| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Zoombombing Is A Crime, Not A Prank |
|
by Paul Arnote (parnote) Study Reveals Hidden Behaviors Of Mobile Apps  Fresh from a report (PDF) jointly published by authors from The Ohio State University, New York University, and CISPA Helmholtz Center for Information Security comes word that 12,706 apps surveyed with a new static analysis technique called InputScope had hidden backdoors, hidden master passwords, secret access keys, hidden blacklist words, and secret commands embedded within them. These vulnerabilities allow users to access admin-only functions, or attackers to gain access to user information and user accounts. An article on ZDNet dug further into the report. The authors had surveyed 100,000 of the most popular apps in the Google Play store (based on the number of installations), the top 20,000 apps hosted on third party app stores, and 30,000 apps that came preinstalled on Samsung handsets. Overall, they found that nearly 6,900 apps from the Google Play store had hidden backdoors or functions. Nearly 1,100 apps from the third party app stores had hidden backdoors. Meanwhile, nearly 4,800 preinstalled apps from Samsung handsets (almost 16%) featured hidden backdoors. More than 4,000 apps (total) featured hidden "bad word" filters to filter out curse words, racial slurs, political words (even the names of some political leaders), gambling, cult references, pornography, and drugs. The authors of the report did not divulge the names of the apps where they found these security issues, in order to protect the users of those apps from malicious actors. The app developers were all notified of the findings, but not all of the app developers responded. Out To Sea, Sailing About The World, They Never Heard About The Pandemic  Imagine quitting your job, buying a boat, and setting out to sail around the world. Sounds like a dream, huh? That's exactly what Elena Manighetti and Ryan Osborne of Manchester, England did in 2017, according to a BBC story. They sailed about the Atlantic Ocean, sailing from one location to the next. Except the dream turned sour, as dreams sometimes do. They had asked their families to stay in touch. But, they had one ground rule: no bad news. And, the family members complied with that wish. They first attempted to land on a small island that was a French territory. But, they found all the borders closed, and the island in the process of being locked down. So, they sailed on to Grenada. Back in February, they heard a little bit of something about a virus in China. But, because there wasn't much information available about it, they thought it would be all over after spending 25 days at sea. Yes. Their families kept their word. They didn't tell them about the coronavirus pandemic. That was bad news. About as bad of news as you might expect. They didn't know that the entire world was infected. Just off the coast of Grenada, they were able to get a good-enough 4G connection to allow them to find out what had been going on. They contacted a friend already on Saint Vincent, and were told that Elena would be refused entry, because she was an Italian citizen. Her home in Italy is in one of the hardest hit areas of the country. Except Elena hadn't been to her home country in months. Fortunately, they were able to prove via their travel documents and their boat's GPS data that they had not been to Italy in months, and had actually spent the last 25 days sailing the ocean. Elena's family is well, she found out while contacting family in Italy, but they know people who have succumbed to COVID-19. They described how horrible conditions are in the ancient country on the Mediterranean Sea. For now, they are sitting tight on Saint Vincent, hopeful that they will soon be able to continue their exploration of the Caribbean isles. But they are worried, because they also want to avoid the hurricane season, which typically begins in June. New Linux Patch Speeds Up FAT Transfer Times By 7.5X  