| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
De-Googling Yourself, Part 8 |
|
by Alessandro Ebersol (Agent Smith)  We have reached the end of this series, and let's reflect on all of that's been discussed before. Don't Be Evil... No more We saw that Google's motto is no longer, they have changed, now it is Do the right thing, and that can be many things depending on where you look. But as we want to preserve ourselves from the "eyes" of the big brother, we will have to take some precautions. Google's Do's and Don'ts Well, as we've seen before, I'm not going to go over already-trodden terrain, but to list, in a succinct and straightforward way, what to do to lessen Google's intrusion into our private lives. Google's DNS Google's famous DNS, 8.8.8.8, should not be used. Google may "hide" sites it doesn't want to promote. Use OpenDNS instead (208.67.222.222) Use Only HTTPS (Hyper Text Transfer Protocol Secure) HTTPS (HTTPS) is an implementation of the HTTP protocol over an additional layer of security that uses the SSL/TLS protocol. This additional layer allows data to be transmitted over an encrypted connection and to verify server and client authenticity through digital certificates. The TCP port used by default for the HTTPS protocol is 443. The HTTPS protocol is used, as a rule, when it is desired to prevent the information transmitted between the client and the server from being viewed by third parties, such as online shopping. The existence in the address bar of a lock (which can be left or right depending on the browser used) demonstrates secure page certification (SSL/TLS). The existence of this certificate indicates the use of the HTTPS protocol and that communication between the browser and the server will take place securely. To verify the identity of the server, double-click the lock to view the certificate. Over HTTPS connections, third-party MITM attacks are not possible because the connection is encrypted end-to-end. Thus, it is possible to track that you have accessed a particular site, but not what you have accessed on that site. Watch out for cookies!  A cookie is a simple string of text loaded into users' browsers when they visit a site. Its goal is to enable the site to recognize and remember its users. But cookies make up the majority of online website crawlers. The cookie was invented in 1994 by Netscape's Lou Montulli and John Giannandrea, and originally served to provide websites with a "memory" so that they could, for example, store items in a shopping cart while the user searched for the goods on the site. Although the cookie still serves this purpose, it can also monitor users and provide a lot of information about user behavior. The cookie is widely used for profiling and targeted marketing, and most websites set a large number of both their own and third party cookies. There are also many different cookies: required cookies, analytics or statistics cookies, marketing cookies, and advertising cookies. Strictly necessary cookies work so that a site operates its most basic functions, so that a visitor can visit it. These rarely, or never have any way of tracking users. However, analytics or statistics cookies are usually third-party cookies that track and record user behavior to provide information to the site owner. Marketing and advertising cookies are also often third party cookies that serve to make targeted advertising possible. These cookies are site tracking tools for the companies involved: The company itself, the site owner, and companies that use cookies for tracking and profiling (Google and all others in the ad technology industry: Yahoo, Bing, Facebook , etc ...) Types of Cookies As we saw above, there are "normal" cookies, but there are still two other types of cookies: Supercookies and Evercookies. Supercookies contain a unique identifier that allows trackers to link records in their data to track their history and browsing behavior (for example, websites visited including length of stay). An example is Flash cookies (also known as Local Sharing Objects or LSO) which, unlike standard cookies, work independently of the browser and have no expiration date. They are stored locally and can be removed manually. To prevent them from being stored on your device, you must set the Flash plugin in your browser to not load flash objects or only with your consent. To do this, select the "Never Activate" or "Prompt to Activate" options. Evercookies are extremely persistent and difficult to get rid of when they get into the device. Its purpose is to identify a user even after removing standard cookies, Flash and others. Evercookies use different storage mechanisms to store data in different formats at various locations on your device. If cookie data is removed, it is immediately recovered from an alternate storage location. Countermeasures To protect yourself from spy cookies, there are some precautions you can take.
