| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Julian Assange Taken Into Custody |
|
by Paul Arnote (parnote) Don't Plug In A "Strange" USB Drive!  A friend "loans" you a USB drive. You find a USB drive, either left plugged in to a public computer, or one that has fallen from someone's pocket. Now, we've all heard it before. NEVER plug a strange USB drive into your computer. You really don't know what lurks there. But, being forever curious, that curiosity gets the best of you. Or, in hopes of finding its rightful owner, you insert it into your computer to find information that will allow you to return it to its rightful owner. Or, maybe you just want to snoop around on it and see just what's there. Now, Linux users are probably quite a bit less susceptible from malware and other malicious software than are Windows users, where programs and software can be easily installed and run without any user interaction at all, and often without the user even knowing. Conceivably, you could be putting all of your data at risk, on any platform. But, do you really want to take that chance? Apparently, the U.S. Secret Service is not immune from this, either. According to a TechCrunch article, "a Chinese national, Yujing Zhang, was caught trying to sneak into President Trump's private Florida resort Mar-a-Lago in March. The Secret Service caught her with four cell phones, a laptop, an external hard drive, a signal detector to detect hidden cameras, and a thumb drive." From the Miami Herald newspaper: Secret Service agent Samuel Ivanovich, who interviewed Zhang on the day of her arrest, testified at the hearing. He stated that when another agent put Zhang's thumb-drive into his computer, it immediately began to install files, a "very out-of-the-ordinary" event that he had never seen happen before during this kind of analysis. The agent had to immediately stop the analysis to halt any further corruption of his computer, Ivanovich said. The analysis is ongoing but still inconclusive, he testified. Reading the Miami Herald article will just boggle your mind. According to that article, a search of the suspect's hotel room discovered that she had nine USB drives, five SIM cards and other electronics, as well as over $8,000 in cash. While your initial reaction might be "what the ...," when you stop an think about it, nothing other than the signal detector screams espionage -- and even that can be explained away. When I travel, I typically have multiple USB drives, a combination of thumb drives and external hard drives. You just never know when you might need extra storage, after all. I like to backup my vacation photos so all is not lost should I have a device failure, or if my computer is stolen. I typically travel with an abundance of cash (usually traveler's checks, anyway, to protect against theft). And let's face it: the U.S. is? (or has become) a surveillance state. Heck, they will surveil you just to determine whether you have anything worth surveilling or not, and then continue to surveil you anyways, just to be sure. So it's not too far-fetched to imagine that someone traveling to the U.S. from abroad might want to have a signal detector to help them avoid the unwanted and unwarranted intrusion into their personal affairs. At any rate, take a lesson from Secret Service agent Samuel Ivanovich. DON'T plug "strange" USB thumb drives into your computer. As a Linux user, you're quite well protected from most of the malware out there. But, some USB thumb drives are capable of frying or nuking a computer. And who, after all, wants something like that to spoil their vacation, or even their ordinary day? I just hope that someday, when traveling, "security" people don't want to go through my computer gear and/or hotel room. I'm likely to be in a similar position as Yujing Zhang. Reliable, Trustworthy, Free VPN For Your Wireless Devices  In the May 2018 Short Topix column, we told you about Cloudflare's new privacy-enhanced DNS. Announced on April 1, a lot of people (including myself) thought it was a cruel April Fool's joke. But no, it was real, and I've been using it ever since. Then, on November 11, 2018 (11/11), Cloudflare released their first ever mobile app to bring the enhanced speed and security of the 1.1.1.1 DNS resolver to mobile devices. It is available through both the Apple App Store and the Android Google Play Store. This past April 1, Cloudflare announced the 1.1.1.1 + Warp program, which brings a bona fide, quality VPN to mobile devices. Warp will be free to use, but users wanting a bit more advanced version will be able to "upgrade" to Warp+, which will be available for a modest monthly fee. 