| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: New Free, Open Source AI Tool Can Fix Most Old Photos In Seconds |
|
by Paul Arnote (parnote) Assault On Your Privacy: Monthly Update  The cybersecurity firm WithSecure has identified a Facebook malware campaign, dubbed "DUCKTAIL," that targets individuals and organizations that operate on Facebook's Business and Ads platform. The malware steals browser cookies to gain access to the accounts and the private information associated with those accounts. You can read a more detailed accounting of the malware from the article on TechRepublic. Millions of Android devices are infected with "wallet-draining malware," according to an article on TechRadar Pro. The article identifies 28 Google Play Store apps. All but three of the apps have been removed from the Google Play Store, according to the TechRadar Pro article. Another article on Komando.com listed the number of infected apps as 36 in the Google Play Store. Another 17 Android apps have been caught compromising users' devices with banking malware called DawDropper, according to researchers at Trend Micro. The malware masqueraded as productivity and utility apps. Don't underestimate the importance of keeping your system up-to-date. Whether you're responsible for the maintenance of 1,000 corporate computers on a network, or just your private home network, the job is the same and requires the same amount of diligence. According to the Palo Alto Networks Unit 42 Incident Response report, hackers start looking for potential targets within about 15 minutes of a CVE (bug) being reported. According to an article on The Hacker News, North Korean hackers have deployed a malicious browser extension for Chromium-based browsers (Chromium, Google Chrome, Microsoft Edge, Brave, Opera, etc.) capable of stealing email content from Gmail and AOL. Discovered by cybersecurity firm Veloxity the malware is called SharpTongue, and it is capable of singling out individuals working for organizations in the U.S., Europe and South Korea who work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea. Apple iOS users didn't escape the past month unscathed. According to an article on Lifehacker, security researcher Alex Kleber discovered seven malware apps hiding in plain sight. While initially appearing to be by separate publishers, Kleber discovered that the malware apps were all created by a single group of hackers in China. Here's a BIG oops! With the Google Pixel 6a hitting stores, reports have emerged about ANYONE'S fingerprint being able to unlock the phone … not just the user who registered their fingerprint, according to an article on 9 to 5 Google. Still think all of those so-called "smart devices" are worth the trouble or a great idea? Well, here's an excellent exposé from Lifehacker about how all of these "smart devices" and IoT (which I've always called I(di)oT) devices sacrifice your privacy all in the name of convenience. This is what I've been saying all along. Remember that there is a literal GOLDMINE available in the reselling of your data, so it's going to be difficult (without legal or legislative restraints) to limit ANY company from profiting off of your data by selling and reselling your data to other "interested" parties … whose only interest is in serving up advertising and other tracking information. Even metadata or anonymized data, given enough of it, can paint a pretty accurate picture of a user from bits of innocent-looking data. In aggregate, it's not so innocent. THIS article deserves your attention, since the markets are now inundated by smart appliances, smart bulbs, smart thermostats, smart speakers, etc. (when I recently purchased a new thermostat for my house, the "non-smart" thermostats were buried on the retailer's website, and harder to find than they should have been). Scary, scary times ahead concerning privacy! According to an article on BleepingComputer, another batch of 35 malware apps has been found in the Google Play Store. This latest batch of malware has been installed more than 2,000,000 times. Research from cybersecurity provider Kaspersky found nearly 7 million users being affected by unwanted software disguised as browser add-ons, with many being found on Google Chrome. As reported, 4.3 million unique users were attacked by adware sneaking their way onto systems, while over 2.6 million users were affected by malware, according to an article from Laptop Mag. "Bad actors" have been discovered creating false Google Ads in an effort to deliver malware to your computer, according to an article from Lifehacker. The "malvertising" disguises itself as a bona fide Google Ad to lure unsuspecting/less savvy users to a fake version of the site that's being searched for. We all knew ads were bad, but now they are even worse. If you haven't changed to Bitwarden to help manage your online passwords, you may want to after hearing this. LastPass, one of the world's largest password managers, has confirmed on a blog post that it has been hacked, according to an article on Forbes. LastPass, which recently switched from a free service to a fee-based subscription service, has about 25 million users. While user data was never compromised, the hackers did gain access to some proprietary LastPass technical information, and gained access to some portions of source code. Mystery Solved: What Does Wi-Fi Stand For?  Here's a debate that has raged for years: what does Wi-Fi actually stand for? If you (like many others) say "wireless fidelity," you would actually be… wrong. It's actually a trick question. The name "Wi-Fi" actually doesn't mean anything. Instead, it's a meaningless marketing term.
