| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Berners-Lee Seeks Web Reset |
|
by Paul Arnote (parnote)  Two New Gmail Bugs ... In ONE Week! Developer Tim Cotten disclosed not one, but TWO new Gmail bugs in one week on his blog in November. The first Gmail bug was discovered when he was able to surreptitiously place items in a Gmail user's Sent folder without their knowledge. From his blog entry about the discovery on November 13, 2018: A strange thing happened to an employee today, who prudently came to me concerned their Google Apps Gmail account had been compromised by an external party. Upon questioning they explained that they had checked their Sent folder with the "in:sent" filter and discovered several emails they had no memory of sending supporting a local political party. Recognizing that this could indeed be a very legitimate threat to our corporate infrastructure we moved to diagnose and resolve as quickly as we could, and what we found was quite surprising: the emails had not been sent from her account, but were received from an external account and then filed in her Sent folder automatically. Well... kind of. Using the Linux email program mutt, coupled with sendmail, Cotten was able to send an email that was automagically filed in the recipient's Sent folder. Simply by placing the recipient's email addresses in quotes in the "From" field, the sent email appeared in the recipient's Sent folder, as if they had sent it to themselves. As he observantly and rightly points out, the RFC 2822 3.6.2 standards for email prohibit this kind of activity. This Gmail "hack" can cause considerable problems for unsuspecting users, and is ripe for exploitation. Despite due diligence by users, all it takes is one or two of these exploits to slip through the cracks -- which seem to be growing ever wider and wider -- to wreak havoc on a user's system, or even worse, across an entire network of enterprise users. Ah, but Cotten wasn't finished yet. In his November 16, 2018 blog entry just three days later, he revealed how easy it was to almost completely mask the sender's identity. To the average user, no sender appears. Hitting the "Reply" option doesn't help, either. Gmail just can't figure out what to do. Just by manipulating the "From" field to include an <img>, <script> or <object> tag causes Gmail to leave the "From" field empty, as far as the user interface is concerned. A glance at the raw email data (accessible in Gmail by selecting "Show original" from Gmail's three-dot menu on each email) will show the sender information at the end of the tag used to obfuscate the sender. But the Gmail user interface can't seem to find or parse that information. This newest Gmail bug is the worse one of the two. It gives phishing scammers a brand new vector that leverages the Gmail user interface's shortcomings. The email headers are fine and intact. But Gmail's user interface cannot properly parse that information. Cotten reported both bugs to Google, but has yet to hear back. Nope. Nothing but a chorus of crickets. Subsequently, when he reported the information on Hacker News, reports of other Gmail hacks and bugs poured in. To say the least, it makes for some interesting reading, especially if you are a Gmail user. If you were worried about the security of your Gmail account from the three and four letter government agencies, you now have even more to worry about.  Russian Hackers Targeting US, Europe With New Malware File this one under "be glad you use FOSS/Linux and open source office productivity software." New malware from Russian government-sponsored hacking groups has been spotted in circulation, according to a TechRepublic article. As you might expect, it targets Windows users in the U.S. and Europe. According to the article, the malware is being "actively distributed by Sofacy - their codename for Fancy Bear, a group also known as APT28, a hacking group which is with strong links to the Kremlin." Called Cannon, after a name reference in the malware code, it takes a screenshot of the infected user's screen every 10 seconds, and gathers full system information every five minutes. The collected information is then emailed in the background to email accounts in the Czech Republic controlled by the hackers. This latest malware sends an email about a recent current event (the one where the malware exploit was discovered was about the Lion Air crash in Indonesia). There is an attached Microsoft Word document. When the user attempts to open the document, they are told that the document was created with an older version of MS Word, and macros need to be enabled in order to view it. That starts the process for installing the malware package. To help avoid detection, the malicious code isn't activated until after MS Word has been closed. Once activated, the malicious code contacts a "command and control" server run by the attackers, and the malware is then downloaded and activated. .jpg) Web Creator Sir Tim Berners-Lee Envisions A "Web Reset" "The Web as I envisaged it, we have not seen it yet. The future is still so much bigger than the past." -- Sir Tim Berners-Lee, creator of the World Wide Web. Are you tired of Microsoft, Apple, Amazon, Google, Facebook, Twitter and all of the other big tech companies holding your personal information hostage for their own benefit? If so, you're in exquisite company. Sir