| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Yahoo Pulls The Plug On Messenger |
|
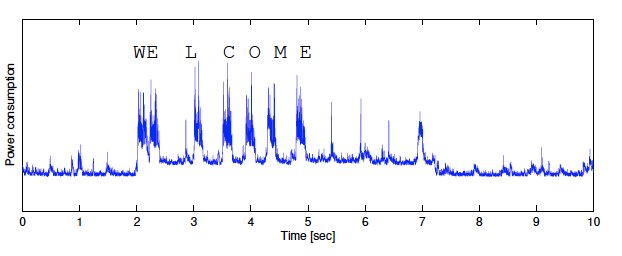
by Paul Arnote (parnote)  EU Copyright Reform Proposal You knew it had to be too good to last. The EU Parliament made a splash last month when it started enforcing the GDPR (see last month's magazine). The GDPR was a good thing that addressed user privacy with a law that actually had teeth and was enforceable. They must not have been able to help themselves. They just had to go and do something stupid. Right on the GDPR's heels comes a new copyright proposal that creates a "link tax", and "places a new general obligation on internet platforms and websites to pre-monitor user content on their website for copyright infringements." You know that interesting news story or photo you share with your friends and colleagues on social media? Well, under the new copyright proposal, you would need to get a license from the news outlets just to share it. That's referred to as the "link tax" part of the new proposal. But let's say you share a Cold War era headline; that original publisher may have long ago gone out of business, and there would be no one to provide that license. Oh, don't worry, because if you go ahead and share that headline, you'll be in violation of the new copyright proposal. It would also require all internet platforms to scan user content for any possible copyright infringements. Without saying exactly how this should happen, it's unclear if websites need to develop in-house procedures for scanning user content, or hire outside companies to do it for them. YouTube has tried to "roll their own," but faces frequent criticism for wrongly flagging original content as being a copyright violation. It's a quite complicated task that is next to impossible to do. In either case, it's going to be costly, and possibly costly enough to force some (many?) out of business. According to the EFF, "Under Article 13 of the proposal, sites that allow users to post text, sounds, code, still or moving images, or other copyrighted works for public consumption will have to filter all their users' submissions against a database of copyrighted works. Sites will have to pay to license the technology to match submissions to the database, and to identify near matches as well as exact ones. Sites will be required to have a process to allow rightsholders to update this list with more copyrighted works." C'mon, EU Parliament! You're doing this all wrong! Copyright laws have already become way, way too onerous, and extend "protections" for far too long of a time. The copyright laws already stifle innovation, expression and the sharing of knowledge. To do what you propose doubles down on that. You should be easing copyright laws to foster innovation, expression and the sharing of knowledge. Y'all are going about this completely wrong! The committee vote was June 20, and the full parliamentary vote should take place either in early July or late September. Let's all hope that this vote fails miserably, or the failures will be upon us like a wet towel in the middle of a humid summer. .png) Google Kills Off Inline Chrome Extension Installation In an effort to improve security and transparency, Google is killing off inline installations of Chrome extensions. Starting in June 12, new extensions are unable to access the Chrome Web Store call function that would allow them to launch an inline install. Instead, users will be redirected to the Chrome Web Store so they can take a look at the extension before choosing to install it.On September 12, inline installation will be disabled for existing extensions, as well. Users will be directed to the Chrome Web Store to install the needed browser extension. Starting with Google Chrome 71, due out in December, 2018, the inline install API will be removed from the browser altogether. If Google really wants to improve security, let's hope they take a different approach to the Chrome Web Store than the hands off approach they have taken with the Play Store for Android. The latter is chock-full of malware-laden apps. If the Chrome Web Store fares no better, it's going to be up to the end user to thoroughly check out extensions to insure security, which is going to be hit-or-miss at best.  Yahoo Pulls The Plug On Messenger After 20 years of service, Yahoo! is pulling the plug on Yahoo! Messenger. After July 17, 2018, Yahoo! Messenger will no longer exist. Initially released as Yahoo! Pager in March, 1998, its name was changed to Yahoo! Messenger one year later. If you've been around computers for any length of time, you have probably used Yahoo! Messenger to chat with friends and family, both near and far. It quickly became a very popular program, and "the" program to use to chat it up. Yahoo! has slowly been taking features away over the years. In August, 2012, all public chat rooms were shut down. You used to be able to use Pidgin and Kopete to connect to the Yahoo! Messenger service. As of March, 2016, only Android, iOS and web browser clients were allowed, and you could no longer connect with non-Yahoo! programs, such Pidgin and Kopete. If you're interested, you can download your chat history to a personal computer for the next six months. You can click here, sign in, select a verification method and enter the account key, click "download," and enter the email where you want the file sent. After you've downloaded your chat history, Yahoo! recommends deleting the Yahoo! Messenger program from your computer or device. While there currently is no replacement for Yahoo! Messenger, but there is a new invite-only group messaging app currently in beta, called Yahoo! Squirrel. If you're interested in participating in the beta for Yahoo! Squirrel, you can request an invitation at squirrel.yahoo.com. So long, Yahoo! Messenger! We had some fun and interesting times!  Your Smartphone Battery May Be Spying On You Believe it or not, your smartphone's battery may be offering up information about what you do with your smartphone, based on your battery's power consumption. A study by researchers from the University of Texas in Austin, the Hebrew University of Jerusalem, and the Israel Institute of Technology described how rigged smartphone battery can collect information from the power-hungry components of your smartphone to reveal the activity of the user. The "rigging" consisted of implanting a microcontroller to sample power flowing in and out of the battery at a 1 kHz sample rate.