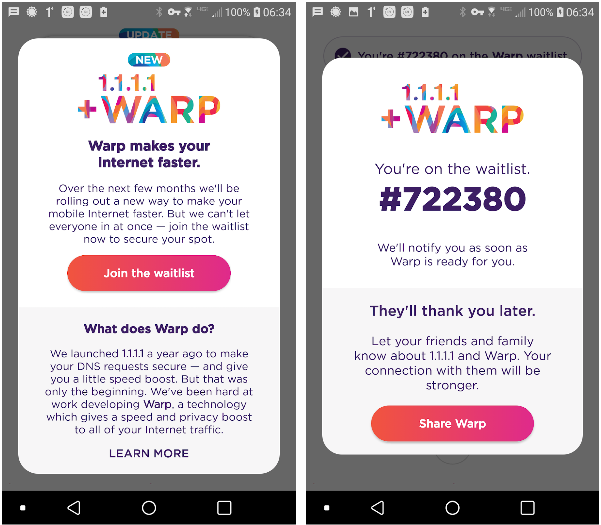 As you might imagine, there are a lot of people clamoring for exactly this kind of app, specifically designed to work with mobile devices as they transition from cellular to wifi connections and back, and which works without placing a heavy load on the mobile device's battery. Through the 1.1.1.1 app, you can join the Warp waitlist. Just click on the "Join the waitlist" button in the app. Gauging by my position on the waitlist, there are 722,379 other people who will gain access to Warp before I get the opportunity. Warp is designed to be easy to use. It is designed for people who don't even know what a VPN is, much less how to go about setting one up. Desktop users shouldn't be afraid, because Cloudflare is also working on Warp for desktop computers. You can read more about all of it on the Cloudflare blog. Julian Assange Arrested, Taken Into Custody
Julian Assange, an Australian journalist and the founder of WikiLeaks, was arrested and taken into custody April 11, 2019, after Ecuador withdrew its grant of diplomatic asylum to him. Assange had been staying in the Ecuador embassy in London since 2012, after Ecuador granted him diplomatic asylum to avoid being arrested under a warrant for jumping bail while trying to fight extradition to the U.S.
To many, Assange is a hero. To others, he is a criminal for publishing top secret or confidential documents. But, is he any different than Daniel Ellsberg, who exposed atrocities of the Vietnam War, published in the New York Times? Is he any different than Bob Woodward and Carl Bernstein, who reported on and sparked the official Watergate investigation, as reported in the Washington Post? There are many other parallels to other whistleblowers that could be made. There are many who argue that governments, to effectively represent their people and to combat corruption, must be as transparent as possible, and secretive behaviors of those governments and its officials should be minimized. Assange's fate is currently in the hands of a UK magistrate, who will determine if Assange's extradition to the U.S. will be allowed. Concerns have been voiced about Assange's continued well-being, and human rights concerns should he be extradited to the U.S. Assange has already been indicted by a U.S. federal grand jury secretively for his supposed role in the release of the documents provided by Manning. Here is a summary (PDF) of the charges that Assange has been indicted for, filed in a U.S. District Court in Alexandria, VA. Undoubtedly, there remains a lot of this story to still be written. I suspect we'll find this playing out over the next several years. Jumbo: Privacy Assistant For Facebook, Twitter, & More
Jumbo is a new privacy assistant that will help maintain your privacy on Facebook, Twitter, Google, and Amazon Alexa. Soon, it will be adding Instagram and Tinder to the list of apps that it helps maintain your privacy. Any Facebook user knows that controlling your privacy settings is a daunting experience (and just another reason among many why I refuse to have a Facebook account). From what I'm told, there isn't just one area to check to make your privacy settings. Instead, they are spread out in several different areas. Jumbo acts as your agent and goes in and makes the changes in a wholesale manner. You simply tell Jumbo if you want weak, medium or strong privacy protections. It then does the rest. For Twitter users, Jumbo lets you set how long before your tweets are deleted. You determine if Jumbo deletes your tweets that are older than a day, week, month (recommended), or three months. All deleted tweets are currently saved to Jumbo's "Memories" tab. The plans are to be able to download all of your "Memories" to either Dropbox or iCloud. At no time does Jumbo "see" your data, as all of your information is stored to your mobile device, locally. There is no server that it is sent to or synced with. Until the Dropbox and iCloud features come about, there currently is no other way to export your "Memories" from the app. If you're a prolific Twitter user, it may take a few