| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: The 411 On 1.1.1.1 DNS Service |
|
by Paul Arnote (parnote)
Google Shutters Short Link Service Google is shutting down the short link service that it launched in 2009, named goo.gl. They cited a proliferation of other short link services, such as ow.ly and bitly. They also cited "changes in the way people find content on the web" (whatever that means). The service is being shut down in three stages. First, after April 13, anonymous users and users who've never used the service before will not be able to use the service. Developers will only be able to use the service if they work on a project that has accessed the service before May 30. The goo.gl management console will continue to work until March 30, 2019. After that date, all short links previously made with goo.gl will continue to redirect to the intended web page. Google has a long, long, long history of shutting down popular services ... or retiring them ... or abandoning them ... or pulling the plug before they've ever caught on. In fact, the list of services that Google has shut down is way longer than the services they offer. So no one should be surprised by this move. So, that leaves the question of what other short link services remain? Let's take a look at a list, excerpted from The Intelligent Economist. ow.ly - Previously free for use by everyone and anyone, use of this short link service now requires signing up for a free Hootsuite Dashboard account. So, it's still free, but it just requires signing up for a free account. bitly - Bitly offers a free version of their URL shortening service. No signup necessary, but creating an account allows you to manage links quickly and change the URL from http://bit.ly/Jhc38q to http://bit.ly/Intelligent. You can only use keywords that other people have not taken, though. TinyURL - TinyURL is a simple shortener that requires no sign-up and allows users to customize the keyword. The service is free to use, but there are no analytics. Tiny.cc - Tiny.cc is a popular and free service that can log basic statistics for each short URL. Tiny.cc also allows you to create a custom URL. is.gd - A simple and very short URL is.gd also allows you to customize your short URL. No sign up required. You can log statistics from their links. soo.gd - soo.gd is a free and easy to use link shortener that allows you to customize the suffix of the URL. However, there is no analytics. It also produces a QR code for your shortened link. s2r.co - s2r.co is a service that offers no statistics and no customization. However, no sign up required. These are only the free services. There are other short link services that require you to pay, and we have excluded them from the list here. It's doubtful that you'll be unable to find a short link service that accomplishes what you (or most users) need among the free services that are available. So, Google's assessment that there is a proliferation of short link services is accurate. We've presented seven such free services here that should more than replace the role played by goo.gl. 
The 411 On CloudFlare's 1.1.1.1 DNS Service Like just about everyone else on the internet, I initially thought that the announcement of this new DNS (domain name server) routing service was an April Fool's joke. Yes, it was announced on April 1. Surely, this must be one of those April Fool's jokes. But no, it's real. And when you think about it, this new DNS routing service was announced on the most appropriate day imaginable: 4/1, since the DNS address is four ones -- 1.1.1.1. CloudFlare, a cloud-based website acceleration service, working in cooperation with APNIC (Asia-Pacific Network Information Centre), announced the new (and free) DNS routing service, 1.1.1.1. It is a drop in replacement for services provided by ISPs, OpenDNS or Google, as well as free WiFi hotspot providers. In any of the alternatives listed, they could log your access history for targeting advertising, or sell it to third parties who'll do who-knows-what with it. The DNS routing service runs atop CloudFlare's content delivery network, which is used by millions of websites to speed up loading times by caching content in multiple discrete locations around the world. As a result, Prospect One's DNSPerf benchmark ranks the query speed of 1.1.1.1 just a tad over 14ms. OpenDNS, ranking second, comes in at just over 20.6ms. Google came in third with its 8.8.8.8 DNS routing service, at just over 34.5ms response. 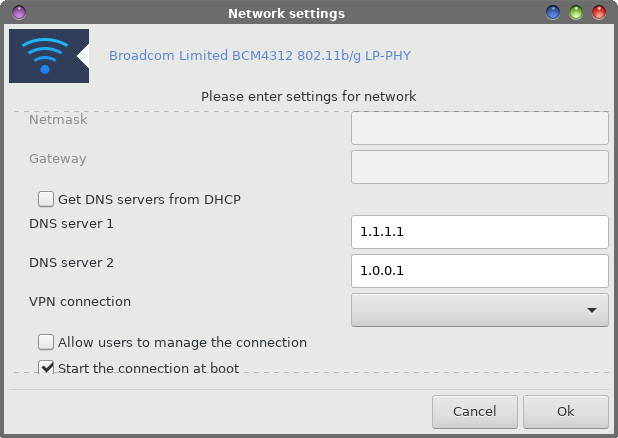 Setting it up in PCLinuxOS is very easy. Open the Network Settings dialog for the network device you want to modify. Scroll down in the settings dialog until you come to the "Get DNS servers from DHCP" setting. Uncheck the checkbox, and put 1.1.1.1 in the DNS server 1 field, and 1.0.0.1 in the DNS server 2 field. Then select OK to save your changes. Disconnect, then reconnect, your current network connection for the changes to take effect. So, what's the advantage? Well, CloudFlare's DNS resolver is setup to be the most secure DNS server on the planet. Logs are kept for debugging and data analysis, but deleted within 24 hours. An outside auditing firm has even been hired to insure that CloudFlare complies with the "no user data logs" pledge. What data is collected -- albeit for less than 24 hours -- is stripped of any user identifiable information. Contrast this with your local ISP, who is seeking to monetize your DNS data, especially in the U.S. since the FTC nullified the Net Neutrality rules. This is especially true if you use any of the "big" carriers, such as AT&T, Comcast, Time Warner (I think they're calling themselves "Spectrum" this week), Verizon, Charter, and a whole host of other large carriers. Since the repeal of the Net Neutrality rules, they are now free to sell your collected data (and they have a literal ton of it) to the highest bidder, all in an effort to target ads to you.  