According to the report, the battery is a very attractive attack vector because "all the phone activity is exposed." An attacker can correlate power flows with a keystroke, the context of the keystroke (like if someone is visiting a website at the time) and "the events that preceded or followed it," such as taking a photo or making a phone call. Just what we needed! I have enough to worry about from all the three and four letter government agencies invading my privacy. Now, all of a sudden, those budget priced phone batteries from China on eBay don't look so attractive. How do I know that cheap battery doesn't contain one of these chips? That's part of the problem; I don't.  Gmail's New Design, Like It Or Not Well ... someone uncaged Google's summer interns and turned them loose, much to the chagrin of those of us who actually might try to use Google's products. This time around, changes are coming to Gmail.Oh, don't expect much change in functionality. After all, it is email. There's not a whole lot you can do with tried and true email. That part is pretty much set. But what Google is f-f-f-f-fidgeting with is mostly cosmetics and aesthetics. There are a few new features, such as offline and confidential mode, but those modes will be turned off by default when the new version reaches general availability in July. Gmail's update focuses on AI-powered productivity improvements, such as suggested replies, as well as collaboration, and security. It also integrates Calendar, Tasks, Keep, and Add-ons so they can be used from within Gmail. The rollout has been gradual over the past month or so (it just became available to me at the end of June). It will continue to roll out over the month of July, but users can opt out of the "new" Gmail. However, come October, the option to opt out goes away, and everyone using Gmail will be forced to use the new Gmail interface. So what are my first impressions, you might be asking? Well, as expected, nothing new that initially appears to be of any substance. And, yes, lots of cosmetic changes. But the interface feels much more sluggish as things fade in and out under your mouse cursor. There definitely is a lag time as I move the mouse around the Gmail screen, not with my mouse, but with the highlighting of the objects below my mouse cursor. Since I just made the switch to the new Gmail as I was writing this article, I've only been using it for less than an hour. But sluggish definitely is my first impression.  Microsoft Drops Win7 Support For Some CPUs Yes, I know. I'm acutely aware that this is a Linux magazine. But I also know that there are quite a few PCLinuxOS users who either run Windows 7 in VirtualBox, or who dual boot PCLinuxOS with Windows 7. But the CPUs that Microsoft is dropping support for with Windows 7 is what struck me as odd: Pentium III CPUs. Really? I never realized that Windows 7 would even run on a Pentium III, available from around the turn of the century. Don't get me wrong ... I loved my P3 computers, even though they all maxed out at 512MB RAM. I even still have some of them around here, in working condition. But I wouldn't have even thought of attempting to install Windows 7 on any of them. More specifically, Microsoft is dropping support for CPUs that don't include the SSE2 multimedia instruction set. That would include the Pentium IIIs. The issue first arose in March of this year when Microsoft sent out an update that refused to complete because the computer didn't support the SSE2 multimedia instruction set. Of course, all the P3 CPUs are 32 bit processors, and PCLinuxOS abandoned the 32 bit version some time ago. So, it's highly unlikely that anyone reading this is dual booting PCLinuxOS and Windows 7 on a P3 computer. But, that's not to say that some of you might not be running 32 bit Windows 7 in VirtualBox. I can only imagine how slow and disk-intensive running Windows 7 on a computer with a P3 CPU would be. The things you learn ...  Wi-Fi Alliance® introduces Wi-Fi CERTIFIED WPA3™ security Wi-Fi Alliance® introduces Wi-Fi CERTIFIED WPA3™, the next generation of Wi-Fi® security, bringing new capabilities to enhance Wi-Fi protections in personal and enterprise networks. Building on the widespread adoption of WPA2™ over more than a decade, WPA3™ adds new features to simplify Wi-Fi security, enable more robust authentication, and deliver increased cryptographic strength for highly sensitive data markets. As the Wi-Fi industry transitions to WPA3 security, WPA2 devices will continue to interoperate and provide recognized security. WPA3 security continues to support the market through two distinct modes of operation: WPA3-Personal and WPA3-Enterprise. All WPA3 networks use the latest security methods, disallow outdated legacy protocols, and require use of Protected Management Frames (PMF) to maintain resiliency of mission critical networks. Key capabilities of WPA3 include:
Wi-Fi Alliance introduced enhancements and new features earlier this year for Wi-Fi Protected Access®, the essential family of Wi-Fi CERTIFIED™ security technologies, to ensure WPA2 maintains strong security protections as the wireless landscape evolves. WPA2 continues to be mandatory for all Wi-Fi CERTIFIED devices. As market adoption of WPA3 grows, the new generation of Wi-Fi security will become required for all Wi-Fi CERTIFIED devices. WPA3 maintains interoperability with WPA2 devices through a transitional mode of operation, and Wi-Fi users can remain confident they are protected when connected to secured Wi-Fi CERTIFIED networks. "WPA3 takes the lead in providing the industry's strongest protections in the ever-changing security landscape," said Edgar Figueroa, President and CEO, Wi-Fi Alliance. "WPA3 continues the evolution of Wi-Fi security and maintains the brand promise of Wi-Fi Protected Access." You can read the entire news release from the Wi-Fi Alliance here. Since this was just announced June 25, 2018, I wonder how long it will be before we a) start seeing routers supporting WPA3, and b) how long before WPA3 support comes to Linux. |