| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Linux Caves To Social Justice Movement |
|
by Paul Arnote (parnote) Google Photos Sports New Logo, Implements Design Changes  Google Photos services over 1,000,000,000 (yes, billion) users across the world every month. Even if it is from the evil Google Empire [bwahahahaha], there's hardly any photo service that's easier or more convenient to use. But, because it's Google, they really just can't help themselves when it comes to screwing with things that aren't broken. To start with, Google has changed the logo for Google Photos. Above is an image showing the progression of the various logos Google has used. The Picasa logo actually made sense. The opening in the middle looked like the aperture of a lens (and I'm thinking specifically of Canon's 50mm f 1.8 lens for their DSLRs, which utilizes a five blade aperture). Then came the middle logo, which some could argue (after several drinks) still resembled ... somewhat ... the aperture of a lens. Now, Google has thrust the latest logo upon us, depicted on the right. I'm not sure what flower petals have to do with photography (other than flowers make for some nice photo subjects from time to time). Nothing about the new logo reaches out and says PHOTOS to you. I would expect this kind of logo for a "Google Gardening" app. To say that it is way, way oversimplified is an understatement. As Google has shown us, you can simplify a logo too much, to the point that it loses its identity. But Google also didn't just stop with the new logo for Google Photos. They also had to mess up a perfectly functional user interface. Many common tasks, like viewing shared photos from a photo "partner," went from being just one click away, to being buried in a menu that now requires multiple clicks to access. Instead, Google decided to give photo memories -- technically called "Memories" carousel -- a larger presence. It was always there before, accessible with just one click, but now it occupies a ridiculous amount of screen real estate, with a garish appearance. Google estimates that 120 million people every month -- or roughly 10 percent or so of its monthly visitors -- access the feature every month. Sure. Let's cater to the 10 percent, and make the other 90 percent of users suffer. Because that makes so much sense. [smh!] Of course, I'll continue to use Google Photos. For me and my wife, the real attraction for Google Photos is what happens in the background. We both use Google Pixel 3 phones, which gives us unlimited storage of photos at full size and resolution (one of the "perks" of using the Google Pixel 3 phone). Most other users of Google Photos only get to store recompressed, smaller versions of their photos. Plus, almost as soon as we shoot a picture (or whenever our phones find a viable wifi network), our photos are uploaded automatically in the background. Then, we can access them from any device that can connect to Google Photos. Even though we have a DSLR and a slew of other quite capable digital cameras, we usually have our phones with us no matter where we are. And that is important when you have two active children who do cute things all day long that you want to capture in a photo. That isn't necessarily the case with any of our standalone cameras. We bought the Pixel 3's because it had the absolute best camera of any of the phones available. We know that we use the camera on our phones a lot to take pictures of the kids, so having a high quality camera was the most important consideration when we bought our new phones. Still, I wish Google would stop changing functional interfaces and features just for the sake of change. That is, after all, what it seems they like to do. Hmmm. Maybe that's what they tell the Google interns that rotate through there. Take this perfectly functioning app and let's see how much you can eff it up before your internship is over.