However, over time, user tracking techniques have evolved to become more elaborate and complex. Tracking users without cookies Tracking pixels, also called 1x1 pixel or pixel tags, are transparent images that consist of a single pixel, present (though virtually invisible) on a web page or in an email. When a user loads the webpage or opens an email, the tracking pixel is also loaded, allowing the sender of the tracking pixel, usually an ad server, to read and record that the webpage is loaded or the email is open and similar user activities. The purpose is the same as for third party cookies: to get user information for targeted marketing(or whatever purposes) Information that may be obtained by websites and third parties through tracking pixels includes:
Location Tracking pixels are a widely used form of analytical or statistical tracking, but the General Data Protection Regulation (GDPR) considers it illegal if it is not first consented to by the user. Tracking with Javascript Tracking scripts are parts of Javascript code that usually implement a tracking pixel on a site and are responsible for creating different request types for external domains, passing the data to them. The tracking script can access and create requests using the data available on the page, as well as set different cookies that can be used as identifiers. This commonly transmitted data consists of data available in HTML, a URL, a data layer, cookies, or obtained through an event listener or an API call. The tracking script can make different types of requests to pass this information to the tracking pixel. An example of tracking javascript is "analytics.js" from Google. Countermeasures To avoid problems with trackers without cookies, either transparent gifs or scripts, the following extensions can be installed:
The NoScript extension provides extra protection for Firefox, Seamonkey, and other browsers (Google Chrome): This free, open source add-on allows JavaScript, Java, Flash, and other plugins to be run only by trusted websites of your choice (eg. your bank's website). NoScript also provides the most powerful anti-XSS and anti-Clickjacking protection ever available in a browser. NoScript's unique whitelisting-based preventive script blocking approach avoids exploiting security vulnerabilities (known as Meltdown or Specter and even not yet known!) without loss of functionality. You can enable JavaScript, Java, and plug-in execution for trusted sites by simply left-clicking on the NoScript status bar icon or by using the contextual menu for easy operation in pop-up windows without a status bar.
Adblock Plus is an ad filtering extension for Firefox, Chrome, Opera, Microsoft Edge, Internet Explorer, Yandex and Maxthon. This program was included in the list of Firefox add-ons as of January 17, 2006. Due to its huge usage, around 80,000 downloads per day have been reported, reaching 100 million in total. Like Mozilla's image blocker, Adblock blocks HTTP requests according to their source addresses and can block IFrames, scripts and Flash. It also uses automatically generated user stylesheets (CSS) to hide, block, elements such as text-based applications on a page as they load.
A smart extension that controls javascript, iframes, and plugins in Google Chrome. Scriptblock is an extension that provides better control of javascript, iframes and other unwanted content. It can even mitigate cross site scripting (XXS) and drive-by-downloads attacks. ScriptBlock works perfectly in conjunction with other extensions like AdBlock, AdBlock Plus or Ghostery. You can add trusted sites to a whitelist so that they are not affected by ScriptBlock. Available for Palemoon and Google Chrome. Fingerprinting Fingerprinting is an advanced browser identification technique that the user is accessing in order to uniquely and accurately identify the user. There are several Fingerprinting techniques, and let's illustrate some of them. In fact, the sophistication of Fingerprinting is such that it seems to come out of a spy movie. Basically, there are 4 types of Fingerprinting:
