| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Vulnerability Discovered Masquerading As Gnome Extension |
|
by Paul Arnote (parnote) Mozilla, Firefox Branded "Internet Villains"  On July 2, 2019, the U.K.'s Internet Service Providers' Association (ISPA) announced their candidates for Internet Hero of the Year, as well as their candidates for Internet Villain of the Year. Amazingly, Mozilla/Firefox was listed among the "villains." Here is a snippet from their announcement: Mozilla -- for their proposed approach to introduce DNS-over-HTTPS in such a way as to bypass UK filtering obligations and parental controls, undermining internet safety standards in the UK.So, what is DNS-over-HTTPS? Well, according to Wikipedia, DNS over HTTPS (DoH) is a protocol for performing remote Domain Name System (DNS) resolution via the HTTPS protocol. A goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle attacks. Typically, DNS information is passed between computers in an unencrypted state. Because of this, users can be more easily tracked, and their actions monitored. According to a TechCrunch article, under the law in the U.K., websites can be blocked for facilitating the infringement of copyrighted or trademarked material, or if they are deemed to contain terrorist material or child abuse imagery. By encrypting DNS queries, it's claimed that it will make it more difficult for internet providers to filter their subscribers' internet access The ISPA isn't alone. U.K. spy agency GCHQ (the U.S. NSA's U.K. brethren) and the Internet Watch Foundation, which maintains the U.K.'s internet blocklist, have criticized the move to roll out encrypted DNS features to the browser. Really? This is what you get when you have ISPs caught between protecting user privacy and policing users to remain in compliance with heavy handed government regulations. Any reasonable person would expect that user privacy would be front and center. But then again, if they do not remain in compliance with the heavy handed government regulations, they won't be in business any longer either. So, in effect, it is a Catch-22, a complete "damned-if-you-do, damned-if-you-don't" situation. Mozilla isn't the first to implement DoH. Cloudflare has been offering DoH since April, 2018 with their 1.1.1.1 DNS service. We first told you about it here, in the May, 2018 issue of The PCLinuxOS Magazine. Millions of users are currently waiting for Cloudflare to roll out its recently announced forthcoming VPN service, so there is little doubt that users are clamoring for improved internet security. More Than 1,300 Android Apps Circumvent Permissions  According to a multinational research document (PDF) from the International Computer Science Institute, called "50 Ways to Leak Your Data: An Exploration of Apps' Circumvention of the Android Permissions System," 1,325 Android apps circumvent the permissions granted to them by users. They looked at 88,000 popular apps from the Google Play store, across all categories. You would think that once a user denies or grants specific permissions to an app, that would be the end of the discussion. But ... Noooooo! Many of the 1,325 apps either continued on as if the user never denied permissions (such as access to location data, WiFi, contacts, camera, etc.), or just piggy-backed their data extraction from other legitimate apps that were given permissions. The information was presented to the attendees of the Federal Trade Commission's PrivacyCon in late June, 2019, after being reported to both Google and the FTC in September, 2018. One app that was used as an example in the report was the Shutterfly app. Even after permissions for location sharing were denied, GPS coordinates for individual photos were still uploaded to Shutterfly's servers, and stored there. You will be in for quite a surprise if you look at the EXIF data from photos taken with your phone's camera. From the report: We observed that the Shutterfly app (com.shutterfly) sends precise geolocation data to its own server (apcmobile.thislife.com) without holding a location permission. Instead, it sent photo metadata from the photo library, which included the phone's precise location in its exchangeable image file format (EXIF) data. The app actually processed the image file: it parsed the EXIF metadata--including location--into a JSON object with labelled latitude and longitude fields and transmitted it to their server. While this app may not be intending to circumvent the permission system, this technique can be exploited by a malicious actor to gain access to the user's location. Whenever a new picture is taken by the user with geolocation enabled, any app with read access to the photo library (i.e., READ_EXTERNAL_STORAGE) can learn the user's precise location when said picture was taken. Furthermore, it