| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
How Secure Are YOUR Passwords? |
|
by Paul Arnote (parnote) It seems like this whole issue revolving around secure passwords just keeps coming up over and over and over, year after year after year. And, it's probably for a good reason: people just aren't getting the message. If they are, they aren't changing their habits and behaviors. I get it, and I bet a lot of you "get it," too. It's difficult to remember a unique, complex password for each site. This leads to password reuse between sites, even though everyone knows such behavior is bad and a poor security practice. So, just how difficult is it for a hacker to break your password using brute force? Well, that was exactly the topic of a Reddit thread recently. The graphic posted in the thread pretty much speaks for itself.  The Reddit post and graphic was by Hive Systems, using data sourced from HowSecureismyPassword.net. It is clear just by looking at the graphic what it takes to create a secure password. No one wants their password or password habits to reside in the purple areas, marked "Instantly." Even if your password or password habits reside in the red areas, this isn't much better. At the very least, you want your password or password habits to minimally fall into the orange areas. The yellow/golden areas would be even better, and you should definitely consider your data secure if your password or password habits land in the green zones. So interpret it this way. Purple equals the WORST PASSWORD you could possibly have! As in, DO NOT use a password habit that would place your password in the purple zone. The only thing easier for a hacker to access your data is to not have any password. Red would be a BAD password that is easily broken, often within minutes to hours. Orange areas represent a MEH password that takes days to years to break, depending on how complex your password is. Yellow/golden areas would represent a "NOT BAD" password that would take years to break. Green equals a SECURE password that would take a hacker millions, billions, trillions, or quadrillions of years to break using brute force tools. Taking a look at the columns, using all numbers to compose your password definitely would not be a great choice, if you want to protect your data. Using just lowercase letters, things start to get a bit better. It makes sense. There are only 10 numbers (0-9), but 26 letters (at least in the English language) to choose from. So, with more letters than numbers to choose from, it's easier to get a wider variety of possible choices. Start mixing uppercase and lowercase letters, and all of a sudden your choices expand to 52 letters to mix and match. Add numbers to that mix of uppercase and lowercase letters, and you now have 62 characters to mix up in your password. To get the best protection, mix up uppercase and lowercase letters, numbers, and symbols to create your password. It should also be apparent, from looking at the graphic above, that the longer your password is, the harder it is to break using brute force methods. Brute force attacks against your password use tools specifically designed to chip away and reveal your password. Trust me, it isn't just some hacker sitting in a dark corner of a room making random guesses and entries to try and decipher your password. Why work that hard when you don't have to? Plus, that would more involve pure luck than brute force. It's also why users have been advised -- for years -- to avoid using the names of children, pets, parents, spouses, favorite TV shows/bands/actors/characters/movies/etc., birthdays, anniversaries, and any other easily determined personal facts as the basis for your passwords. Brute Force Tools Let's preface this section of the article with this statement: we're not advocating for anyone using these tools for any illegal hacking activities. We also are not "informing" hackers of anything that they don't already know about. This information is freely and readily available to anyone curious enough to search, with a very, very simple internet search. But, if you know the tools hackers have at their disposal, the better prepared you are to protect yourself, your accounts, and your data. It also perfectly frames just how far hackers are willing to go to gain access to YOUR information. Of course, it depends on just how determined a hacker is to gain access to your information. If you make it too difficult, there's a high probability that they'll just move on to the next poor sucker, who didn't take the time to secure their data with a good password. So, let's take a look at some of the tools