| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Privacy Issues Emerge During Pandemic |
|
by Paul Arnote (parnote) Solar One Light Sail Spaceship Proposed  Alberto Caballero, an amateur astronomer from Spain and coordinator of the Habitable Exoplanet Hunting Project, has authored a paper (PDF) proposing a light sail spaceship, called Solar One, that could take flight by the end of the decade. Caballero takes four current projects and combines them into one proposal to help create his interstellar spacecraft. He wants to take a 10 MW fission reactor (the Los Alamos National Laboratory Mega Power Reactor), couple it with the Sunjammer lightsail proposed by NASA, throw in the High Energy Liquid Laser Area Defense System (HELLADS) developed by DARPA, and launch it via SpaceX's Big Falcon Rocket. The light sail would be propelled by the laser system, which receives its necessary power from the onboard fission reactor. The proposed spacecraft would be able to accelerate to 30% of light speed (0.30c), carry two crews, and be able to travel to Alpha Centauri (4.24 light years away) in 15 years. To put that in a different perspective, since light travels at 186,282 miles per second (299,792 Kilometers per hour) and 670,615,200 miles per hour (1,079,690,472 kilometers per hour), 30% the speed of light would be 201,184,560 miles per hour (323,907,142 kilometers per hour). The light sail would be furled when cruising (neither accelerating or decelerating) to help prevent damage from micrometeorites, and unfurled for acceleration/deceleration maneuvers. The reactor section of the spacecraft would have the thickest protective coating, to also help protect it from micrometeorite damage. Using "off the shelf" projects as he proposes, Caballero is certain that his project will cost less than $100 million (U.S.). The reactor currently costs around $16 million, the HELLADS costs around $21 million, and the Sunjammer light sail costs around $27 million. The ride to the heavens aboard SpaceX's BFR would cost around $30 million. All total: $94 million (U.S.). Of course, there would also be the added expense of building the crew capsule, the descent module, the light sail module, the reactor module, and the module that houses the laser, plus all of the support systems and equipment. All of that isn't going to come cheaply, and may (at least) double the projected costs. Upon arrival at Alpha Centauri, the search will begin to find a habitable planet. Upon finding one, a robotic probe will be sent to the planet to ascertain atmospheric composition, climate, etc. If the robotic probe reports back that the atmosphere is breathable, then members of the crew would use the descent capsule to land on the new world. So, even if the spacecraft were to launch in 2029, it wouldn't arrive at Alpha Centauri until 2044, and we wouldn't even hear of its arrival until 4.24 years (2048 at the earliest) after it transmitted a radio message announcing its arrival. Of course, it should go without saying that this will be a one-way trip for the crews, barring further advances in space travel that allow us to travel faster than 30% the speed of light. It's rather exciting to imagine the feats and accomplishments that our children and grandchildren may bear witness to. Online Dating Threat Actors Target U.S. Universities  As if being single and trying to utilize online dating sites wasn't bad enough, threat actors are now targeting adult singles at U.S. universities with the Hupigon RAT (remote access trojan) malware, according to an article from Proofpoint. The Hupigon RAT has been around since 2006, and is usually associated with state-sponsored threat actors. Researchers from Proofpoint have discovered a large volume campaign targeting faculty and students U.S. colleges and universities. 