| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Google, Other Tech Giants Buying Up Internet Undersea Cables |
|
by Paul Arnote [parnote]
 Yet another security flaw has been found in the "internet-browser-that-wouldn't-die-even-though-Microsoft-wishes-it-would," Internet Explorer. The last version of Internet Explorer was released in 2013, six years ago. Despite being replaced by Microsoft's newer browser, Edge, Microsoft still maintains multiple versions of Internet Explorer to support legacy applications. In fact, in the ensuing six years, even Edge has seen some significant changes, having been rebased just this year on Google's open source Chromium browser. And this security flaw is a doozy. Users could be at risk just by having it installed. The security flaw comes from MHT files, which are IE's web archive format. Windows uses IE to open MHT files, by default. But you don't even have to open IE to be affected. If you download a MHT file sent through chat or email, hackers can spy on Windows users and even steal their local data. That data can include contacts, online transactions, and other private and personal data that users are typically lax about security on. While Microsoft has said that it "will consider" a patch for the vulnerability in a future update, it isn't assured that one will be coming. Therefore, millions of Windows users are at risk until a patch is released, if it's even coming at all. So, the advice to Windows users is to either turn off Internet Explorer, or point to another program that can open MHT files. Of course, it might be wise to avoid downloading any MHT files, as well. I don't know about you, but it's things like this that make me very glad to be a PCLinuxOS user! Make Firefox More Efficient By Disabling Lazy Loading  By default, Mozilla's Firefox web browser has "lazy loading" turned on. Not sure what "lazy loading" is? Let's explain. Let's say you have a number of "pinned" tabs that are loaded when Firefox starts up. Or, let's say that you have Firefox setup to remember your open tabs when it closes, so they can all be re-displayed when Firefox is relaunched. With "lazy loading" turned on, the content of each tab is not loaded until you click on each particular tab. This initially improves Firefox's loading time, and some users are just fine with this behavior. But, some users want to work more efficiently by having the content of all tabs already preloaded when it is needed, instead of waiting for each tab to load its content. Fortunately, it's relatively easy to turn off "lazy loading." Open a new tab in Firefox, then type about:config into the address bar. Agree to "be careful" and accept the risk (if you're a long time Firefox user, you probably already know the routine), and then type browser.sessionstore.restore_on_demand on the search bar in the window that subsequently appears. The default value will be set to "true." Double click on the "true" setting to change it to "false." Close and then restart Firefox. Now, all of your tabs will load just as soon as Firefox loads, and you'll no longer have to wait for each of them to load when you click on each individual tab. Google, Other Tech Giants Buying Up Internet Undersea Cables 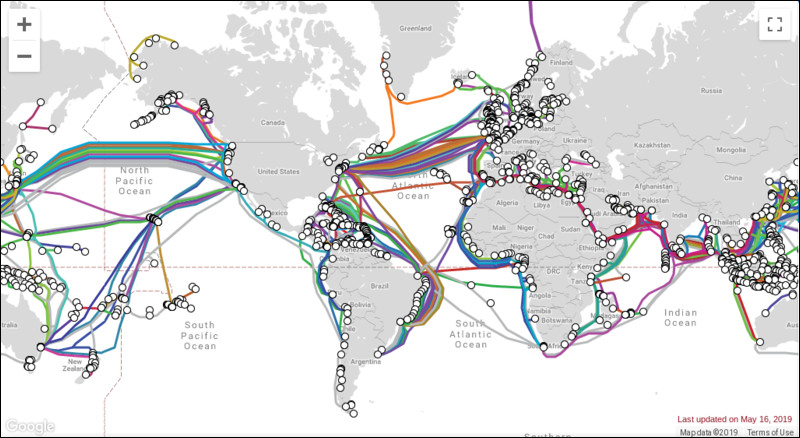 I recently read an alarming article on VentureBeat that I had never really thought about before. There are over 700,000 miles (1,147,550 km) of submarine (undersea) cables in use today. Historically, those cables have been owned by groups of private companies, comprised mostly of telecom companies. But, 2016 saw a new group jump into the submarine cable arena: content providers. Google leads the way, with the direct/whole ownership or part ownership of nearly 65,000 miles (106,560 km) of submarine fiber optic cable. That's enough submarine fiber optic cable to wrap around the Earth's equator 2.5 times, with a few thousand miles of cable to spare. This past February, Google announced plans to move forward with the Curie cable, a new 6,400 mile (10,476 km) submarine cable from Los Angeles, Calif. to Valparaiso, Chile. Google isn't alone in its pursuit of ownership of submarine fiber optic cables, either. Other tech giants are also clamoring for their share of the pie. These companies include Amazon, Microsoft, Facebook, and others. You can view an interactive map from TeleGeography of all the major submarine fiber optic cables here. The interactive map will display the owner of each cable. Just click on the cable name in the sidebar on the right side of the map. As mentioned earlier, historically these submarine cables have been owned by private telecom companies. Back when they were being installed, we didn't worry about privacy concerns. We trusted those companies, rightfully or wrongly. But now, these tech giants are buying up the literal backbone of the internet. Given their utter disregard for users' privacy and their cavalier attitude towards users' private information, well ... therein lies the concern that leads to the sense of alarm. As the owners or partial owners of these information conduits, carrying massive amounts of data, what's to prevent them from siphoning off even more of our private information that they already don't possess or respect? These tech giants have done