Typically, your DNS data records EVERY SINGLE SITE you visit, regardless if the site is a secure site or not (secure sites typically have a green padlock on your address bar). This is especially true if you are using your ISP's DNS resolver, which is the case when you leave the "Get DNS servers from DHCP" option checked in your network configuration. When we uncheck that box and insert CloudFlare's DNS resolver, we prevent our ISP from collecting all of that DNS data on us. Your ISP *does* maintain DNS logs that go back who knows how far, while CloudFlare does not maintain logs. CloudFlare has the 1.1.1.1 address on "loan" from APNIC, who manages allocation and registration of IP addresses for the Asia-Pacific region. Partnering together, APNIC will conduct a study of the DNS traffic in order to measure the efficacy of caching systems, and to study potential new mitigations against DNS-powered denial of service (DoS) attacks. APNIC is also sensitive to the security needs of users. Here is an excerpt from their statement: APNIC is acutely aware of the sensitivity of DNS query data. We are committed to treat all data with due care and attention to personal privacy and wish to minimise the potential problems of data leaks. We will be destroying all "raw" DNS data as soon as we have performed statistical analysis on the data flow. We will not be compiling any form of profiles of activity that could be used to identify individuals, and we will ensure that any retained processed data is sufficiently generic that it will not be susceptible to efforts to reconstruct individual profiles. Furthermore, the access to the primary data feed will be strictly limited to the researchers in APNIC Labs, and we will naturally abide by APNIC's non-disclosure policies. The service is available to users of Windows, Linux, OS X, or iOS. At this time, Android devices require a static IP address in order to manually configure the DNS. You can read more about CloudFlare's new DNS service here.  IoT Invades The Loo! I know I've told you previously how my mind reads IoT, by placing a "di" after the first "I" in the acronym. Well, now there's one less place you can go to get away from these pervasive "connected" devices. Yes, that's right. They've even started invading public restrooms. Someone obviously saw a problem and thought that IoT was the way to solve it. I'd have never seen this problem, since I don't fly (I have and don't mind it, but am vehemently opposed to the groping that's necessary to board a flight). And, since I don't fly, I never go to airports. But, it seems that lots of people who do fly tend to avoid using the bathrooms aboard planes that are crammed into half the space of a small closet. That means when a plane lands, the first destination for the travelers after deboarding a flight are the airport's public restrooms. This can create lines -- sometimes long lines -- at the restrooms as travelers queue up to relieve themselves. Now, a company calling itself "Tooshlights" has attempted to improve the situation by developing a traffic management solution for restrooms. A red light appears over a stall when it is occupied and in use, a green light appears over a stall when it is available, and a blue light appears when a handicap stall is available. The light changes color when the latch on the stall door is locked or unlocked. The latch wirelessly communicates with the overhead light to change colors based on the availability of the corresponding stall. Women, when they go to a public restroom, tend to view a closed stall door as proof that it is occupied and unavailable. This can cause some unused stalls to go unused in times of need. Men, on the other hand, tend to casually look under the stall doors and between the cracks of the door, while gently pushing on the door, to see if a stall is occupied. But, since men are the worse about locking the stall door, pushing on the stall door can lead to some rather embarrassing encounters. It is hoped that the feedback of the lights changing colors will help remind men to use the stall latches. Expect to see these "improvements" at LAX, in the American Airlines Terminal 4, and in United Airlines Terminal 7, before expanding throughout the entire airport. It is also expected to be installed in the busiest airport in the world, the Hartsfield-Jackson Atlanta International Airport very soon. Of a positive note, the data collected (yes, they are collecting data from these devices) is used to help keep the restrooms cleaner by monitoring how busy the restrooms are and when they are the busiest. On the negative side, I only wonder how long it will be before these devices (and its data) are used for more nefarious uses, or how long it will be before some perv links the signal from the latches to trigger hidden cameras in the ceiling. Over 20,000,000 Chrome Users Victims Of Fake Ad Blockers If you, or anyone you know, have installed one of the following ad blockers in Google Chrome, you should immediately remove them from your system, according to Andrey Meshkov, co-founder and team lead of Adguard:
This was reported on the Adguard blog, on April 17, 2018. Growing ever popular among crooks, the taking of honest ad blockers, inserting malicious code, and re-releasing them under slightly different names has grown considerably during recent times. As you can see from the names of the fake ad blockers listed, the names are believable and seem innocent. Certainly, no one (except the advertisers and those collecting money from the display of ads) wants to see any ads as they travel around the interweb. So, casual users who may not know or realize the difference between bonafide ad blockers and the imposters are most at risk. According to the blog entry, this is how one such imposter works. First, It hides malicious code inside a well-known javascript library (jQuery). Then, this code sends back to their server information about some of the websites you visit. It then receives commands from the command center remote server. In order to avoid detection, these commands are hidden inside a harmless-looking image. These commands are scripts which are then executed in the privileged context (extension's "background page") and can change your browser behavior in any way. Basically, this is a botnet composed of browsers infected with the fake adblock extensions. The browser will do whatever the command center server owner orders it to do. Meshkov goes on to blame the lax moderation of Google Play Store apps for their proliferation. Since the discovery of these fake ad blockers, they have all been reported to Google, and all have subsequently been removed from the Google Play Store.  An Ass-tonishing Solution From the "you can't make this sh ... er, stuff ... up" department, researchers think they may have found a solution to two problems facing humans on long space flights, like to Mars and beyond. Those two problems are transporting materials and dealing with the solid waste produced by humans in space. A team of researchers from the University of Calgary have devised a process called "Astroplastic." It produces PHB (polyhydroxybutyrate), a plastic, from solid astronaut waste (poo). That plastic can then be used to make 3D printed objects for use by the astronauts. The process takes genetically modified E. coli bacteria to make PHB plastic granules. The process uses an ongoing fermentation and extraction process to create a continual PHB supply, suitable for use by a 3D printer aboard the spacecraft. The astronauts' fecal matter, extracted from the vacuum toilet, is left to ferment for three days, where the volatile fatty acids (VFAs) are allowed to increase. It is those VFAs that they E. coli bacteria will chow down on, producing the PHB plastic. You can read the full PDF report on the process here (PDF). While the original plan is to use it to make tools, like ratcheting wrenches, for the astronauts to use to make necessary in-flight repairs, let's hope that they don't use this poo-plastic to make eating utensils and toothbrushes.  New Cryptomining Malware Doesn't Need An Active Browser Session Reported in an April 2018 press release from Check Point Software Solutions, Ltd.: Check Point® Software Technologies Ltd. (NASDAQ: CHKP), a leading provider of cyber-security solutions globally, has published its latest Global Threat Index for the month of March, revealing a surge of cryptomining malware attacks -- specifically, an endpoint cryptomining malware known as the XMRig variant. First seen in the wild in May 2017, XMRig entered Check Point's top ten most wanted malware index (8th) for the first time during March 2018, after a 70% increase in global impact. By working on the end point device rather than the web browser itself, XMRig is able to mine the Monero cryptocurrency without needing an active web browser session on the victim's computer. "Cryptomining malware has been quite the success story for cybercriminals, and XMRig's rise indicates that they are actively invested in modifying and improving their methods in order to stay ahead of the curve," said Maya Horowitz, Threat Intelligence Group Manager at Check Point. "Besides slowing down PCs and servers, cryptomining malware can spread laterally once inside the network, posing a major security threat to its victims. It is therefore critical that enterprises employ a multi-layered cybersecurity strategy that protects against both established malware families and brand new threats." In March, Coinhive retained its most wanted spot for the fourth consecutive month impacting 18% of organizations, followed by the Rig EK Exploit Kit in second (17%) while the Cryptoloot miner was third (impacting 15%). XMRig was the 8th most common malware variant, impacting 5% of organizations. What makes this unique is that previous cryptomining malware exploits required an open browser session to perform its deeds. This exploit eliminates that "need." XMRig, by itself, is not malware. It is commonly used to mine for Monero cryptocurrency. But the version now being seen has been "weaponized" to mine for cryptocurrency without requiring an active and open browser session. According to a TechRepublic article, "It appears to be spreading via file sharing websites like DropMeFiles, 4Sync, and Rapid Files, which all feature public linking to downloads. Palo Alto Networks also reported instances of internet users being infected by malicious Adfly advertisements as well. "Once installed, the XMRig malware uses proxies to hide its traffic and obscure the wallet destinations, and it also adds the infected PC to Nicehash, an online marketplace where users can sell their processing power for use by cryptocurrency miners."  