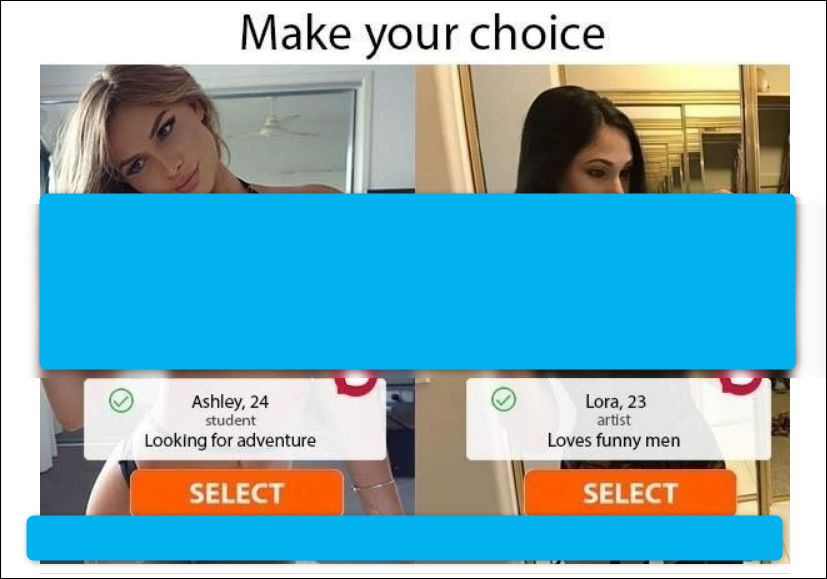 The messages arrive disguised as adult dating lures, where the user is asked to choose which picture represents someone they would like to date. Clicking on either picture causes the download to start. Once the executable (exe) file is downloaded, Hupigon is installed on the user's system. Hupigon allows threat actors to access the infected machine, has rootkit functionality, webcam monitoring, and the ability to log keystrokes and steal passwords. This version connects to a DNS server for its initial command and control communication. They also discovered that it uses the same address as another piece of malware, called "gogominer." In this particular case, the Proofpoint researchers believe the campaign is crimeware motivated, based on the distribution methods and message volumes, as well as other technical associations that were observed. Privacy Issues Emerge During Pandemic It's not bad enough that privacy issues before the pandemic were mounting. Now, with many people telecomputing from home, bosses are attempting to log how much time employees working from home are spending doing their jobs, taking privacy concerns to new heights. According to an article from NPR (National Public Radio in the U.S.), the increased incidence of working from home has led to an increase in surveillance by bosses spying on those working-from-home workers. One company required its WFH (work from home) workers to install Hubstaff on their computers. In turn, Hubstaff logged every mouse movement, keystroke, and website the workers visited. The same company required WFH workers to install an app on their phones, called TSheets, to keep track of the worker's whereabouts during work hours. Companies try to sell it on the merits of "improving team productivity and efficiency." But many WFH workers aren't buying it. Nor are privacy advocates, who are fearful that the extra surveillance of WFH workers will normalize workplace surveillance, and that the digital surveillance will continue once workers return to working "on site." The software is intrusive and unforgiving. "If you're idle for a few minutes, if you go to the bathroom or whatever, a pop-up will come up and it'll say, 'You have 60 seconds to start working again or we're going to pause your time,' " one woman said. But most workers, including this one woman, are afraid to say anything, fearful that they will lose their jobs. Meanwhile, the companies selling the software say that the demand for and usage of their software has at least tripled since the beginning of the pandemic. Of course, that means more money for them, and we all know how powerful of a motivator GREED is. Is it intrusive? Without a doubt. Is it illegal? Not at all. While there are laws (in the U.S.) that are supposed to prevent the government spying on its citizens, employers are not subject to those laws. In fact, the laws governing employers vary wildly from state to state. For many employees, it comes down to choosing between privacy and a paycheck. With so many (in the U.S.) who have lost their jobs during the pandemic lockdown, employees may feel between a rock and a hard place. They at least have a paycheck coming in because they are able to work, but they are having to forfeit a fair amount of their privacy to keep that paycheck coming in. Cloth Face Mask Hack Improves Efficiency  With many countries around the world attempting to reopen their economies after the coronavirus pandemic, many of us will be (or should be) wearing masks when out in public for quite some time to come. Additionally, such reopenings will also have to leverage social distancing to avoid spreading the coronavirus and creating a spike of new coronavirus cases. Two researchers from the Departments of Civil and Environmental Engineering and Marine and Environmental Sciences at Northeastern University in Boston, MA have come across a simple, quick, cheap and effective "hack" to increase the filtration efficiency of cloth face masks. Amy Mueller and Loretta Fernandez posted their findings in a preliminary paper (324 KB PDF) detailing their findings. The hack is simple. Just cut out a section from the leg of a pair of panty hose, and slip it over the top of your cloth mask. The panty hose layer helps filter the air passing through it, and it helps seal the mask underneath