Just days before Linus Torvalds closed the merge window and released the first release candidate for the Linux kernel 5.7, kernel developer Ogawa Hirofumi sent out a patch that speeds up FAT file transfers on Linux by 7.5 times. Hirofumi's patch enhances the read-ahead performance of Linux's FAT file system code, according to an article on FOSSBytes. To validate the patch, Hirofumi tested the driver on a slow, USB connected 2TB hard drive. File transfer times went from 383.18 seconds to 51.03 seconds after application of the patch. Even though most have moved to exFAT, the older FAT16/FAT32 file system is still in use in some digital cameras and EFI partitions. Prosecutors: Zoombombing Still A Crime  With the near-global coronavirus lockdown and social distancing having taken a prominent role in our daily lives, Zoom, a video conferencing program, has gained a ton of recent popularity. But, as with most anything that becomes popular, trolls and other users with malintent have to come along and ruin things. Sadly, they have taken to exposing themselves to children and yelling racial slurs -- among other things -- as they join Zoom meetings just to disrupt them. The idjits claim that it's just a prank. But not so fast, say U.S. federal prosecutors, according to an article on ArsTechnica. They say it's a crime. From a statement released by the U.S. Department of Justice, U.S. Attorney's Office of the Eastern District of Michigan: Michigan's chief federal, state, and local law enforcement officials are joining together to warn anyone who hacks into a teleconference can be charged with state or federal crimes. Charges may include -- to name just a few -- disrupting a public meeting, computer intrusion, using a computer to commit a crime, hate crimes, fraud, or transmitting threatening communications. All of these charges are punishable by fines and imprisonment. "You think Zoom bombing is funny? Let's see how funny it is after you get arrested," stated Matthew Schneider, United States Attorney for Eastern Michigan. "If you interfere with a teleconference or public meeting in Michigan, you could have federal, state, or local law enforcement knocking at your door." "It is a shame that during a pandemic which is causing fear and anxiety across the globe that there are wrongdoers seeking to disrupt virtual environments which have become essential to communication, teleworking and online learning," said Special Agent in Charge Steven M. D'Antuono. "While Michiganders are sheltering in place, it is important to practice good cyber hygiene. We encourage our communities to visit fbi.gov or ic3.gov to learn more about tips they can take to keep their devices secure." "We were alerted to this problem by a Michigan reporter who participated in a Zoom conference that was hijacked," stated Michigan Attorney General Dana Nessel. "Since then we have learned of other incidents around the country. There are steps people can take to protect their cybersecurity and we encourage all users to follow the proper procedures to ensure their teleconferences are secure." The statement goes on to offer some advice to help avoid becoming a "zoombombing" victim.
In related Zoom news, CEO and Zoom founder Eric Yuan says that he underestimated the threat of harassment on the Zoom platform, adding that he never gave it any serious thought, according to a report on NPR. Yuan is pleased that the FBI has gotten involved in tracking down "zoombombers," and has cooperated with law enforcement officials every step of the way. His company has halted work on adding new features, instead focusing on privacy and security for the next 90 days. He's willing to make Zoom more secure, with better privacy, even if it makes it more difficult to use. Some large school districts, companies and governments have banned the use of Zoom entirely, due to the security issues. Google has also banned its employees from installing it on their work computers, saying it doesn't meet security standards. One recent change to happen to Zoom is that all meetings now require the use of a password. Expect more changes in the future as Yuan works to strengthen Zoom's security. He has recently announced the formation of a security-focused council and advisory board, and hired Alex Stamos, Facebook's former chief security officer, as an outside security advisor to Zoom. If You Have SuperVPN Free Installed On Your Mobile Device ... UNINSTALL IT IMMEDIATELY!  