available to hackers, along with describing their primary purpose. You can get a more complete description by visiting the InfoSec article here. Aircrack-ng is a tool that, believe it or not, is in the PCLinuxOS repository. The tool is used to crack the password for wireless networks. John the Ripper is a tool that was originally created for Unix systems, but it now supports 15 different platforms, including Linux, Windows, DOS, BeOS, and others. This popular tool uses several different cracking methods, and can help identify weak passwords, or to crack passwords. Rainbow Crack is another popular tool that generates "rainbow tables" while performing the attack, which can help reduce the amount of time it takes to crack a password. Cain and Abel is yet another popular tool by cracking various kinds of passwords by performing brute-forcing attacks, dictionary attacks, and cryptanalysis attacks. Interestingly enough, some virus detectors label it as malware, and block it. LOphtCrack, SAMInside and Ophcrack are quite capable tools designed to crack Windows passwords. Crack is one of the oldest cracking tools, designed for the UNIX systems. Hashcat claims to be the fastest CPU based password cracking tool. The free program is available for Linux, Windows, and MacOS platforms. Hashcat supports various hashing algorithms including LM Hashes, MD4, MD5, SHA-family, Unix Crypt formats, MySQL, Cisco PIX. It supports various attacks including Brute-Force attack, Combinator attack, Dictionary attack, Fingerprint attack, Hybrid attack, Mask attack, Permutation attack, Rule-based attack, Table-Lookup attack and Toggle-Case attack. DaveGrohl is a popular brute-force cracking tool for the MacOS. Ncrack is a password-cracking tool for cracking network authentications. Available for Linux, BSD, Windows and MacOS, it supports various protocols including RDP, SSH, http(s), SMB, pop3(s), VNC, FTP, and telnet. THC Hydra is known for its ability to crack passwords of network authentications by performing dictionary attacks against more than 30 protocols, including telnet, ftp, http, https, smb and more. It is available for various platforms, including Linux, Windows/Cygwin, Solaris 11, FreeBSD 8.1, OpenBSD, OSX and QNX/Blackberry. Of course, this listing is just a handful of the available tools that hackers can/will use to crack your password, network or computer. Some of the ones available are free, while others are available for sale. So What's "Best Practice?" By "best practice," we mean "how do you best protect yourself?" We've covered password security here in The PCLinuxOS Magazine so often and so many times that I've lost count. Even if I try to count, I'm sure I'll forget about or omit an article where we talked about it. Use the new search page on the magazine's website to search for "password," and you'll see what I mean. It seems to go on forever. However, looking at the graphic at the beginning of this article, it's apparent that length trumps complexity. That is, a password with 18 characters, using all lowercase letters, will take 23 million years to crack. Using the same schema, but with only 16 characters, it would take 34,000 years to crack. Any hacker trying to crack your password would be turned to dust before the password is successfully cracked. As we published in the January 2018 issue of The PCLinuxOS Magazine, complex isn't necessarily best. Here's an excerpt from that article: In years past, we thought this was an easy one to answer. But in August, 2017, Bill Burr set the password world on its ear. See, Bill Burr was the employee of the National Institute of Standards and Technology who released a report in 2003 advocating for the use of special characters, mixed case letters, and numbers in a password in the hopes of fooling/foiling hackers. Literally overnight, his paper became password policy. It became the FINAL WORD on passwords. (Read the full USA Today article here.) But in August, Bill Burr stated in a Wall Street Journal article, "Much of what I did, I regret." His report wasn't based on any real-world password experience or expertise. Rather, it was based on another paper written in the 1980s. But in the interim, it became entrenched as THE holy password gospel. Bill Burr now suggests that users string together four common and random words, instead of the "standard" mix of uppercase and lowercase letters, numbers, and special characters. The XKCD comic shown here sums up nicely why and how this is better. 