Canvas Fingerprinting HTML Canvas allows the web application to draw real-time graphics, with functions to support drawing shapes, arcs, and text in one Custom canvas element. Differences in font rendering, anti-aliasing, and other device features make devices draw the image differently. This allows the resulting pixels to be used as part of the device fingerprint. The image below is a representative example of the types of screenshots used by fingerprinting scripts.  AudioContext Fingerprinting Fingerprinting techniques are not usually used in isolation, but together. One of the new fingerprinting techniques accesses the AudioContext interface and related interfaces. Trackers try to use the audio API to fingerprint users in various ways. How it works? An audio signal is generated by an oscillator and the resulting signal is split after processing to create an identifier. This does not require access to the device microphone and depends on differences in the way the generated signal is processed. In the figure below, the fingerprint audio of my notebook (where I wrote this article) compared to the fingerprint audio of a standard Android reference device. 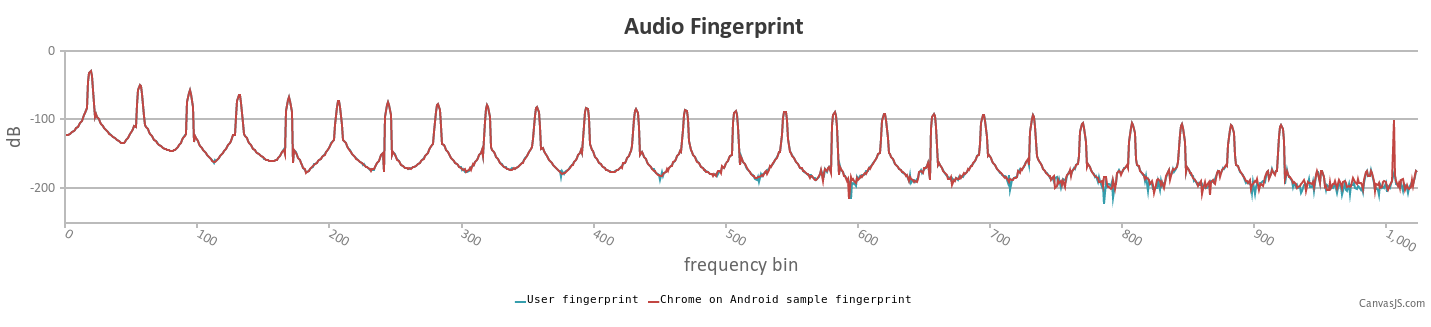 Also, with this technique, it was possible for the script to profile my hardware admirably: AudioContext Fingerprints AudioContext properties:
{ Fingerprint using DynamicsCompressor: 35.73833402246237 Fingerprint using DynamicsCompressor (hash of full buffer) : 5f5ca60e8aa59e3b0f1f5d3064746a42b760ed57 Fingerprint using OscillatorNode: 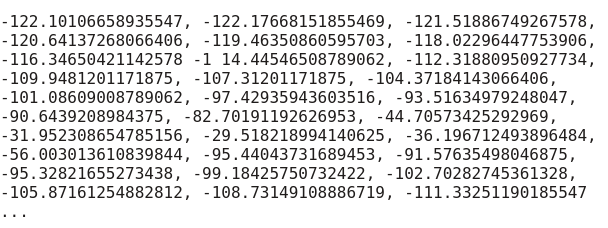
Fingerprint using hybrid of OscillatorNode / DynamicsCompressor method: 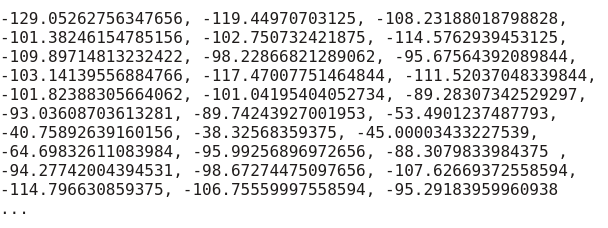 WebRTC Local IP Discovery WebRTC is a framework for real-time, point-to-point communication in the browser and accessible via Javascript. To find the best path between peers, each pair collects all available candidate addresses, including addresses from local network interfaces (such as Ethernet or WiFi) and public-side addresses from NAT, and makes them available to the Web application without explicit permission. of user. A fingerprinter script can leverage these addresses to track users. Canvas-Font Fingerprinting Javascript and Flash were used to enumerate fonts in the browser and also to profile users. The HTML Canvas API provides a third method for deducing fonts installed in a specific browser. The screen rendering interface exposes a measureText method, which provides the resulting width of the text drawn on the screen. A script can try to draw text using a large number of fonts and then measure the resulting width. If the text width is not equal to the text width using a default font (which would indicate that the browser does not have the tested font), the script may conclude that the browser has that font available. As an example, here is the data that a test script extracted from my notebook: Canvas, Javascript, and Flash Font Detection Canvas font detection: Andale Mono; Arial; Arial Black; Bitstream Vera Sans Mono; Calibri; Cambria; Cambria Math; Comic Sans Courier; Courier New; Georgia; Helvetica; Impact; Lucida Console; Lucida Sans Unicode; Microsoft Sans Serif; Palatine; Segoe UI; Tahoma; Times; Times New Roman; Trebuchet MS; Verdana; Wingdings; JS / CSS font detection: Andale Mono; Arial; Arial Black; Bitstream Vera Sans Mono; Calibri; Cambria; Cambria Math; Comic Sans MS; Courier; New Courier; Georgia; Helvetica; Impact; Lucida Console; Lucida Sans Unicode; Microsoft Sans Serif; Palatine; Segoe UI; Tahoma; Times; Times New Roman; Trebuchet MS; Verdana; Wingdings; Flash font detection: AD MONO, Adventure, Andale Mono, Arial, Arial Black, Babelfish, Bitstream Charter, Bitstream Vera Sans, Bitstream Vera Sans Mono, Bitstream Vera Serif, Blue Highway, Condensed Blue Highway, Calibri, Cambria, Cambria Math, Cantarell , Cantarell Extra Bold, Cantarell Light, Cantarell Thin, Christmas School, Comic Sans MS, Courier New, DejaVu Math TeX