Writes Phil Belanger, a founding member of the Wi-Fi Alliance who presided over the selection of the name "Wi-Fi" in a 2005 BoingBoing article by Cory Doctorow:
Wi-Fi doesn't stand for anything.
It is not an acronym. There is no meaning.
Wi-Fi and the ying yang style logo were invented by Interbrand. We (the founding members of the Wireless Ethernet Compatibility Alliance, now called the Wi-Fi Alliance) hired Interbrand to come up with the name and logo that we could use for our interoperability seal and marketing efforts. We needed something that was a little catchier than "IEEE 802.11b Direct Sequence". Interbrand created "Prozac", "Compaq" "oneworld", "Imation" and many other brand names that you have heard of. They even created the company name "Vivato".
The only reason that you hear anything about "Wireless Fidelity" is some of my colleagues in the group were afraid. They didn't understand branding or marketing. They could not imagine using the name "Wi-Fi" without having some sort of literal explanation. So we compromised and agreed to include the tag line "The Standard for Wireless Fidelity" along with the name. This was a mistake and only served to confuse people and dilute the brand. For the first year or so( circa 2000) , this would appear in all of our communications. I still have a hat and a couple of golf shirts with the tag line. Later, when Wi-Fi was becoming more successful and we got some marketing and business people from larger companies on the board, the alliance dropped the tag-line.
This tag line was invented after the fact. After we chose the name Wi-Fi from a list of 10 names that Interbrand proposed. The tag line was invented by the initial six member board and it does not mean anything either. If you decompose the tag line, it falls apart very quickly. "The Standard"? The Wi-Fi Alliance has always been very careful to stay out of inventing standards. The standard of interest is IEEE 802.11. The Wi-Fi Alliance focuses on interoperability certification and branding. It does not invent standards. It does not compete with IEEE. It complements their efforts. So Wi-Fi could never be a standard. And "Wireless Fidelity" – what does that mean? Nothing. It was a clumsy attempt to come up with two words that matched Wi and Fi. That's it.
So we were smart to hire Interbrand to come up with the name and logo. We were dumb to confuse and water down their efforts by adding the meaningless tag line. Please help reinforce the good work that we did and forget the tag line.
New Free, Open Source AI Tool Can Fix Most Old Photos In Seconds   A new and open source AI model can now "fix" most old photos in just seconds … for free! With the new GFP-GAN (Generative Facial Prior-Generative Adversarial Network) tool, old photos can be fixed to provide a much more lifelike appearance. Not only does the new process work for old photographs where the colors are faded, but it can also take a black and white photo and colorize it. The real "magic" of the tool comes in the reconstruction of damaged areas of a photograph. 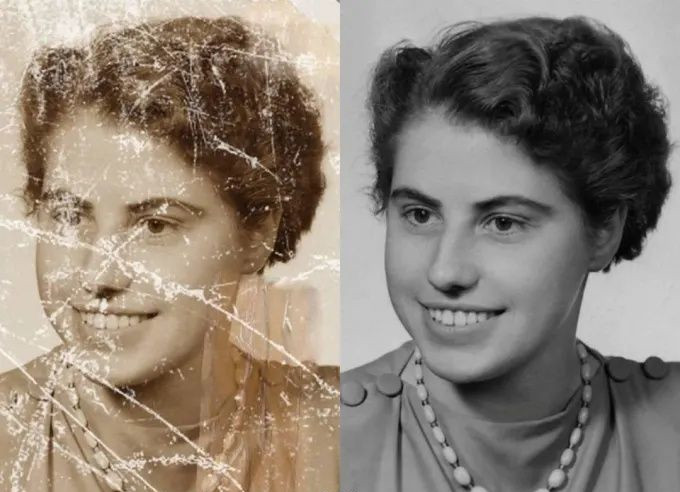
Can you imagine trying to repair the above image on the left? The new AI tool created the image on the right in just a matter of seconds. It would literally take HOURS to try to repair all of that damage, and the results would not look as good as the results from the AI tool. If you want to read all of the nitty-gritty about the new AI tool, head on over to Louis Bouchard's home page where he describes the process. He has also created a YouTube video about the process, which you can view here. If you want to take a DEEP dive into the internals of how this whole process works, you can check out the PDF study paper. Finally, don't hesitate to check out the GitHub page, where you can find the software libraries and a working demo for this new tool. Concerned About How To Protect Your Online Privacy? Read On…  Increasingly, users of online services are concerned about their privacy. And, gauging by the ongoing monthly section of this article highlighting assaults on user privacy, users have good reason to be concerned. According to a TechRepublic article, 85% of Android users are concerned about privacy … or their ongoing lack thereof. What's worse is that it's like trying to navigate through a virtual minefield, with all of the different apps with different privacy settings, and with each app's privacy settings in different places and covering/offering different levels of protection. Kaspersky, one of the leaders in antivirus/anti-malware software, has an online privacy checker site. While it doesn't cover Linux, it does cover Windows, MacOS, iOS and Android… and lots of Linux users have/use those platforms as well. 