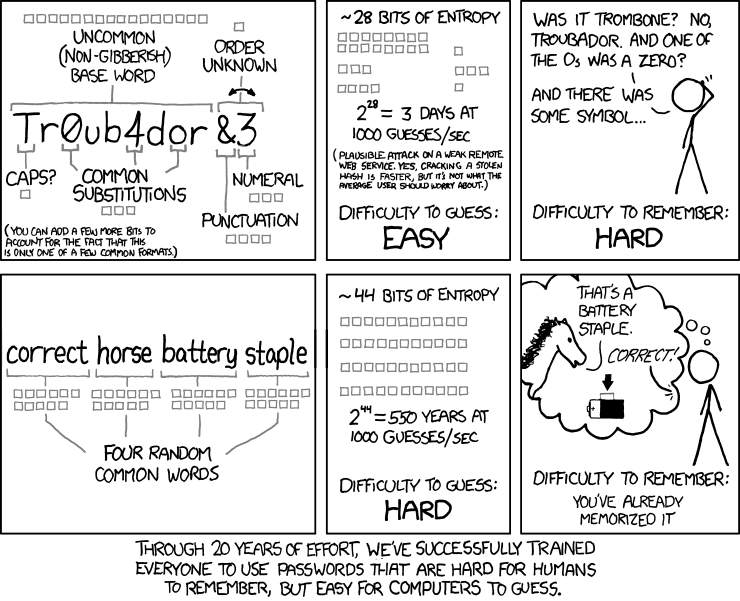 But don't expect to see websites and other entities jump aboard with this new revelation, as many of them will still require the "standard" mix from that 2003 report that has become password gospel. Those "recommendations" are firmly entrenched in the password world as key tenets of the "religion." After all, it took us nearly 20 years to get to that point, and it's likely to take twice as long (or more) for those erroneous thoughts to erode, despite evidence that there is a better way. So many bad ideas take so long to go away. Still, it's apparent that many users are sloppy with passwords. This is evident from the 2017 Worst Passwords list. So, there are ways to help protect yourself with strong passwords. The fact remains that there is no uncrackable password, given enough time. But the goal is to make it sufficiently difficult to crack that the hackers will simply give up and move on to the next poor sucker in line, leaving your data safe. However, you're going to find situations where the "old method" of using a mixture of lowercase letters, uppercase letters, numbers, punctuation, and symbols are required. These guys never got the message, or chose to ignore it altogether. Even with the example given in the comic strip, I'm comforted by the fact that any hacker would have spent 500 years or more staring at the lining of his coffin before my password would have been cracked by him or her. Personally, I'm OK with that level of protection. Use a password manager. There are a couple of excellent choices here. If you're looking for a browser-based plugin that is exceptional, take a look at LastPass. You can even set a master password to access your stored passwords. Just don't ever forget it, because without it, no one at LastPass will be able to retrieve your list of passwords. LastPass will also generate unique, secure passwords for you, if you so choose. If you prefer a locally-stored solution, take a look at KeePassX, which is in the PCLinuxOS repository. But, if you ever have a hardware failure, you may be left in the position of losing all of your stored passwords. Don't reuse passwords on different sites. Password reuse is a HUGE weak link in password security. If a site gets hacked and your password is revealed to the hackers, using that same password elsewhere also makes your data on all the other sites where you used that same password vulnerable. If you feel compelled to reuse a password (as in you just can't help yourself), then you can (as we've reported before in this magazine) use a common base password, altered slightly for each site you log onto. For example, let's say your base password is billspassword20. Use it, with some representation of each site you use it to log into, appended to the end, using the same schema. So, let's say you will append the name of the website, but omit all vowels from the website name. Using that method, "google" will become "ggl," which gets appended to the end, or billspassword20ggl. Or, it becomes billspassword20^ggl if you decide to insert a symbol between the base password and the "name" of the website you are creating a password for. You can come up with whatever method works best for you, that only you know. A password schema used by one of the "tech guys" at the company where Meemaw works uses song lyrics with the spaces left in, and some characters changed to numbers or symbols. He says it's easy to remember. Whatever schema you use to come up with your passwords, stick with it, be consistent ... and don't tell ANYONE your "method." Summary I definitely feel like a broken record that keeps repeating itself over and over. The security of YOUR data and accounts is fully YOUR responsibility. No one else is going to give two hoots about the security of your data and accounts. YOUR data and accounts -- your private information -- IS. THE. NEW. CURRENCY. OF. THE. TIMES. Hackers are more eager than they ever have been to get their hands on it. Forget the thoughts that some users have, thinking that THEIR data doesn't hold any value to anyone else but them. Your social security number, government ID number, birthdate, name, likeness, and everything else about you can be used by not-so-benevolent individuals to create false identities, behind which they will hide to carry out their crimes and misdeeds. Forget the thoughts that go something like, "Well, I don't have anything to hide." This has nothing to do with whether or not you have anything to hide, or if you've done (or are doing) anything improper. This is about protecting your privacy from not only the prying eyes of overzealous, overreaching government agencies, but also from those with nefarious motives in mind. It's YOUR data. It's YOUR information. It's up to YOU to protect it. |