exceptionally little to earn our trust over the years, and have behaved especially poor in recent years. Then, there's the rumors and speculation of just how much the tech giants are "in bed" with the three and four letter government spy agencies. Without a doubt, the submarine fiber optic cables are necessary not only for growth of the internet, but also for shaping the internet of tomorrow and beyond. I'm just not sure that the giant tech companies are the best caretakers/custodians of these information conduits. While I realize that this may sound like rank paranoia, or that it may make me seem like a conspiracy theorist, given their track record, they haven't given any of us enough reason to trust them with our privacy and private data. In fact, given their recent "performances" in this area, they have provided ample cause for doubt and suspicion. So not only are they sucking up our private data faster than a Hoover vacuum cleaner on steroids, they are now going to OWN the means of getting that data from point A to point B. Users would be negligent to not be concerned. G7 Countries Negotiate Tech Regulation Charter  You've heard of the G7 (Group of 7) countries, right? The group is made up of the United States, United Kingdom, Japan, Canada, France, Germany and Italy. The EU also has a representative. Started back in 1975, these countries have the seven largest advanced economies in the world. Together, they represent 58% of the global net wealth, and more than 46% of the global gross domestic product (GDP). The G7 meets at least annually to discuss economic policies. So, according to an article on TechCrunch, the digital ministers/leaders of the G7 countries met on May 15, 2019 to discuss an upcoming charter on toxic content and tech regulation at large. The plan is for the G7 member nations to sign the charter at the upcoming G7 Summit in August, to be held in Biarritz, France. Additionally, officials from Australia, India and New Zealand participated in the meeting. From the article: "Everyone has to deal with hateful content," France Digital Minister Cédric O said in a meeting with a few journalists. "This industry needs to reach maturity and, in order to do that, we need to rethink the accountability of those companies and the role of governments." One of the problems to overcome is how some countries want protections for free speech, while others are pushing for more regulation. "Hateful speech" won't be precisely defined, but a set of guidelines/principles to follow should help countries makes laws to address this issue. We'll have to wait until August to see how all of this plays out. Ransomware Holds City Of Baltimore Hostage  The city of Baltimore, Maryland had to take several of its systems offline on May 7, 2019, after their computer systems were victimized by a nasty ransomware virus, according to an article on ArsTechnica. More than two weeks later (at the time this article was written in late May), Baltimore's systems remain offline. The ransomware attack by the aggressive RobbinHood ransomware is similar to another attack in April that hit Greenville, North Carolina. The FBI, who is helping investigate the ransomware attack, have identified the ransomware as a new variant of the RobbinHood ransomware that has emerged within the past month. In the past, the RobbinHood ransomware has not been able to be spread across a network. Rather, the software typically has to be installed on each infected computer by a user with administrative access to that computer. It is spread to individual machines via a psexec system internal call, and/or by compromising the domain controller. Additionally, RobbinHood requires that a public RSA key already be present on the target computers in order to begin encryption of the computer's files. Thus, the attacker would have had to deploy the ransomware in a series of multiple steps. Here's an excerpt from the ArsTechnica article that illustrates just how nasty this ransomware is: Before it begins encryption, RobbinHood malware shuts down all connections to shared network directories with a net use * /DELETE /Y command and then runs through 181 Windows service shutdown commands--including the disabling of multiple malware-protection tools, backup agents, and email, database, and Internet Information Server (IIS) administrative services. That string of commands--which starts with an attempt to shut down Kaspersky's AVP agent--would create a lot of noise on any management system monitoring Windows systems' event logs. This isn't the first go-around for Baltimore in dealing with a ransomware attack. In March, 2018, the city's 911 system was attacked by ransomware when the city's IT department was doing some maintenance work on the city's firewall. That work briefly left a few holes in the city's firewall, which attackers found and exploited, probably by an automated scan. The firewall holes (and maintenance) were only present for about four hours before the ransomware attacked the system. It's stories like this that make you scratch your head and wonder what IT departments and CIOs are thinking by putting the operating system with the WORST security ever in charge of mission critical systems. It's stories like this that make me glad to be a Linux user. |