to your face better. By eliminating the leaks around the edges of the mask, the mask filtration efficiency was improved between 15% and 50%. Thus, with a cloth mask (which varies widely and wildly in quality and caliber depending on style, craftsmanship and the style of mask), the mask wearer can attain the same level of efficiency as a hospital surgical mask. With the panty hose worn over a hospital surgical mask, the hospital surgical mask goes from around 75% filtration efficiency to around 90% filtration efficiency. Since this is a preliminary paper, it has not been published yet in a peer-reviewed journal. Thus, the paper only appears on the Northeastern University website. In a FastCompany website article, they laid out step-by-step instructions for anyone wanting to give the panty hose hack a try. First, researcher Fernandez recommended using queen size panty hose, because they are easier to breathe through. Then, cut out an eight to ten inch (20cm to 25cm) section of the leg. Put your cloth mask on first, and then put on the ring of panty hose material on your head, as if you were putting on a headband. Now, slowly pull it over your face mask so that it rests just above the upper part of your mask, down to under your chin past the bottom edge of your face mask. One pair of panty hose should be able to provide at least four face mask covers. If you're going to wear a mask (and I hope all of you are, at least when you're out in public), you might as well make it as efficient as possible, so that it provides the highest level of protection possible. Y'all know that I work in a hospital as a respiratory therapist, so help me help you and everyone else by urging you to, at the very minimum, follow the advice of public health officials with regards to social distancing, wearing a mask in public, proper hand washing, avoid touching your face, and just staying away from other people as much as possible. Microsoft: $100,000 If You Can Hack This Linux Operating System  Microsoft. That old bastion of Linux hatred turned to love. [ ⁄ tongue-in-cheek] They have chosen Linux to power a line of IoT devices. Nope. Not Windows, or anything else that you typically associate with the Evil Empire. Linux. According to an article on Forbes, they are offering hackers a $100,000 (U.S.) award if they can "break it." Just as you might imagine, there are "strings" attached. First, it's not the ordinary Linux that you and I run on our computers. Instead, it's a very specific version of Linux that powers Microsoft's IoT end-to-end security platform, called Azure Sphere. Azure Sphere is a customized high-level and very compact OS, based on Linux. It is hardened with a secure application environment. Mix this with hardware, software and the cloud, and you have Microsoft's end-to-end security platform. The Azure Sphere Security Research Challenge, as it's called, was accepting applications from hackers, and those had to be submitted by May 15. Then, starting June 1, 2020, the 50 selected hackers are given three months to try to "break" it. Microsoft will supply access to Azure Sphere, as well as to other Microsoft products and services the hackers can use in their attempts. The hopes are that the hacking community -- the "white hat" hackers, instead of the "black hat" hackers" -- can help find any security vulnerabilities that were missed that would allow execution of code on the platform. Plus, if they find a security vulnerability on the "Secure World" layer, which runs below the custom Linux kernel, that allows code execution, there is another $100,000 up for grabs. Transfer Your Facebook Videos & Photos To Google Photos With Ease  Are you a North American internet citizen full of Facebook regret? Well, Facebook has made it even easier for you to ditch, ironically, Facebook. According to an article on Forbes, after a trial run in Ireland, Facebook has opened up its Data Transfer Project (DTP) to the 200 million Facebook users in Canada and the U.S. The tool allows Facebook users to transfer all of their photos and videos from Facebook directly