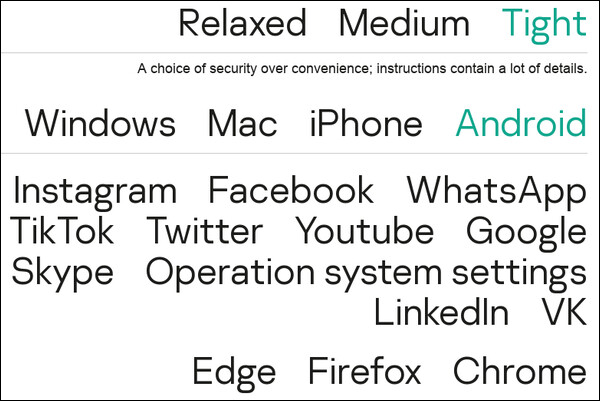 As you can see in the screenshot image above, users can choose between relaxed, medium or tight security. The "relaxed" setting prioritizes convenience over security, while the "medium" setting tries to strike a balance between convenience and security. Selecting the "tight" setting emphasizes security over convenience, and comes with LOTS of detailed instructions on how to achieve a level of heightened security. Users then choose which app(s) they are wanting greater security/privacy with, and then the browser they use most. What I find most ironic from looking at the list of apps that it helps users manage privacy settings on, is that most of the apps listed are literal sieves when it comes to user privacy in the first place. Couple that with Edge or Chrome, and you have a privacy nightmare that's nearly impossible to navigate successfully. Still, the site offers a roadmap to many privacy settings that are most often obfuscated or obscured by being buried so deeply. The ultimate solution is to avoid using these apps altogether, if possible. But, barring that abstinence, the recommendations from the Kaspersky Online Privacy Checker is a good place to start. As a bonus, Kaspersky also offers an online password checker further down on the page. With it, you can see how many years it might take a supercomputer to break/hack your secure password. You are using a secure password, right? You aren't using the same password on multiple sites, right? Ahmm! Two Astrophotographers Team Up, Create Highest Resolution Photo Of Moon Ever  Two astrophotographers teamed up to create two of the most detailed images ever taken of the moon, according to an article from NPR (check out the New York Post article for even more information). It took over 500 images to capture the subtle colors of the moon, and was assembled using a technique called photo stitching. The black and white image was made from 200,000 separate images, also assembled using photo stitching. That effectively made the black and white image a 174 megapixel image, with the most astounding detail ever recorded in an image of the moon. The image above is called "The Hunt For Artemis," paying homage to the upcoming Artemis I mission. That mission will launch three test dummies into orbit around the moon to test out NASA's new moon launch vehicle, before returning to Earth for a splashdown in the Pacific Ocean. Artemis III is scheduled for the first live crew launched to the moon since Apollo 17 in 1972, and should occur in 2025. New Vulnerability Found In Linux Kernel, Previously Unknown DirtyCred is a kernel exploitation concept that swaps unprivileged kernel credentials with privileged ones to escalate privilege. Instead of overwriting any critical data fields on kernel heap, DirtyCred abuses the heap memory reuse mechanism to get privileged. Although the concept is simple, it is effective, reports the GitHub page about the vulnerability. From the description of the talk presented by researchers at the 2022 Blackhat hacking conference: Dirty pipe is the name given to the CVE-2022-0847 vulnerability, present in Linux kernel versions 5.8 and later. It is considered a very serious vulnerability found in the Linux kernel recently partially because it gives a bad actor the ability to escalate privilege but more importantly, its exploitation has no headache in dealing with kernel address randomization and pointer integrity check. With this capability, the exploit built on top of the dirty pipe could be easily used for all versions of kernel affected without even modification. While dirty pile is powerful, its exploitability is closely tied to the capability of the CVE-2022-0847 vulnerability which abuses the Linux kernel pipe mechanism to inject data to arbitrary files. For other vulnerabilities without such a pipe-abusive power, the exploitation is still hard to follow the dirty pipe journey and thus brings the same level of security implication. In this talk, we present a novel exploitation method pushing the dirty pipe to the next level. To be specific, given a vulnerability with a double-free ability, we will demonstrate that our exploitation method could obtain the dirty-pipe-like ability to overwrite an arbitrary file to escalate privilege. Exploits utilizing our method inherit the advantage of the dirty pipe that the code would work on any version of the kernel affected without modification. We argue that our new exploitation method is not only more general than the dirty pipe but also more powerful. First, rather than tying to a specific vulnerability, this exploitation method allows any vulnerabilities with double-free ability to demonstrate dirty-pipe-like ability. Second, while it is like the dirty pipe that could bypass all the kernel protections, our exploitation method could even demonstrate the ability to escape the container actively that dirty pipe is not capable of. Along with this talk, we will demonstrate how our exploitation method works using real world vulnerabilities. Specifically, we