We've covered the benefits of using a VPN here in The PCLinuxOS Magazine before. You've heard about the benefits of using a VPN, I'm sure, from other sources on the internet. So, if you were duped into installing SuperVPN Free VPN Client on your mobile Android device, uninstall it immediately! According to an article on Forbes, the app has been installed by 100 million users. It has since been removed from the Google Play store. But, there are many, many users out there who may not realize that the app behaves in a malicious manner. Specifically, and according the a blog post by VPNPro (who reported the issue to Google): "... it has critical vulnerabilities that allow for man-in-the-middle (MITM) attacks that can easily allow hackers to intercept communications between the user and the provider, and even redirect users to a hacker's malicious server instead of the real VPN server." The SuperVPN Free VPN Client was reported to Google Play Security Reward Program, by VPNPro, and Google verified the security issues. Attempts to contact its developer, so he/she/they can patch the vulnerabilities, were unsuccessful. Even trying to track down the actual developer proved to be a monumental and circuitous task that often led to many dead ends. The "paid" version of SuperVPN VPN Client is still available in the Google Play store. It definitely differs from the free version by not displaying any ads. However, it would probably be a wise idea to avoid the paid version, as well, since it may have similar (if not the same) security vulnerabilities. Even though the SuperVPN Free VPN Client has been removed from the Google Play store, it's likely that there are many, many users who may still have it installed. Those users may not be aware of the app's security issues, and may continue to use it, mistakenly thinking that they are protected as they would be with a bona fide VPN app. Do You Think That Fingerprint Reader Is Secure?  Well, do you think that fingerprint reader is secure? According to researchers from Talos Cisco Security Research, it might not be as secure as you think it is. Yes, it's true that everyone has unique fingerprints. If you have a smartphone, you've probably used your fingerprint to unlock your phone. Some laptops have a fingerprint reader to enhance security of the data stored on the hard drive. Some USB flash drives use fingerprints to secure the data stored upon it. However, you might be surprised by the answer. And, that answer is mostly NO, that the fingerprint reader can be fooled fairly easily, given enough time and the right materials. Also, all fingerprint readers are not created equal, either. So, the answer becomes "it depends." Using a 3D printer, they made a mold of Al Capone's publicly available fingerprints from the FBI's website. The mold comes out of the printer, and must be cured in a UV chamber before it can actually be used as a mold. When it comes out of the printer, it is too soft and too toxic to be of any use. The mold makes a "negative" of the fingerprint. It took the authors 50 attempts to come up with a usable mold, due to the 3D printed mold shrinking during the UV curing, depending on the time it spends in the curing chamber. They also used a direct collection method (where a cast of an actual fingerprint is made in softened Plastiline modeling material; this was the most successful method), and an optical scan method that scanned a photo of the fingerprint. Next, you have to fill the mold with your material to make a "positive" from the "negative" (the mold). The best performing material they found was fabric glue. Fill in the mold with a thin layer of the fabric glue, wait for it to dry, and then carefully peel it up from the mold. Use that "sheet" to press down over the fingerprint reader. 