Gyre, DejaVu Sans Condensed, DejaVu Sans Light, DejaVu Sans Mono, DejaVu Serif, DejaVu Serif Condensed, Deutsch Gothic, Dingbats, DirtyBaker'sDozen, Georgia, Hershey-Gothic-English, Hershey-Gothic-German, Hershey-Plain-Duplex, Hershey-Plain-Duplex-Italic, Hershey-Plain-Triplex, Hershey-Plain-Triplex-Italic, Hershey-Script-Complex, Hershey-Script-Simplex, Impact, Larabiefont, Liberation Mono, Liberation Serif, Lucida Console, Lucida Sans Unicode, Microsoft Sans Serif, New, Nimbus Mono L Nimbus Roman No9 L, Nimbus Sans L, Nimbus Sans L Condensed, Segoe UI Light, Segoe UI Light, Standard Symbols L, Symbol, Tahoma, Times New Roman, Trebuchet MS, URW Bookman L, URW Chancery L, URW Gothic L, URW Palladio L, Utopia, Verdana, Webdings, Wingdings Countermeasures To try to "fool" fingerprinting, you can install some extensions in your browsers: Secret Agent (Palemoon, Waterfox, Seamonkey, Icecat) enhances the privacy of your web browsing by rotating the identity of the browser 'User Agent' with all web requests ( or each page load or session of each browser).Randomizing your User Agent makes it a little harder for bad guys, rogue ISPs, spies like Phorm, corrupt governments, and other nasty surveillance / tracking threats to correlate your clicks based on device fingerprinting. Ghostery is a free, open source privacy and security related browser extension, plus a mobile browser application. Since February 2017, it belongs to the German company Cliqz International GmbH (formerly owned by Evidon, Inc., formerly Ghostery, Inc. and the Better Advertising Project). The code was originally developed by David Cancel and associates. Ghostery allows its users to easily detect and control JavaScript tags and trackers. JavaScript bugs and beacons are embedded in many web pages, largely invisible to the user, allowing the collection of user browsing habits through HTTP cookies, as well as participating in more sophisticated forms of tracking, such as canvas fingerprinting. As of 2017, Ghostery is available for Mozilla Firefox, Google Chrome, Internet Explorer, Microsoft Edge, Opera, Safari, iOS, Android, and Firefox for Android (not available for Palemoon, Seamonkey, Icecat). Use And Abuse Private Browsing A Private browsing automatically deletes browsing information such as passwords, cookies and history, leaving no trace after you log out. Private browsing is available on all popular browsers (Firefox, Chrome and all derivatives thereof) TOR and VPN Using TOR browser can get you in trouble: The U.S. Supreme Court quietly approved a rule change that would allow a federal magistrate judge to issue a search and seizure warrant for any target using anonymity software like Tor to browse the internet. As for Virtual Private Network (VPN) networks, they're as good as the companies behind them. That is, as long as these companies don't hand over your browsing history and data to government agencies, you're fine. But otherwise... I think that both the TOR browser and virtual private networks deserve their own articles, where they can be further analyzed. Final Words Over the course of eight months, we thoroughly and thoroughly analyzed the ways Google uses to spy on its users. We've looked at the known ways, and many new online tracking technologies, that in these perilous times we live in, where freedom of thought and expression can put the average citizen in hot waters, given the prevailing polarization and political radicalization. Protecting privacy, freedom of thought and expression has become a necessity these days, but mostly staying out of trouble, controversy and online discussion that can hurt ordinary people (as Richard Stallman was harmed by giving his opinion on a very sensitive subject). So take a good look at tips for protecting your online privacy, and especially don't get involved in controversy or sensitive issues, whether it's on Twitter, Facebook, YouTube or whatever, as out-of-context statements can cost careers, reputations and even jobs. A big hug, and see you next month. |






