| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
How To Setup DoH On Firefox, Opera, Chrome |
|
by Paul Arnote (parnote)  DNS over HTTPS (commonly referred to as DoH) has been making headlines over the past few months. Basically, it adds another "privacy cog" to the gears that make the internet go ‘round. Is it perfect? Far from it, but it's at least a start. DoH helps prevent ISPs from logging what sites you visit. Of course, there are a few other methods your ISP can utilize to figure out what sites you are visiting. Those methods, though, aren't as easy to use as merely logging the DNS address(es) that are passed between your computer and your ISP ... unencrypted. DoH fixes this glaring privacy hole by making DNS requests part of the usual HTTPS traffic. Instead of DNS requests being passed along as unencrypted plain text on port 53, it becomes a part of the encrypted traffic on port 443, which is used by HTTPS. Thus, your ISP cannot easily intercept your DNS requests by monitoring your unencrypted DNS requests coming over port 53. This allows DoH to bypass local ISP filters and access content that might have otherwise been blocked by the ISP or local governments. This led to a group of U.K. ISP's declaring Mozilla Internet Villian of the Year, 2019 "for their proposed approach to introduce DNS-over-HTTPS in such a way as to bypass U.K. filtering obligations and parental controls, undermining internet safety standards in the U.K." Of course, this is an overly simplistic explanation of how DoH works. To get a better grasp of how DoH works, I refer you to the "A Cartoon Intro To DNS Over HTTPS" article from Mozilla Hacks elsewhere in this issue of The PCLinuxOS Magazine. DoH also isn't the only game around. Another competing method, called DoT (short for DNS over TLS) has been touted by some as better and more secure. However, the emergence of DoH isn't necessarily a death blow to DoT. I suspect that DoH gained its more rapid adoption because it's easier to implement than DoT, despite DoT seeming to have a lot of supporters. I also suspect that we'll be hearing more from the DoT camp after the TLS 1.3 specs have been finalized. As a result, most of the major browsers (led by Mozilla with Firefox 70) have started implementing DoH. So, let's take a look at how to turn on DoH in Firefox, Opera and Google Chrome browsers. Yes, I know that there are other browsers; the PCLinuxOS repository has something like 20 or more browsers, including Flashpeak Slimjet, Vivaldi, Brave, and others. And no, I'm not going to review how to enable DoH on all of them. For example, I looked in Slimjet (one of the browsers I already have installed) and cannot find any DoH settings available. I already have five different browsers installed, and I'm not going to install them all just to see if they support DoH and figure out how to implement it. If you use one of those "other" browsers, you will have to visit their support forums to figure out how to turn on DoH, if it's even available or supported. Also, if you use one of those "other" browsers and discover that it does support DoH, I'd welcome you writing it up in a separate article for The PCLinuxOS Magazine to share the process with everyone else. So, let's take a look.Firefox 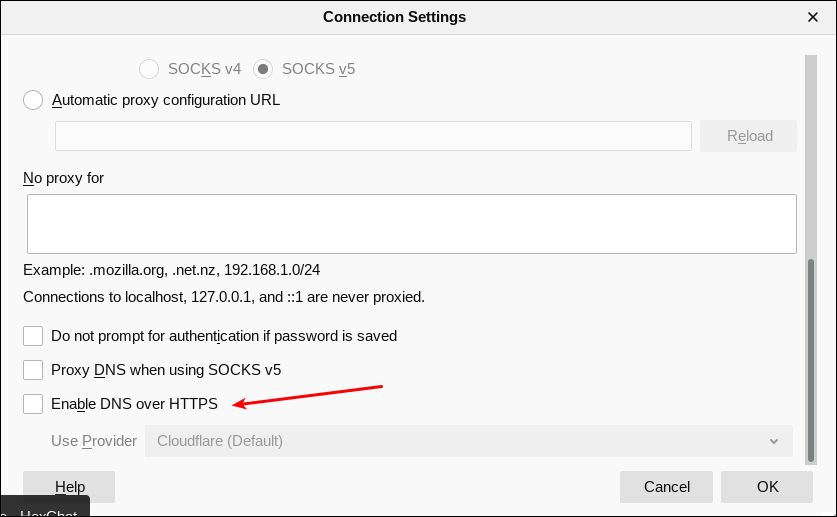 Mozilla got this whole DoH thing rolling by including the ability to enable DNS over HTTPS in