also allows obtaining historical geolocation fixes with timestamps from the user, which could later be used to infer sensitive information about that user. Yessiree. Encoded within each photo taken with your cellphone's camera is the exact GPS coordinates within the EXIF data that is stored in the JPG files detailing exactly where that particular photo was shot. It won't show up if you just look with the EXIV2 command line tool, which seems to promote itself as an enhanced EXIF tool. You must look with the EXIF tool, specifically. Install the EXIF tool from the PCLinuxOS repository, and (from a normal command line), run exif -m yourphoto.jpg. You're likely to be as surprised as I was. To be totally honest, I had never really given it any thought before that my photos taken with my cellphone's camera contained geolocation information that virtually anyone could access. But the Shutterfly app wasn't just guilty of uploading the EXIF information that's stored in the header of each JPG file. Nope. The Shutterfly app specifically extracted the GPS data (along with other EXIF data) and uploaded a JSON object to the Shutterfly servers. While Shutterfly isn't using this information for nefarious or evil purposes, it perfectly illustrates a vulnerability that most users won't even have a cursory or glancing thought about. Google has responded to the report, and said that these issues will be addressed (at the earliest) in Android Q, which is due to be released later this year. Vulnerability Discovered Masquerading As Gnome Extension  CAUTION! There is a new vulnerability for Linux masquerading as a GNOME shell extension. Fortunately for PCLinuxOS users, the incidence should be miniscule, due to the fact that GNOME isn't one of the desktops offered on PCLinuxOS. I first saw this reported on BleepingComputer.com, stumbling upon subsequent articles on OfficialHacker.com and TheHackerNews.com. What makes things worse is that it is NOT detected by any of the major virus scanners. Called EvilGnome, it's installed as a self-extracting archive, camouflaging itself as a GNOME shell extension. Once installed, it sets up cron jobs that take screenshots of the user's computer, captures audio from the user's microphone, and looks for newly created files on the user's computer. It then sends that gathered data to the owner's command-and-control server. It can also ping the owner's server, and download and execute additional payloads. The malware also contains an uncompleted and yet-to-be-implemented keylogger. EvilGnome has been linked back to a Russian threat group, known as Gamaredon Group. They are an active and persistent threat group that has been around since 2013. Since it has thus far evaded the major virus checkers, just how do you know if you've been compromised? Fortunately, that's fairly easy. Take a look in ~/.cache/gnome-software/ gnome-shell-extensions, and look for the "gnome-shell-ext" executable. If you don't find it, then you're in the clear. The malware stores its collected data in the ~/.cache/gnome- software/gnome-shell-extensions/tmp/ folder on infected Linux computers. EvilGnome connects to its command-and-control servers via SSH, over port 3436. This newest exploit perfectly makes the case for how dangerous it is to download and install software from outside of the official PCLinuxOS repository. By sticking to the official offerings in the PCLinuxOS repository, you virtually eliminate the possibility of becoming one of its victims. LightSail 2 Set To Prove Value Of Solar Sails 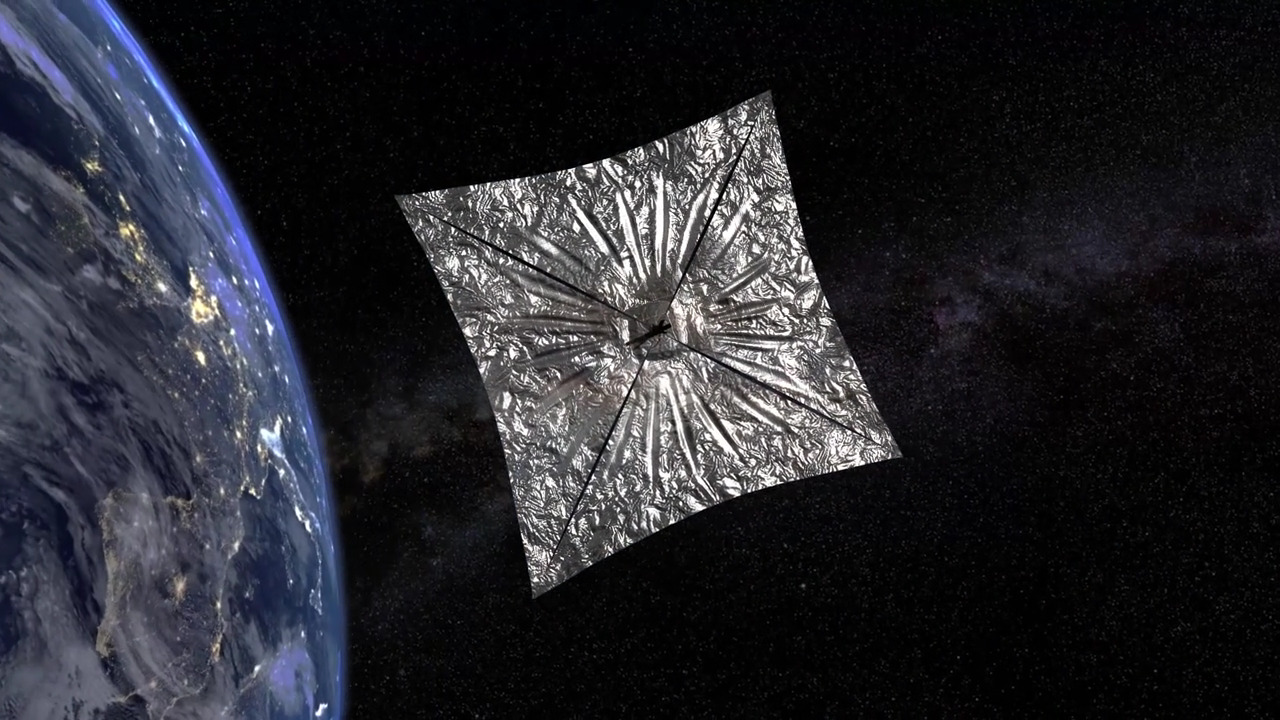 The Planetary Society launched a small cubesat on June 25, 2019, from a Falcon Heavy rocket that launched from Kennedy Space Center in Florida. The satellite was deployed July 2, 2019 from another satellite that was designed by Georgia Tech students. The solar sail was successfully deployed on July 23, 2019. Roughly thirty days after deployment of the solar sail, the mission plan is to raise the satellite's orbit using the solar sail as the only propulsion. Solar sails work by using only the impact of the Sun's photons upon the surface of the extended sail material. LightSail is a crowd-funded venture (raising over $1 million with a KickStarter campaign) that sets out to prove the value and usefulness of using solar sails as the sole propulsion source of small cubesat satellites. The Planetary Society has advocated for the use of solar sails for decades. They found their first practical success in 2005 with the launch of Cosmos 1, a solar sailing spacecraft. However, it was lost due to a rocket failure. In 2015, LightSail 1 successfully completed its test flight, paving the way for this current endeavor. Anyone with an internet connection can follow along with LightSail 2's progress by visiting its Mission Control