Tim Berners-Lee is, too. The web -- as in World Wide Web -- that we have today is NOT the web that its creator had envisioned when it was released (freely) to the world 28 years ago. Yes, THAT "web" that permeates so many facets of our daily lives today. In fact, Sir Tim Berners-Lee says "I was devastated" in a Vanity Fair article from July, 2018, as he watched his creation become rather distorted from the vision he had when he created it. You can view the very first webpage ever, here. Berners-Lee writes on his blog: I've always believed the web is for everyone. That's why I and others fight fiercely to protect it. The changes we've managed to bring have created a better and more connected world. But for all the good we've achieved, the web has evolved into an engine of inequity and division; swayed by powerful forces who use it for their own agendas. Today, I believe we've reached a critical tipping point, and that powerful change for the better is possible -- and necessary. This is why I have, over recent years, been working with a few people at MIT and elsewhere to develop Solid, an open-source project to restore the power and agency of individuals on the web. So what are the things that have "devastated" him? Recent data breaches, spying on users, collecting user data for financial gain are some of the things that have forced Berners-Lee to attempt a "web reset" with the release of Solid. So what is Solid? Here's the description from Solid's "About" page:Solid is the technology that underpins a movement, being lead by Sir Tim Berners-Lee to re-orient the web to its original vision. To understand the ‘why' of Solid, it's important to understand the evolution of the web and how it's diverged from Sir Tim's original and inspiring vision. The first web browser was also an editor. The idea being that not only could everyone read content on the web, but they could also help create it. It was to be a collaborative space for all mankind. However, when the first browser that popularized the web came along, called Mosaic, it included multimedia and editing was taken out. It was considered too difficult a problem. This change was the first curtailing of the web's promise and spawned an effort lead by Tim and others to get the write functionality back. It was dubbed the ‘read-write web' and lead to Richard McManus' seminal article published in 2003. Solid has taken 15 years of development work to finally deliver this. The issue with writing data, as wikipedia and others have learned, is that you need a degree of control over who can write what. That means you need to have permissions - what can individuals do to the data. And to have permissions you need to have a system for identity - a way of uniquely confirming that an individual is who they purport to be. At the same time the web was always designed to be a space for data as well as documents. The Linked Data Platform group formalized this further by creating a standard for working with file systems, which when combined with the Unix philosophy form a powerful way of achieving this. These two principles, of read-write capability and managed data accessibility are key to the original and potent concept of the web. They were unfortunately lost along the way as the web evolved. Hence solid, based on existing web standards and the result of decades of work, Solid has read-write functionality, incorporating permissions and identity, along with data manageability and real-time updates via a websocket. It realizes the web as originally envisioned and provides a platform for the next generation of truly empowering and innovative applications. With Solid, USERS decide who has access to their data. USERS keep their data safe, stored in a place THEY decide. It could be in a file on your computer, or it could be on a USB flash drive. Whenever another application wants or needs your data, the USER decides who gets access and how much access. In a way, Solid is the "read-write web" that Berners-Lee envisioned 28 years ago. But it goes further than that, by empowering users with control over their data -- personal and otherwise. After suffering through endless mass data collection by companies like Google, Facebook, Apple, etc., and the data breaches that occur almost daily across the web, Solid sounds like not only ambitious, but also a HUGE breath of fresh air. FINALLY, someone has rode into the apocalyptic web landscape like a knight on a white horse. Ironically, that someone is Sir Tim Berners-Lee, the very man who invented the whole idea of the World Wide Web, to set it back on track to preserve his vision of what he set out for it to be. It's about time someone did something.  