25 Android Apps That Steal Your Facebook Login Information
 IF you still have a Facebook account (lots of people have left the platform in recent years), there is a new threat from rogue Android apps that will attempt to steal your Facebook login credentials. Google has removed 25 of those rogue apps from the Google Play store, after French cybersecurity firm Evina identified the Facebook credential-stealing malware. Below is the full list of malware apps that Evina discovered, from the Evina website. 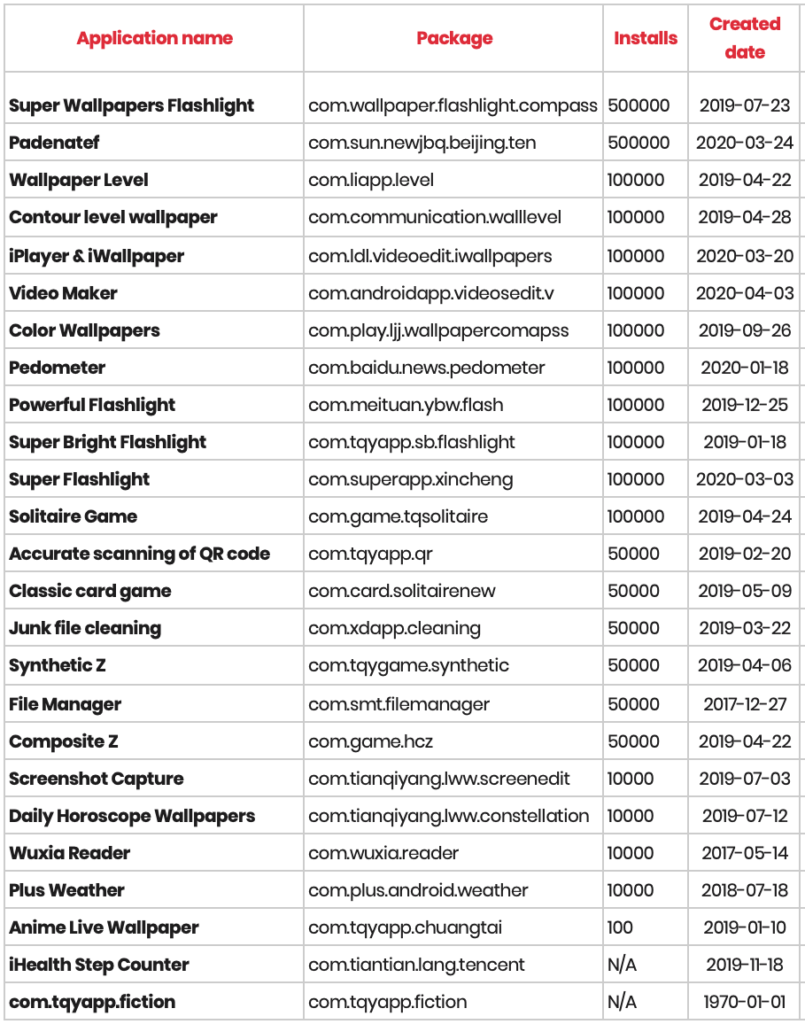 Image: Evina The list of apps include pedometers, flashlight apps, live wallpaper apps, card games, file managers, and other assorted apps. While they are functional in terms of their intended use, the malware apps will also open up a browser window with a fake Facebook login page. When the user fills in the login credentials, the login information is sent to a remote server for collection. The remote server has since been shut down. Even though Google has removed the malware from the Google Play store, users should check their Android devices to make sure the apps are not installed on those devices. Exclusion from the Google Play store will not affect apps that are already installed on devices. It is up to the end user to remove these apps that might have been installed on their devices. Stay vigilant! I've said it before, and I'll say it again: your data/information is the modern currency d'jour. Facebook Improperly Shares User Data With Developers ... AGAIN!  Just when you thought it might be safe to go into the water again, the same ol' shark that you thought was dead resurfaces, looking for another victim. Welcome to the premiere of Jaws 45 in 4D. And so it goes with Facebook, who was discovered to be improperly sharing user information -- email addresses, birthdays, language, gender, etc. -- long past the time that they should have, according to a Mashable article. Facebook, on its blog, offered a typically vague explanation. When pressed by Mashable for additional information, Facebook did not respond. If all of this sounds familiar, that's because it is. The very same situation was discovered in 2018 and 2019, and similar statements (yawn) were offered at those times for the overabundance of information given to third-party developers. Follow the links if you think you can stay awake reading essentially the same statement ... over ... and over ... and over again. It's things like this that make me happy to have NEVER been a Facebook user. Nor will I ever be. NASA: Watch 10 Years Of Solar Activity  On June 2, 2010, the Solar Dynamics Observatory was deployed. Its mission: watch the sun. While doing so, it took an image of the sun every 0.75 seconds. Over its 10+ years of observation, that amounts to over 425 million solar images. To commemorate the 10 year milestone, the SDO team put together a video of the sun from that massive amount of images that spans the 10 years of the mission so far. Each day in the video is one second of the video. It even sports a custom music soundtrack. As such, the video goes for 61 minutes. In it, you can see transits of planets, as well as solar eruptions. You can view the video here. Caution: it's quite hypnotic, and difficult to look away. Linux Caves To Social Justice Movement  If you haven't heard about the current levels of social unrest sweeping across the landscape, you must have been the lone survivor at a long lost, forgotten moon base with no way to communicate back to the "Mother Planet." The world is descending into absolute crazy madness! Well, not wanting to be left out of the "virtue signaling" mix, Linus Torvalds signed off onto removing "offensive" terms from the Linux kernel, such as slave, master and blacklist. According to an article on The Register, the removal of these terms is supposed to occur immediately, starting with the latest rc5 release of the 5.8 Linux kernel. Sooooooo ... where does all of this end? What about all of the curse words that are dispersed throughout the kernel code? Won't some puritanical sort of person take offense to the appearance of those "offensive" words? Gauging by the comments to the article on The Register (and elsewhere across the internet), the changes are not being well received by Linux aficionados. There is, to say the least, a LOT of backlash against the forthcoming changes, and most of it centers around the types of questions I asked in the previous paragraph. I Know What You Downloaded Via BitTorrent  Do you think you're safe downloading BitTorrents without a VPN? Prepare to have your mind changed in 1 ... 