rounds with Jumbo to delete all of your old tweets, since Twitter's API limits the number of old tweets you can delete to 3,200 every few days. On Google, Jumbo will delete your search history. For Alexa, it deletes voice recordings stored by Amazon. The ability to delete your old Instagram photos and videos, along with your old Tinder matches and chats are reported to be coming next. You can learn more about Jumbo by following the first link (which leads you to the apps home page), or by reading the TechCrunch article, here. Currently, the app is only available via the Apple App Store, but an Android version is reported to be coming soon. Brexit Equals Uncertainty For UK Tech Firms  Back in 2016, by narrow margins, British voters chose to exit the EU. The referendum became known as "Brexit." It wasn't a straight-up vote across the UK, either. Northern Ireland and Scotland voted to remain with the EU, while England and Wales voted in favor of leaving the EU. Prime Minister Theresa May delivered the order for the exit from the EU on March 29, 2017. The referendum allowed for a two year period for Britain to leave the EU, and the whole thing was to be finalized on March 29, 2019. Without getting into the why's and wherefore's, that date is now set for the end of October 2019 (as best I can tell). In the aftermath, tech firms in the UK are having difficulty attracting talent to fill the available tech jobs, thanks to the uncertainty surrounding Brexit. According to a TechRepublic article, the uncertainty stems from not knowing what form Brexit will take. More uncertainty stems from not knowing whether or not there will be a 21 month transition period after Brexit, which represents a period of time when the UK's relationship with the EU will stay largely the same as it is. That transition period is set forth in the Withdrawal Agreement negotiated by Theresa May's government and the EU. Parliament, however, has overwhelmingly rejected the Withdrawal Agreement three times. This has caused Theresa May to open negotiations with the Labour Party, who is largely in opposition to Brexit, to come up with a Brexit strategy that is agreeable to both the Labour Party and the EU. Another uncertainty for the UK tech industry is how EU data will be handled by the UK post-Brexit, and the ability to freely exchange data between the EU and UK post-Brexit. One thing that is striking fear into the UK tech industry is a no-deal Brexit, where the UK leaves the EU at the end of October without an approved formal Withdrawal Agreement. Nearly 70% of tech companies claim that a no-deal Brexit would have negative ramifications for their businesses, should it happen. To say that the entire Brexit proceedings, as well as trying to imagine a post-Brexit world, are a tangled web full of about faces and dead ends would be a gross understatement. There is a lot to ponder and consider, and having a Withdrawal Agreement in place to ease the transition certainly seems to make the most sense. Roundup At The PCLinuxOS Corral  OVER AT SLASH GEAR, they definitely make a strong case for abandoning Windows for Linux. Given Windows 10's lengthy problems with updates, Windows users could start to view the transition to Linux with greater interest. So what about Linux did they use to make a strong case for making the switch to Linux? Well, having a curated software repository, a smoother update process for programs and the OS, a choice of highly customizable desktops, being WAY more lightweight than Windows, and less data extraction. They also point out that Linux is more secure, and is nearly always FREE. If you're already a Linux user, then these are things you most likely already know. But, it will make good ammunition for getting your reticent Windows friends to finally give Linux a try. Linux Journal's very first issue featured an interview between LJ's first Publisher, Robert Young (who went on to co-found Red Hat among other things), and Linus Torvalds (author of the Linux kernel). After 25 years, they thought it'd be interesting to get the two of them together again. You can read that first interview from 1994 here. So, what's the secret to Linux's long term success? According to Torvalds, it's the open source development model. You can read the newest interview here, along with all of the clarity that 25 years of experience provides on a wide range of topics. |