Center. The Planetary Society, under the leadership of CEO Bill Nye (yes, THAT Bill Nye, of television fame from the Bill Nye The Science Guy fame), is the world's largest and most influential non-profit space organization. The organization is supported by over 50,000 members in over 100 countries, and by hundreds of volunteers around the world. Mad Magazine Closes Shop After 67 Years  After 67 years, MAD Magazine is essentially closing down. Well, not completely, but at least in a very significant way compared to how we have come to know them. Alfred E. Neuman and company's monthly satirical review will sell its last monthly magazine on newsstands in August, 2019. Started in 1952, the magazine features irreverent, satirical humor targeting current events and societal trends. Nothing is or was sacred. They even often poked fun at themselves. Along the way, it has wielded significant influence in helping either fuel the current debate(s), or shaping the debate in a different light. But, in today's culture where runaway, rampant political correctness rules the discussions, it seems many people can't take a joke or see the humor in many topics of the day. Starting with 2019's issue 10, it will only be available in comic book shops, and mailed to subscribers. Starting with 2019's issue 11, there will no longer be any new content, except for end-of-the-year specials. From issue 11 onward, they will only feature previously published content, drawn from its massive vault of material gathered from the past 67 years. DC Comics, however, will continue to publish MAD books and special collections. Although it started out as a comic book, it quickly changed its format to a bimonthly magazine. Its covers, featuring Alfred E. Neuman with his gap-toothed smile, were eagerly anticipated by its fans. It was very influential for successive generations of comedians, writers, artists and performers. With the state of the world being what it is, we need the irreverent and satirical humor of MAD Magazine more than ever. It's saddening that such a publication will be closing up shop. We need you A. E. Neuman, more than ever! Are Notifications On Google Maps Driving You Crazy On Your Android Device?  If you use Google Maps on iOS, you won't have this problem; for some reason, iOS users are immune from this problem. But, if you use Google Maps on an Android device, this problem is enough to DRIVE. YOU. CRAZY. There are 54 different notifications for Google Maps, and by default, they are ALL turned on. Oh, yay! What a treat for users of Google's own OS! These notifications from Google Maps can quickly overwhelm users. At minimum, they crowd out more important notifications, becoming more of an annoyance than being helpful. You could tap on the hamburger menu at the left upper corner of the Google Maps window, select Settings, then Notifications, and then begin to plow through all of the notifications that Google Maps has turned on. If you choose this route (or forced to because of the version of Android you use), be prepared for an arduous journey through "notification hell." Many of the notifications are obscurely described, so you may never be sure if they are turning off something helpful, annoying, or that doesn't even apply to you and your life. You'd probably have better odds playing craps at the local casino. But, if you use Android 9 Pie, there is an easier and faster way to turn off whole groups of notifications. By turning off whole groups of notifications, you don't have to wade through each and every one of the 54 different notifications. To accomplish this, follow the steps below. First, "long press" the Google Maps icon. Second, in the little window that pops up, click on the "information" icon near the top. It looks like an "i" with a circle around it, a lot like a copyright or trademark symbol. This will take you directly to the "app info" screen. Third, tap on "Notifications" in the "app info" screen. Fourth, and lastly, you should find all of the notifications divided up into categories. This makes it much easier to turn off entire groups of notifications that you don't want to be bothered with. For example, I never use public transportation, so that whole group of notifications was a no-brainer for me. Another one for me was Google Maps telling me, every morning when I go to work, how many minutes it will take to get there. Uhm ... that never, ever changes, and it's just a nuisance notification. So those types also got turned off, too. Now, I'm hoping that I'm feeling a lot less "love" from Google Maps. I've tested this, and it does work (I'm running Android 9 Pie, on a Google Pixel 3 phone). The nice thing about using this method is that if you turn off notifications that you find useful, you can repeat the steps above to turn them back on. |