to Google Photos. Previously, users had to click and download each image individually, one by one. Even if you don't plan on leaving Facebook, it's always a great idea to have backups of your precious photos and videos. So, to grab all of your photos and videos, head over to the DTP page. Choose your destination (Google Photos is currently the only one, thus far). In the next popup window, authorize Facebook to access your Google Photos. Select "Videos" or "Photos," then click on the Next button. You have to select one or the other, and then go back and do the other one. You cannot transfer them all at once. Then, you're done! The process runs in the background, so go do something else for a while. When you come back, you can check on its progress. A couple of caveats though. The article reports that images transferred from Facebook to Google Photos seem to have had their exif data stripped away. Any panorama or 360 degree photos -- especially the latter -- seem to get mangled in the process. So if leaving your precious photo and video memories behind has been keeping you from ditching Facebook, at least one obstacle has been eliminated. The service may or may not work in other areas of the world at this time (it is "unofficially" working in the U.K.), but it is being rolled out to other countries. So, if it's not currently available in your area, keep checking back. A "Sneaky" Way To Ditch Out On Those Zoom Meetings  With the lockdowns across the globe associated with the coronavirus pandemic, many workers have taken to conducting business over video conferencing programs, such as Zoom. In fact, Zoom has even been added to the PCLinuxOS repository. Initially, I didn't see a need -- personally -- for such a program. But then, as the lockdown dragged on, my son's teacher started using Zoom to reach out to her students twice a week. It gives them a chance to see their classmates, their teacher, and to talk to one another. So, the program I didn't think I'd ever use had ended up not only installed on my main PCLinuxOS computer, but also used at least twice a week. There are some workers who conduct a LOT of their work via Zoom. And, without a doubt, all of those Zoom meetings would seem to really drag on and on and on for what seemed like an eternity. Well, leave it to a 4th grade student to figure out how to ditch out on a Zoom call, as reported on Reddit. It's actually kind of funny, too. First, quickly disable your video (Alt+V) and audio (Alt+A). Then, quickly rename your "window" to "Reconnecting...". To the less tech savvy people in your meeting, it will appear as if you're having internet connection issues. It's probably not going to fool everyone, but it may just allow you to break away from yet another [boring] Zoom meeting. Your more tech savvy users ... probably not so much. British Museum Offers Viewing For 4.5 Million Objects 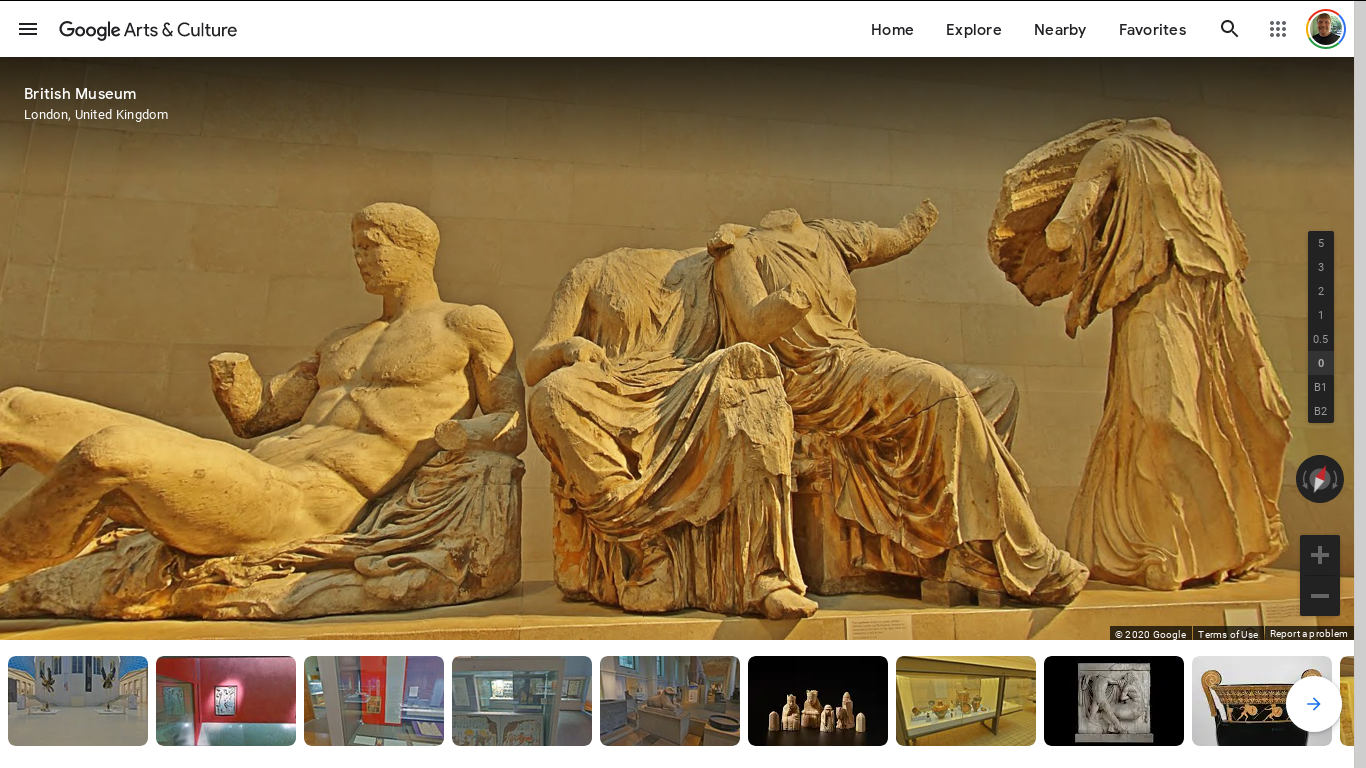 Of course, due to the coronavirus pandemic, the British Museum is closed to in-person visits. As much of a bummer that might be, it shouldn't stop you from taking a look at its collection. Especially since nearly 4.5 million objects in its collection are viewable online, from the comfort of your desk or sofa. There are a couple of ways to view the online collection. First, if you know what you are wanting to look at, just click on the "Search" button, then type in what it is you're looking for. Second, if you're not sure what you're looking for, you can click on the "Collections" menu item at the top of the page, followed by clicking on "Collections Online." The page that appears will break down the collection into broad categories. Follow those and dig through deeper parts of the collection. You will also be provided some highlights from each collection to help get you started. So, do you want to view the Parthenon Sculptures (image above)? Or would you like to view the Rosetta Stone? Use those as search terms in the search box. If you'd rather just browse, click on the "Galleries" section under the "Collections" menu item, and you can browse through