will demonstrate privilege escalation on Linux and Android. Last but not least, we will demonstrate how to achieve container escape on CentOS. We will release our exploitation details and all of our exploits demonstrated in this talk. To the best of our knowledge, our exploitation is the first general method that helps develop a universal exploit to different versions of kernel and different architectures. It greatly unloads the burden of exploit migration across versions and architectures. Since our exploitation is general and powerful, it also imposes a great challenge to the existing kernel defense architecture. The vulnerability exists for all major distros, and has been compared to the previous Dirty Pipe vulnerability, which has been patched. As of the time of this article, the new vulnerability has not yet been patched. It can allow local users to gain root privileges. Messin' With Mother Nature: The Return Of The Wooly Mammoth  According to an article from The Independent, a Texas startup is attempting to use genetic engineering to bring back the extinct wooly mammoth. As you can imagine, this attempt has sparked all kinds of ethical discussions. Wooly mammoths last walked the Earth with humans over 3900 years ago, going extinct just after the last ice age. Since then, no human has ever laid eyes on a living mammal of such size. Then, wooly mammoths were a valuable food source for humans. The company is touting how good wooly mammoths might be for a healthier planet. The animal's massive weight will help keep the permafrost compacted, which helps to prevent it from melting, and thus keeping greenhouse gasses sequestered in the frozen mix. Of course, others are asking other questions. Since wooly mammoths provided a significant food source for humans, will we find wooly mammoth meat making its way into our grocery stores? NASA Awards Next-Generation Spaceflight Computing Processor Contract  NASA's Jet Propulsion Laboratory has selected Microchip Technology Inc. to develop a high-performance spaceflight computing processor that will support future space missions. Credits: NASA NASA's Jet Propulsion Laboratory in Southern California has selected Microchip Technology Inc. of Chandler, Arizona, to develop a High-Performance Spaceflight Computing (HPSC) processor that will provide at least 100 times the computational capacity of current spaceflight computers. This key capability would advance all types of future space missions, from planetary exploration to lunar and Mars surface missions. "This cutting-edge spaceflight processor will have a tremendous impact on our future space missions and even technologies here on Earth," said Niki Werkheiser, director of technology maturation within the Space Technology Mission Directorate at NASA Headquarters in Washington. "This effort will amplify existing spacecraft capabilities and enable new ones and could ultimately be used by virtually every future space mission, all benefiting from more capable flight computing." Microchip will architect, design, and deliver the HPSC processor over three years, with the goal of employing the processor on future lunar and planetary exploration missions. Microchip's processor architecture will significantly improve the overall computing efficiency for these missions by enabling computing power to be scalable, based on mission needs. The design also will be more reliable and have a higher fault tolerance. The processor will enable spacecraft computers to perform calculations up to 100 times faster than today's state-of-the-art space computers. As part of NASA's ongoing commercial partnership efforts, the work will take place under a $50 million firm-fixed-price contract, with Microchip contributing significant research and development costs to complete the project. "We are pleased that NASA selected Microchip as its partner to develop the next-generation space-qualified compute processor platform." said Babak Samimi, corporate vice president for Microchip's Communications business unit. "We are making a joint investment with NASA on a new trusted and transformative computer platform. It will deliver comprehensive Ethernet networking, advanced artificial intelligence/machine learning processing and connectivity support while offering unprecedented performance gain, fault-tolerance, and security architecture at low power consumption. We will foster an industry-wide ecosystem of single board computer partners anchored on the HPSC processor and Microchip's complementary space-qualified total system solutions to benefit a new generation of mission-critical edge compute designs optimized for size, weight, and power." Current space-qualified computing technology is designed to address the most computationally-intensive part of a mission – a practice that leads to over-designing and inefficient use of computing power. For example, a Mars surface