Private Internet Access To Open Source Client Code Over the next six months, Private Internet Access will release all of the code for its VPN client to the open source community. The first piece of code has already been released on GitHub for Java tinkerers to start working with. That first code piece is PIA's Chrome extension. Even as a paying customer, I didn't know that PIA had a Chrome extension. But then again, I'm also not fond of Chrome, either. So, it makes sense that I wouldn't have known about the Chrome extension. Plus, the Chrome extension only protects your data in the browser, and has no effect on other programs that may running and connected to the web, so it's of limited value anyways. Here is their announcement from their blog page, dated March 15, 2018: Today marks the start of an exciting shift over here at Private Internet Access. As long-time supporters of the Free and Open Source Software community, we have started the process of open sourcing our software, and over the next six months we will be releasing the source code for all our client-side applications, as well as libraries and extensions. We are extremely grateful to the Free and Open Source Software community for creating the foundations of the Internet as we know it. And while we may be late to the party, we are looking forward to furthering our work with a movement that aligns with our own passions, on both a personal and professional level. We believe that the shift to open source is the right move for a privacy-focused business, and recognise that code transparency is key. We appreciate that our code may not be perfect, and we hope that the wider FOSS community will get involved, provide feedback, feature requests, bug fixes and generally help provide a greater service to the wider privacy movement. Today, we are opening up the first of many repositories, the chrome extension, that allows users to access our network of proxies from their web browser. The chrome extension also boasts additional privacy and security features such as disabling the microphone and camera, blocking flash and ip discovery through WebRTC, and can also automatically block ads and tracking through PIA MACE™. Please note that the extension will protect traffic from the browser only and will NOT offer any protection when using other applications. "Let's continue to fight the good fight. Freedom is an earned right, and we must continue to re-earn it everyday. As the world continues to fight, Private Internet Access will be there. In crypto we trust." -- Andrew Lee, Private Internet Access Founder, and long-term FOSS contributor. Head over to GitHub, check out the repo and get involved! You can find us in #privateinternetaccess on chat.freenode.net if you have questions, comments or simply want to find out more about what we are up to. Our longer term goal is to release all our code into the open, and we hope that you will join us on our journey. We have some exciting things planned, and would love to hear from you if you want to get involved ... and don't forget to keep an eye on our blog and/or social media as we will be throwing some exciting launch events further down the line. It should come as no surprise that we think that open source is awesome, and as long-term consumers of open source we are really happy to now be in a position where we can contribute back. If you have any questions or comments, please do drop us a line to opensource@privateinternetaccess.com, we look forward to speaking with you and hope that our transparency will ensure that you have some peace of mind. According to The Register, "There is no schedule for when the rest of the client-side software will be made available, although PIA is a user of the OpenVPN application and conducted an audit of that code last year." As a paying customer, I have to admit that PIA's client software has been problematic, especially when it comes to updates. Not too long ago, I attempted to perform the recommended update, only to find that the "update" would not complete installation. So, at that point, I switched over to using PIA via openvpn. Having PIA's software not properly install was the best thing to ever happen for me (regarding using PIA), since it forced me to use their service with openvpn. The openvpn route is easier, faster, and a lot less resource and memory hungry than their client software. Here's to hoping that the open-sourcing of PIA's client software will help improve that software. I also hope the it will allow inclusion of the PIA client software in the PCLinuxOS repository, for those who might be interested in using the service via their client software. As for me, I'll keep using the openvpn access that they provide. |