the museum's collections that have been put online. You don't have to let some tiny virus keep you from exploring the wonders of the past. Plus, you won't have to put up with any other people, either. And, it's GREAT for social distancing. While it's true that it probably won't replace seeing the items in person, you can still quench your thirst for knowledge, discovery and exploration by seeing the massive collection of the British Museum online. Lenovo To Sell Thinkpads With Fedora 32 Pre-Installed  Coming very soon, according to Fedora Magazine, Lenovo will begin selling ThinkPad laptops pre-installed with Fedora Workstation 32. Lenovo will be starting with three models of ThinkPad laptops: ThinkPad X1 Gen8, ThinkPad P53, and ThinkPad P1 Gen 2 (left to right in image above). This pilot program, Lenovo's Linux Community Edition, may be expanded to other laptop models as time goes on. If you purchase a ThinkPad laptop from Lenovo's site, you can choose Fedora 32 Workstation to be pre-installed as the operating system when you order it. From Fedora Magazine: "The Lenovo team has been working with folks at Red Hat who work on Fedora desktop technologies to make sure that the upcoming Fedora 32 Workstation is ready to go on their laptops. The best part about this is that we're not bending our rules for them. Lenovo is following our existing trademark guidelines and respects our open source principles. That's right--these laptops ship with software exclusively from the official Fedora repos! When they ship, you'll see Fedora 32 Workstation." It's nice to see computer manufacturers starting to embrace Linux as an operating system option for their customers. Dell has been offering some of its computers pre-installed with Ubuntu as the operating system for a while now. I have used a number of Lenovo ThinkPad laptops in the past with PCLinuxOS installed. They have always performed admirably. They are well built, rugged, and usually packed with useful features. Pricing has not yet been determined for the laptops preloaded with Fedora 32 Workstation. Hacker Retrieves User Data From Tesla MCU Units  Let's see a show of hands. How many of you can afford to own a Tesla motor vehicle? Yep. That's what I thought. I'm right there with you. The prices haven't trickled down to levels where us mere mortals can afford them ... new or used. Quality certainly commands a price, but in the case of a Tesla motor vehicle, it's one that the vast majority of us cannot afford. One of the luxury features of the Tesla line of motor vehicles is its MCU, or Media Control Unit. Tesla's MCU makes it possible for owners of Tesla motor vehicles to stream Netflix or YouTube videos, find/connect to wifi, store phone numbers and contacts, run Spotify, and a whole host of other "fancy" things for a motor vehicle. Well, according to an article on Ars Technica, one hacker who describes himself as a Tesla enthusiast and tinkerer, obtained 13 Tesla MCUs to "explore." He purchased 12 of them from eBay, and one was given to him by a friend. From the Ars Technica article: "Each one of the devices stored a trove of sensitive information despite being retired. Examples included phone books from connected cell phones, call logs containing hundreds of entries, recent calendar entries, Spotify and Wi-Fi passwords stored in plaintext, locations for home, work, and all places navigated to, and session cookies that allowed access to Netflix and YouTube (and attached Gmail accounts). All 13 of the devices showed that their last location was at a Tesla service center, an indication that they were removed by an authorized Tesla technician. Tesla service stations remove MCUs for several reasons. Most commonly, it's to replace a faulty device or to upgrade to a newer, more advanced device model that improves the vehicle's autopilot." It's unclear what Tesla's policy is regarding MCU units that are removed or replaced, but it's certain that this isn't what they originally had in mind. Tesla didn't respond to Ars Technica's inquiries regarding the intended fate of removed MCUs. |