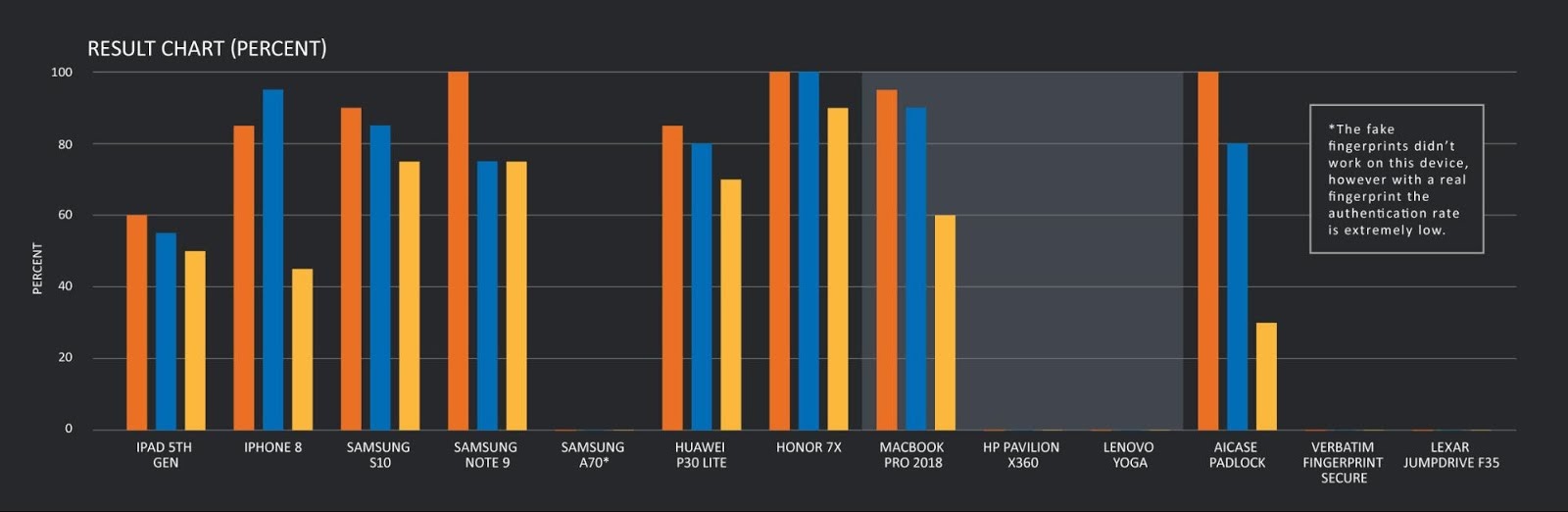 Orange: Direct Collection Blue: Image Sensor Yellow: 3D Printed Molds Once you've made it this far, this is where the fun starts: seeing if you can fool the fingerprint reader. The researchers first tried a MacBook. Believe it or not, they were able to fool the MacBook fingerprint reader 95% of the time. The iPhone and iPad fared only slightly better than the MacBook at not granting access to an unauthorized user. The Samsung S10 and Samsung Note 9 were easily fooled, as was the Huawei P30 Lite and the Honor 7x. Curiously, the Samsung A70 kept the data secure, but the researchers attribute that to the fact that the fingerprint reader on that device barely works even when it's the "real thing." The AICase Padlock was pretty much useless when they used the direct collection method, only slightly better when the image sensor method was used, and was only fooled about 30% of the time when using the 3D printed molds. Amazingly, they were never able to fool the fingerprint reader on laptops running Windows. The researchers attributed this to two traits. First, you tend to "unlock" a laptop less frequently than a mobile device. Because of this, which leads to the second trait, is the fact that Windows samples more data points in the fingerprint. Also, the fingerprint reader code is part of the Windows OS, enabling it to work better across all Windows iterations. The researchers were also unable to fool the fingerprint reader on the Verbatim Fingerprint Secure USB flash drive, nor the Lexar Jumpdrive F35, regardless of the method they employed. There was no mention of any tests involving Linux. So, what were the researchers' conclusions? Well, not much has changed since fingerprint readers were largely introduced in 2013. The security offered by them is pretty much dependent on the method employed to read the fingerprint, as well as how many data points are compared to a saved set of data. The more data points used, the more secure it is, but also the more "finicky" it is, too. Overall, fingerprints are probably sufficient data protection for the more casual user, but can represent a real security hole for individuals and groups that need a higher level of security (2FA would sure seem to be warranted in these cases, I would think). Windows Explorer File Manager Eases Reading Of Linux File Systems 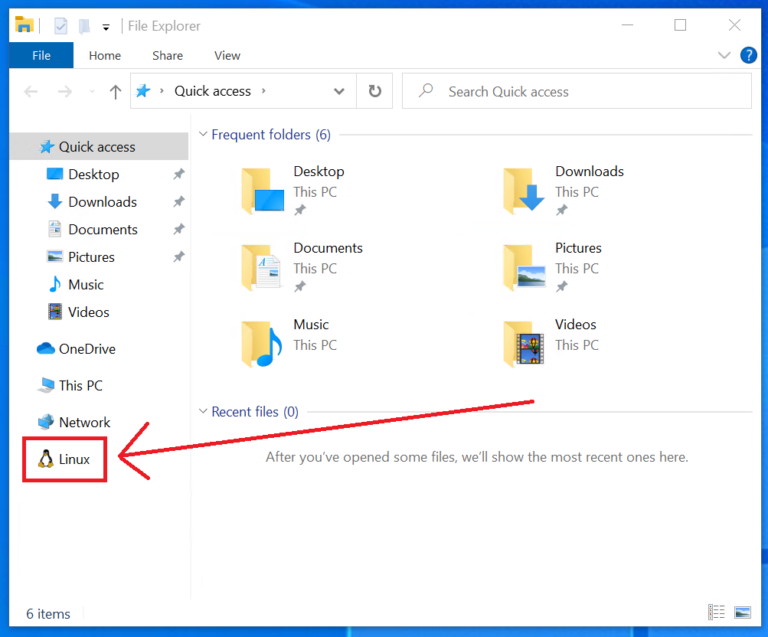 Image: Microsoft Do you dual boot your computer with PCLinuxOS and Windows 10? If you do (and I know there are some of you out there), Microsoft has made a once extremely complicated (if not nearly impossible) task of reading data files on your Linux partitions as easy as a couple of clicks in Windows Explorer File Manager. Now, in Windows 10 Build 19603, as long as you have the Windows Subsystem for Linux (WSL) installed, your Linux files are only a couple of clicks away. From looking at the images (sorry, but I haven't run Windows since XP ... Vista drove me into the loving arms of Linux), it appears that Windows Explorer will give you access to ALL your Linux files, including those whose permissions are usually reserved for the root user under Linux. So, exercise extreme caution if you use Windows Explorer to manipulate files on your Linux partition. You could render your Linux installation incapable of booting. Still, it will be quite a timesaver to allow users to access files saved on their Linux partition(s) while working in Windows, instead of making the user log out from Windows, and then boot and sign in to Linux, copying the file to a shared folder or networked drive, and sign back out of Linux, and have to reboot Windows ... all before even doing anything with the data contained in the file. Phew! I get short of breath just typing all of that out! |