Linux Getting Two-Line Patch To Finally Deal With The Quirky Microsoft OEM Mouse Despite all of Microsoft's "love" being professed for Linux, the Microsoft OEM mouse has remained a thorn in many Linux users' side for several years. That is, until now. According to a phoronix.com article, the Microsoft OEM mouse worked just fine from Linux kernel version 2.6. But, in 2012, with kernel 3.4, something "broke." The mouse would freeze every 60-62 seconds use under level 1 or level 3. The mouse is also sold as a Dell mouse, with the model MS116. Linux identifies it as a PixArt mouse. We're not talking about some high end gaming mouse, either. This is a very, very basic USB mouse, that typically sells for between $5 and $7 (U.S.). Therein is where the problem lies. The Linux driver USBHID is responsible for managing USB devices, including USB mice. The mouse will "freeze" because it was not polled, and experienced a buffer overrun. Finally, the two line "fix" is being rolled into the Linux kernel, thanks to SUSE developer Sebastian Parschauer. It is also being backported into the series of stable Linux kernels. He also posted the issue on GitHub. If you can't wait for the fix to hit the kernel, you can also use a kernel boot option to fix the quirky behavior. Add usbhid.quirks=0x413c:0x301a:0x00000400 to your Linux boot options. The 0x413c is the vendor id (PixArt), and 0x301a is the device id. The 0x00000400 tells USBHID to always poll the device. The problem isn't necessarily unique among USB mice. Logitech and Corsair mice also needed this workaround, but they were addressed in a more timely manner. For whatever reason, the issue with the Microsoft OEM mouse was never addressed. As he states in his GitHub entry on this issue, "PixArt mice with this HW issue are known from vendors Chicony, Dell, HP, Microsoft, PixArt, and Primax." 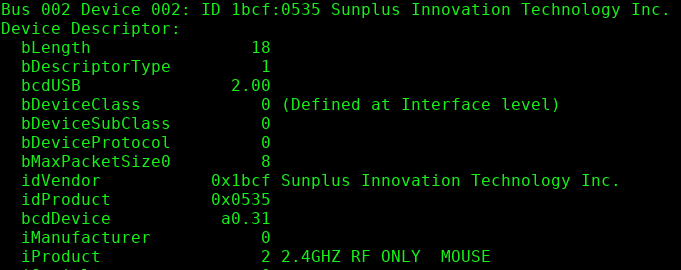 It's possible that you have another mouse from another vendor that experiences similar issues. To see the information about your mouse, open a terminal session and enter lsusb -v at the command line. Scroll through the information until you find your mouse. Write down exactly the idVendor and idProduct identifiers. Then, plug them into the usbhid.quirks kernel boot option. Using the screenshot from my own computer (above), the boot option would be usbhid.quirks=0x1bcf:0x0535:0x00000400. For what it's worth, you can chain up to four USB devices in the Linux boot option command, each separated by a comma. So now, if you have one of these basic mice lying around, you should now be able to use it without difficulties, and without it "freezing up" on the screen.  Make Your Android Phone Or Tablet Feel Twice As Fast With This "Secret" Setting If you have an Android smartphone or tablet, you know how fast the latest, greatest device becomes yesterday's news. There are new processors, new phones and new versions of Android being released all the time. Last year's top performing device will be obsolete this year. The problem is, because of their high cost, most people can't afford to upgrade their device any more often than once every two years, in most cases. So, what to do with last year's model that now feels slow? Well, the bgr.com website recently ran an article showing how to make your older Android phone feel a lot faster. Indeed, the bgr.com article was specifically about Android phones. However, I pulled out my inexpensive RCA 7-inch Android tablet, and this "trick" works with it, as well. Your mileage may vary, but I reckon that it should apply to most any fairly recent Android device. One thing that has a HUGE impact on the performance of your Android device is the speed of animations as your device transitions from one screen to another. What this "secret" setting does is double the animation speed. Your Android screen is full of animation transitions. You see them when you open an app, close an app, open or close popups, or even when you switch between apps. Fortunately, the change is very, very easy to make. Most recent versions of Android should work. Go to the Android Settings app. Select "About phone" on your Android phone, or "About tablet" on your Android tablet. Scroll down to Build number, and tap it seven times. This will enable the hidden "Developer options" menu. Yes, it is hidden from your view until you jump through these hoops. Now, go back to the top level window in the Android Settings app, and you will be greeted with the new "Developer options" menu. Select it, and scroll down to find these three items:
Next to each item, you should see a "1X" next to each of them. This means that the animations are being played at normal, 100% speed. Click on them, and you will see other options. Select the option that says ".5X" or "0.5X" from the list (be careful to NOT select "5X", which will slow your device down dramatically!). The ".5X" means that the animations will be played in half the normal time, or twice as fast. Now, you older Android phone will go from feeling sluggish to feeling brand new. If you have a newer Android phone, even if it isn't a "top of the heap" model, it may just feel as if it is.  The Linux 4.20/5.0 Kernel Is The Biggest All Year With 354+ Thousand Lines Of New Code The phoronix.com website reported that the Linux 4.20~5.0 kernel is the biggest of all year, with over 354,000 lines of code. The merge window closed on November 4, 2018, with Linus Torvalds expected to release the first release candidate either later that day, or very soon after. Despite shrinking the lines of code in the kernel by over 400,000 lines between 4.18 and 4.19 kernels, the 4.20 kernel now expands it. The reason the 4.18 and 4.19 kernels shrunk was because old architectures and staging drivers were dropped from those kernels. If you're curious about what is coming with the new 4.20 kernel, you can check here to see all the coverage phoronix.com has given to the new kernel and its new features. The new 4.20~5.0 kernel is expected to be released as stable around the end of December or in early January. |