...and then there is this:  This one somehow ended up in the Primary folder instead of the Spam folder. I will not open this one due to the fact that this message is empty.
KetoSlimDiet. has an email address of  This is the KetoSlimDiet. :-) ...and once again, another "Last Reminder from FedEx" shows up.  This is getting rather old, isn't it? This one is from FedEx@book.your-server.de, which happens to be from the same domain as the email I got three days ago, which had an email address of FedEx@returned.your-server.de...and true to form:  from 18r6c@ec2-13-54-123-19.ap-southeast-2.compute.amazonaws.com which resides on the same infected server as cv0vc@ec2-13-54-123-19.ap-southeast-2.compute.amazonaws.com...and in about three days...(two, sir)...two days, I should get another one or more of these messages, and attempts to infect this machine. Eventually, whoever is sending this garbage will give up.  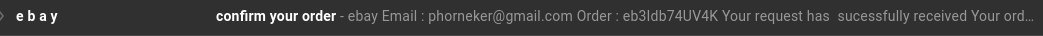 This one has "Phishing!" written all over it. The sender name "e b a y" is spelled with extra spaces, and has an email address of support@onsarsnbz.com. 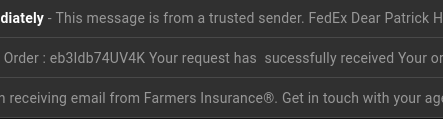 Note the poor quality formatting of the message. There are two spaces between "has" and "sucessfully", which itself is misspelled, and there is no period after the word "received". Even if there were a period there, there should have been two spaces after the period to properly separate the sentences. Also, "Your request has successfully received" is not a complete sentence.  "Night Watch", Rembrandt van Rijn, in public domain courtesy of WikiCommons. There is a third message in the list for January 30, 2019:  This appears to be from a Farmers Insurance agent, of which the message has a trademark symbol after the word "Insurance". The email address appears to be one from Farmers Insurance itself: ADIAZ@mail.farmers.com. But it is not! The Farmers Insurance website has a feature that allows you to find an agent. It turns out that the scammer used this tool to come up with the sender name. Clicking on the Contact Me link at the website pops us a form where messages can be sent. In other words, the agent's email address is not listed on the website! Also, the sender name is in all capital letters, which is very unusual for a legitimate email address. January 31, 2019  From the people that brought us the FedEx notifications and the Terminate Your Google emails of a few days ago comes this so-called granted request email. Offers.Notification@minjundv.mdb.com Initially, mdb.com told us they were unable to "deliver postal package". Now, they are telling us that the "request has been granted" to unsubscribe, but to what? As this is one of the cyber criminals that attempted to infect my laptop with whatever c*** they were planning to install (not that it mattered as it would fail to work on PCLinuxOS), this email message could well have made things worse. The message started with "This message is from a trusted sender." Where have we heard that before? Oh yeah, in those many FedEx "Last Notification" emails sent over the past week!  Ha! You think this is going to stop these messages? I don't think so! Responding to this will do just the exact opposite, and then some. The first one has an email address of Laura.wthxta4bnn@wthxta4bnn.dwy, which is obviously not a valid domain name. But that second one. This looks familiar. Oh yeah, the message from Jessica received on January 27.  At least with an email address of ImOR8hhAqrupUDW3B2p@kpgv5i391rl0pscmi.edu.se, the sender attempted to make an effort to mask the real email address. But today's version of the message has an email address of a1b3a7fc7fb@a1b3a7fc7fb.singlehosti.com, which is evident of two things. First, the sender name and subdomain for ".singlehosti.com" is a laughably obvious copy and paste operation. (Anyone can do that.) Second, whoever is doing this is becoming increasingly frustrated with the lack of success (in getting personal information needed to steal money and identity). This is good, as the success here is that this method of combating phishing attempts is so far successful. Not to mention this is reminding me of the Aesop fable "Boy Who Cried Wolf". The fact that these messages come to the Spam folder daily suggests that a network of unattended machines (or even processes in a certain public cloud) simply use a form letter and one or more databases to create the messages. One would think that after a while, these people would simply give up and move on. However, machines (without artificial intelligence) do not have that capability.  Francis Barlow's illustration of "Boy Who Cried Wolf", 1687, in public domain and courtesy of Wikipedia. Conclusion While we had some fun (and maybe some good laughs) with these phishing attempts, phishing itself is no laughing matter. Whoever is doing this is serious about stealing your identity and your money. By presenting these emails the way I did, hopefully we can be more vigilant about our use of electronic messaging systems, and one day, make this type of activity much less profitable, and hence make this type of activity stop for good. As I get these messages in the Spam folder almost every day, there is more than enough material to create a new column for this magazine, at least until the phishing stops. |