2 ... 3 seconds. Even though users can download perfectly legal "stuff" via torrents, such as Linux distros, BitTorrents are commonly used for peer-to-peer file sharing of copyrighted material, like music and movies, and that is where BitTorrents get their bad rap. Some ISPs even attempt to throttle the download speed of torrent downloads to discourage users from downloading torrents. Point your browser over to iknowwhatyoudownload.com. Once there, you will see your IP address listed at the top of the page, and all of the BitTorrents downloaded from that IP address listed below it. If the IP address listed is indeed yours, you might be quite surprised at the information revealed. However, if the IP address listed is one of the servers for your VPN service, then relax and know that the VPN is doing its intended job. I use a VPN, and it's quite an eye opener to see what other customers of the VPN are downloading through the VPN server. None of it points back to the actual user, but it's still quite revealing. I know. I know. Some of you are going to say something along the lines of "well, I have nothing to hide," or "I don't download torrents, so I have nothing to worry about." This isn't about whether you have anything to hide or not. This also isn't about whether or not you download torrents. This is about privacy. Why should your IP address be associated with the files you upload or download? Is it really the business of anyone else what things interest you? "No Log" VPN Provider Leaks User Database Online  Cybersecurity firm CompariTech reported that Hong Kong based, "no logs" UFO VPN has been leaking user database files for millions of its users ... daily ... due to poor security. The information includes: There are a literal TON of people who would like to snag a record of your online activity, and among them are governments, ISPs, individuals, and advertisers. It is your duty to protect your online activity as much as possible from snooping eyes. Besides storing the information in easy-to-read plain text files, none of the files were encrypted or secured in any way. The first database breach was reported by CompariTech to UFO VPN on July 1, 2020. A subsequent release of an updated and even larger database file was discovered on July 20, 2020, posted at a different IP address. UFO VPN boasts serving 20,000,000 users, and possessing "bank level security." I don't know about you, but that's not a bank I'd want to put my money into. While it's unknown just how many records were leaked, it is possible that ALL UFO VPN records were compromised. Don't worry. This gets even better. There are six Android VPN apps that appear to use the same codebase and setup as UFO VPN. They are:
The decision for UFO VPN users to leave should be an easy one. And overall, this gives VPN services a black eye. But keep in mind that VPN services that are REPUTABLE deserve your trust and business. UFO VPN should not fall into that category. There are VPN services that do not keep logs (UFO VPN just said they didn't, and the database leak proves otherwise), and that go out of their way to protect their clients' privacy and anonymity. Want to know which VPN service provider is worthy of your trust and business? Check out this "Best VPN Service for 2020" article from TechRadar. The use of a VPN is NOT the cure-all for protecting your privacy. But, it is a very important cog in a gear that makes up a whole series of things that can help protect your privacy, like enabling two-factor authentication whenever possible, making smart choices for your web browser, stop using the same passwords on multiple sites, etc. If someone or an entity wants to track your movements across the web, they will find a way. Using a good quality, trustworthy VPN service will help make tracking your activity more difficult. |