mission demands high-speed data movement and intense calculation during the planetary landing sequence. However, routine mobility and science operations require fewer calculations and tasks per second. Microchip's new processor architecture offers the flexibility for the processing power to ebb and flow depending on current operational requirements. Certain processing functions can also be turned off when not in use, reducing power consumption. This capability will save a large amount of energy and improve overall computing efficiency for space missions. "Our current spaceflight computers were developed almost 30 years ago," said Wesley Powell, NASA's principal technologist for advanced avionics. "While they have served past missions well, future NASA missions demand significantly increased onboard computing capabilities and reliability. The new computing processor will provide the advances required in performance, fault tolerance, and flexibility to meet these future mission needs." Microchip's HPSC processor may be useful to other government agencies and applicable to other types of future space missions to explore our solar system and beyond, from Earth science operations to Mars exploration and human lunar missions. The processor could potentially be used for commercial systems on Earth that require similar mission critical edge computing needs as space missions and are able to safely continue operations if one component of the system fails. These potential applications include industrial automation, edge computing, time-sensitive ethernet data transmission, artificial intelligence, and even Internet of Things gateways, which bridge various communication technologies. In 2021, NASA solicited proposals for a trade study for an advanced radiation-hardened computing chip with the intention of selecting one vendor for development. This contract is part of NASA's High-Performance Space Computing project. HPSC is led by the agency's Space Technology Mission Directorate's Game Changing Development program with support from the Science Mission Directorate. The project is led by JPL, a division of Caltech. PCLinuxOS Magazine Short Topix Roundup  Linux creator Linus Torvalds has announced the first release candidate for the Linux kernel version 6.0, but he says the major number change doesn't signify anything especially different about this release, according to an article on ZDNet. Have you ever dropped your cell phone into water? If so, you may have thrown out the very thing that could possibly save your phone, according to an article from ZDNet. The article recommends saving those "non-edible" chiclet bags of silica gel that come in pairs of new shoes, electronic devices, and many other things. Place them and your drenched phone in an airtight container … then wait a few days. They might just resurrect your drenched device(s) and buy you some time. Buy you some time? Yes, because you will still have to deal with the corrosion from the liquid you dropped your device(s) into, but that will be somewhere down the road. It should be common knowledge by now, but Google uses a homegrown version of Linux on its thousands of workstations at its offices. Known as gLinux, it's based on Debian, which has longer LTS support than the initial Goobuntu version (can you guess what that was based on?) that they started with. Ubuntu's LTS support is pretty much limited to two years. With the thousands of computers to keep up-to-date, that would make updating a full-time job before you have to start all over again. If you want to know more about gLinux … the version of Linux you will never be able to use "in the wild," check out the article on Computerworld. The internet has been built on the back of TCP connections. TCP stands for Transmission Control Protocol, and has been entrenched as the standard for the past 40 years. But according to an article from The Register, while cutting edge for its time at the time of its introduction, TCP doesn't work as well for modern data centers. For that, Homa was conceived (PDF). Homa has the potential to speed things up by 100X over the speed of TCP. The James Webb Space Telescope keeps breaking its own records, according to an article on Space.com. Sifting through the data returned thus far, astronomers are now able to see distant galaxies as they existed 200 million years after the Big Bang. Previously, they could only see galaxies as far back as 480 million years after the Big Bang. NASA's DART mission will purposefully crash an unmanned space probe into an asteroid (Dimorphos) as a demonstration of its plan to divert or otherwise change the course of an asteroid that might be on an Earth trajectory, according to an article on LiveMINT. DART stands for Double Asteroid Redirection Test. The demonstration will take place on September 26, 2022, and will be aired on NASA TV and the space agency's website. |