Firefox 70. To enable it, Go to Firefox's Edit menu, then select Preferences. On the "General" tab, scroll all the way to the bottom, to "Network Settings." Click on the "Settings" button there. In the dialog box that appears, scroll (once again) all the way to the bottom. Place a check in the box next to "Enable DNS over HTTPS," as indicated in the image above. Once you check that box, you will be able to set whether to use the default provider (Cloudflare), or a different one. Most users will be just fine sticking with the Cloudflare choice. Mozilla partnered with Cloudflare to provide the anonymizing DNS service. Opera 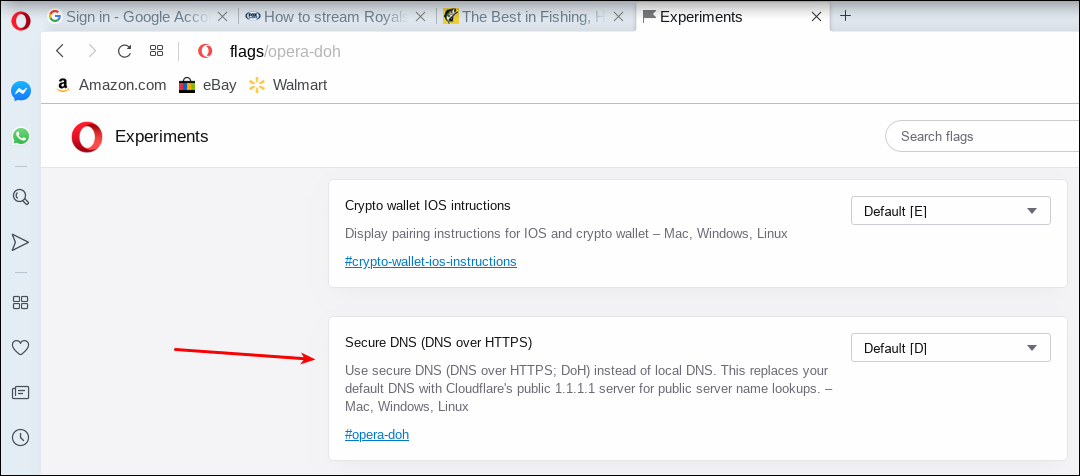 Opera has a history of going the extra mile to protect user data, so it's not surprising that it too supports DoH. To setup Opera to use DoH, follow these brief, simple steps. First, open a new tab and point it to opera://flags/opera-doh. This should bring up a whole list of experimental settings in Opera. Second, scroll down the list until you find "Secure DNS (DNS over HTTPS) in the experimental settings, like in the image above. You will find that Opera has DoH set to "Default [D]." The "[D]" means that it is turned off by default. Click on the dropdown box, and change the setting to "Enabled." Google Chrome 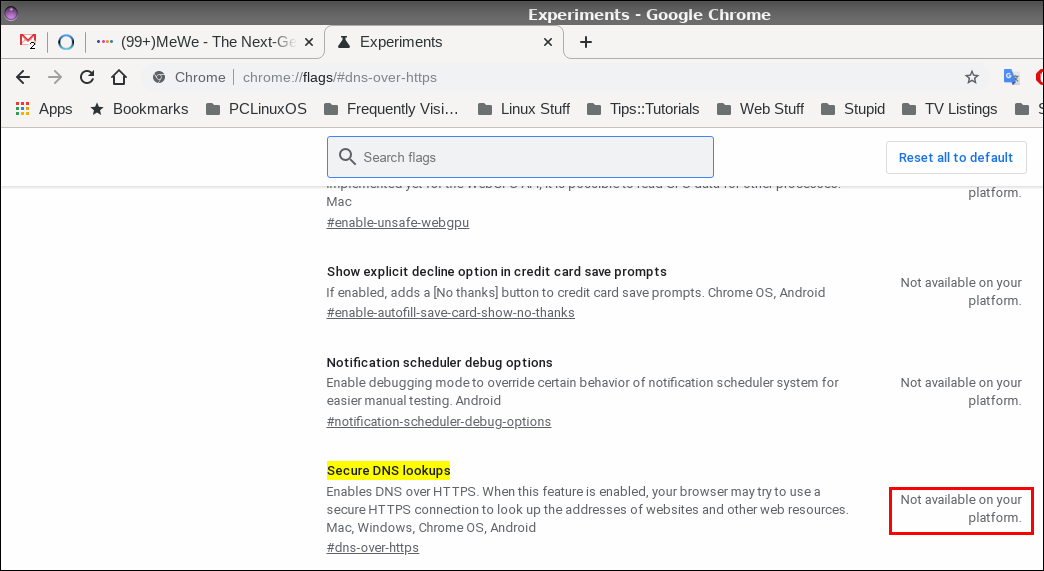 The real disappointment comes from Google, who has supposedly "signed on" to the DoH movement, touting it as an effective way to help improve user privacy on the internet. Unfortunately, the "Secure DNS lookups" setting in Google Chrome says "Not available on your platform," as highlighted by the red box in the image above. I don't know if this is yet another case of Google not adequately supporting Linux (despite using Linux to conduct their business in most every way ... same ol' shenanigans, different day), because I don't use any other platforms (Windows, Mac) to compare it against. So, for the most part, Google Chrome users can just eat dust when it comes to using DoH. It simply isn't available, at least on the Linux platform. Ha! As if I needed another reason to dislike the Chrome browser. Using DoH on Google Chrome under Linux is ... well ... just a big old DOH! Summary Of course, enabling DoH in the browser will have benefits, since most people interact with the internet mostly through their web browser. But, not everything happens in a web browser, so anything that happens outside of the web browser won't receive the encryption of DNS requests. There is, however, another alternative that is probably better than DoH, and simultaneously gives users the same protection both inside and outside of a web browser. We published a short article on Cloudflare's 1.1.1.1 DNS service in the May, 2018 issue of The PCLinuxOS Magazine. By simply replacing your DNS service with Cloudflare's DNS service, you will gain protection for all DNS requests, for all internet data. Still, 40 some years after it was originally created, DoH gives significant privacy upgrades to DNS servers. In every case that I found, DoH was NOT turned on by default. You owe it to yourself to turn it on to give you an extra layer of protection. Plus, does your ISP *really* need to know everywhere you've been on the web? It's not as if every other entity out there is trying to leech as much of your personal and private data as possible. Why make it easier for them to do so? |


